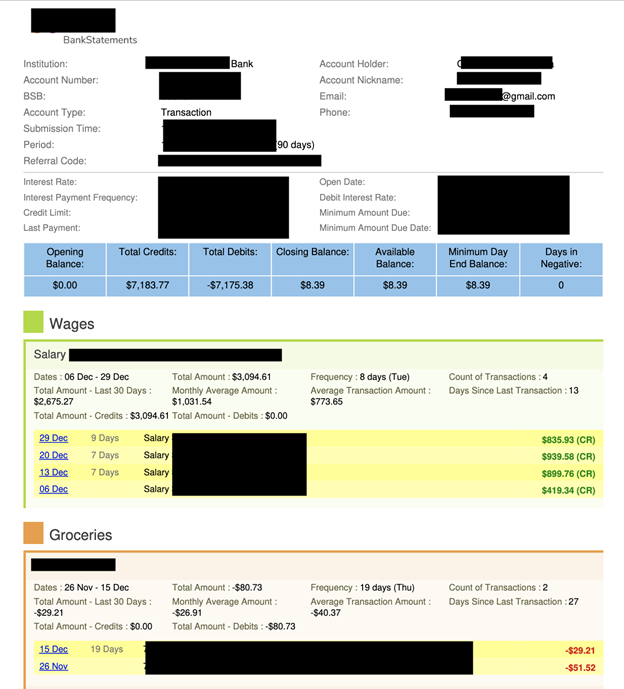
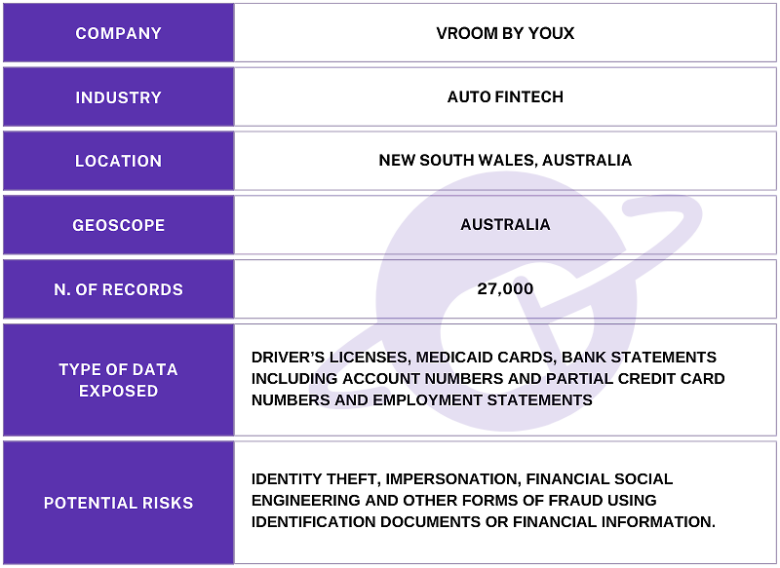
 The publicly exposed Amazon S3 database was not password-protected or encrypted. It contained 27,000 records, including driver’s licenses, medicaid cards, employment statements, and bank statements that contain account numbers and partial credit card numbers. The name of the database and its internal files indicated they belonged to Australian Fintech company Vroom by YouX (formerly Drive IQ).
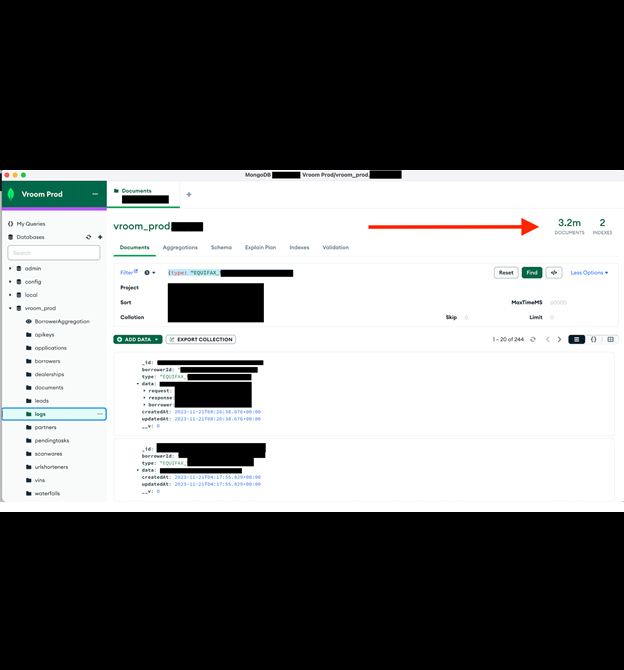
Additionally, I saw an internal screenshot that showed the information of an additional MongoDB storage instance that contained 3.2 million documents. I did not review the MongoDB, and it is unknown for me if those files were accessible or secured, but there are numerous potential risks to exposing additional file storage locations, database names, and systems that are intended for internal use. When cybercriminals know where internal data is stored, it could possibly become an additional attack vector or backdoor deeper into a network.
I immediately sent a responsible disclosure notice to Vroom, and the database was restricted from public access and no longer accessible shortly after. It should be noted that AWS S3 is a key-value store, and S3 is effectively considered to be a NoSQL database, which is why I reference “database” in this report. Although the records belonged to Vroom by YouX, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I received a response the following day stating: “We’ve identified and resolved the issue causing this vulnerability so thank you for bringing it to our attention. A post incident review will be conducted shortly so we can determine the communication plan and process improvements required”.
Vroom was launched in June 2022 by Drive IQ Technology as an AI-powered dealership finance platform that aimed to streamline vehicle financing by instantly matching customers with participating lenders. In 2023 the company was rebranded from Drive IQ to YouX. The dates of the records range from 2022 through 2025. Although I did see references to Vroom and Drive IQ in a limited sample, I did not see any mentions of YOUx.
In an interview with a startup news website, the service was described as “Vroom reviews customer identification information, multi bureau credit information, vehicle details and uses an AI matching algorithm to serve customers with pre-approved finance offers from lenders.” According to the Drive IQ website, they claim to be Australia’s largest online marketplace for car loans.
Identity documents are a required part of the financing approval process; however, these should never be publicly accessible to anyone with an internet connection. Although the database contained images of users’ documents, I did not see any proprietary coding or development records about how Vroom’s technology functions, as these were segregated and stored in a different location.
Any data exposure that contains images of identification and financial documents poses serious potential risks. Documents such as driver’s licenses, Medicaid cards, bank statements, and employment records could potentially be used by cybercriminals for a wide range of fraudulent activities, from launching targeted social engineering attempts to creating fraudulent accounts, applying for loans, or even impersonating victims.
The publicly exposed Amazon S3 database was not password-protected or encrypted. It contained 27,000 records, including driver’s licenses, medicaid cards, employment statements, and bank statements that contain account numbers and partial credit card numbers. The name of the database and its internal files indicated they belonged to Australian Fintech company Vroom by YouX (formerly Drive IQ).
Additionally, I saw an internal screenshot that showed the information of an additional MongoDB storage instance that contained 3.2 million documents. I did not review the MongoDB, and it is unknown for me if those files were accessible or secured, but there are numerous potential risks to exposing additional file storage locations, database names, and systems that are intended for internal use. When cybercriminals know where internal data is stored, it could possibly become an additional attack vector or backdoor deeper into a network.
I immediately sent a responsible disclosure notice to Vroom, and the database was restricted from public access and no longer accessible shortly after. It should be noted that AWS S3 is a key-value store, and S3 is effectively considered to be a NoSQL database, which is why I reference “database” in this report. Although the records belonged to Vroom by YouX, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I received a response the following day stating: “We’ve identified and resolved the issue causing this vulnerability so thank you for bringing it to our attention. A post incident review will be conducted shortly so we can determine the communication plan and process improvements required”.
Vroom was launched in June 2022 by Drive IQ Technology as an AI-powered dealership finance platform that aimed to streamline vehicle financing by instantly matching customers with participating lenders. In 2023 the company was rebranded from Drive IQ to YouX. The dates of the records range from 2022 through 2025. Although I did see references to Vroom and Drive IQ in a limited sample, I did not see any mentions of YOUx.
In an interview with a startup news website, the service was described as “Vroom reviews customer identification information, multi bureau credit information, vehicle details and uses an AI matching algorithm to serve customers with pre-approved finance offers from lenders.” According to the Drive IQ website, they claim to be Australia’s largest online marketplace for car loans.
Identity documents are a required part of the financing approval process; however, these should never be publicly accessible to anyone with an internet connection. Although the database contained images of users’ documents, I did not see any proprietary coding or development records about how Vroom’s technology functions, as these were segregated and stored in a different location.
Any data exposure that contains images of identification and financial documents poses serious potential risks. Documents such as driver’s licenses, Medicaid cards, bank statements, and employment records could potentially be used by cybercriminals for a wide range of fraudulent activities, from launching targeted social engineering attempts to creating fraudulent accounts, applying for loans, or even impersonating victims.Another concern would be the exposure of partial credit card numbers. In this case, I saw the first 3 and last 4 numbers of credit cards in several .Json files. When criminals have partial card numbers, they may be able to cross-reference previous breaches to find the missing numbers, or combine them with other leaked financial details and attempt targeted phishing scams to have the individual provide the missing numbers. I am not implying that Vroom’s customers or users are at imminent risk of being targeted for any type of fraudulent activities. I only highlight the potential real-world risks when this type of data is exposed. According to research conducted by Sophos in 2024, the financial industry is a prime target for cybercriminals, with 65% of organizations falling victim to ransomware attacks. As financial technology expands and fundamentally changes how consumers manage money or obtain financing, cybersecurity must also evolve to meet the risks and threats the industry faces today and tomorrow. I would highly recommend that Fintech companies implement additional security measures in both the applications or dashboards customers use, but also the internal storage networks where sensitive documents are stowed. One of the best ways to protect these records would be to implement end-to-end encryption of sensitive data. This includes applying access controls (to know who can view or download data from an organization) and ensuring that multi-factor authentication (MFA) is required for both customers, users, and employees. Security audits and penetration testing are also an important tool to identify vulnerabilities or data exposures and should never be overlooked. Moreover, I recommend that Fintech companies use data minimization policies — collect and store active data while deleting outdated records that are no longer in use. On balance, it is potentially risky to hold large amounts of sensitive records if they become a liability. Finally, active monitoring and anomaly detection systems can identify suspicious activity and respond to potential breaches before they become a critical incident. It is also important to notify users when their personal information has been exposed so that they are aware of any potential risks. Customers who may have had their PII exposed in a data breach should monitor their credit profiles, financial accounts, and identities for potential misuse or unauthorized activity. In the unfortunate event that customers do identify suspicious transactions or misuse, they should report them immediately to the authorities and their financial institution. The most important thing is to remain vigilant — understand the risks and know what to look for to catch any unauthorized activity as early as possible. In the past, scammers and criminals have used information from data breaches to launch phishing attempts (via email or phone call), impersonating financial institutions or known service providers in a quest to obtain additional personal data. I always recommend verifying the authenticity of any unexpected requests for personal or financial information — only use official communication channels to transmit sensitive information. It is also a good idea to update all passwords and enable MFA as an extra layer of security on any accounts that may have been compromised. If an individual suspects their identity has been stolen, they should contact the Australian Cyber Security Centre (ACSC) and consider reporting it to Scamwatch to help prevent further fraud. I imply no wrongdoing by Vroom, Drive IQ, YouX, or any contractors, affiliates, or related entities. I do not claim that internal, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures. As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots as necessary and solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.