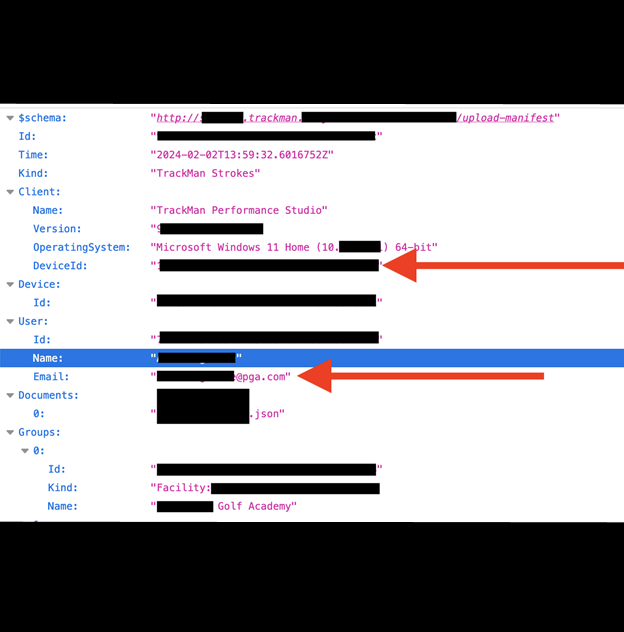
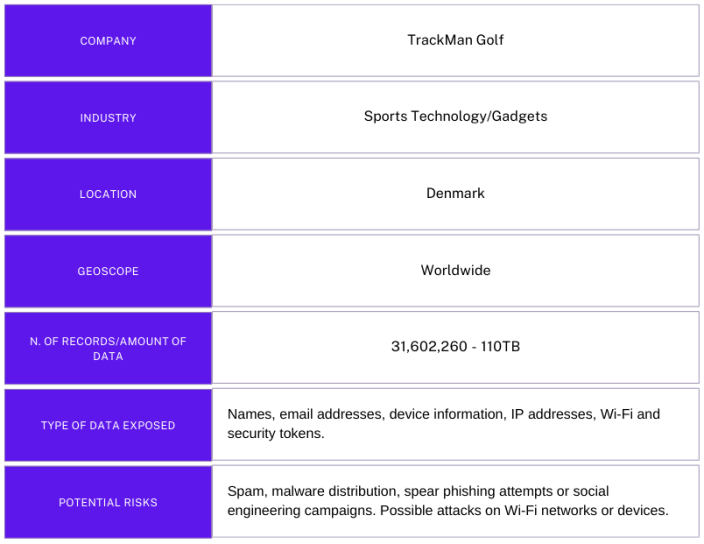
 The publicly exposed database was not password protected or encrypted and contained 31,602,260 records with a total size of 110 TB. The records indicated the customers’ user’s name and email address and also contained potentially sensitive data such as device information, IP addresses, and security tokens. Upon further research, I identified that the records belonged to TrackMan, a technology company that provides golf simulators, range solutions, and launch monitors. I immediately sent a responsible disclosure notice, and public access was restricted the same day. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from TrackMan after my disclosure notice or at any time before publication. It is not known if the database was owned and managed by TrackMan or a third party contractor.
TrackMan is arguably the most well-known sports technology company, specializing in data analytics for performance improvement in sports such as golf and baseball. TrackMan provides subscription software, indoor golf simulators, and physical devices such as launch monitors that measure key parameters like club speed, ball speed, launch angle, spin rate, and more. The tracking systems use Doppler radar and imaging technology to capture detailed data on ball flight and player movement. Among the exposed documents, I saw numerous “session” reports with highly detailed analytics and statistics. TrackMan’s technology is used in broadcasting, offering viewers detailed graphics and statistics that enhance the viewing experience. Their sports analytics technology provides software solutions for performance analysis, coaching, and player development. In a limited sampling of documents, nearly all of them indicated the use of TrackMan Performance Studio.
The publicly exposed database was not password protected or encrypted and contained 31,602,260 records with a total size of 110 TB. The records indicated the customers’ user’s name and email address and also contained potentially sensitive data such as device information, IP addresses, and security tokens. Upon further research, I identified that the records belonged to TrackMan, a technology company that provides golf simulators, range solutions, and launch monitors. I immediately sent a responsible disclosure notice, and public access was restricted the same day. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from TrackMan after my disclosure notice or at any time before publication. It is not known if the database was owned and managed by TrackMan or a third party contractor.
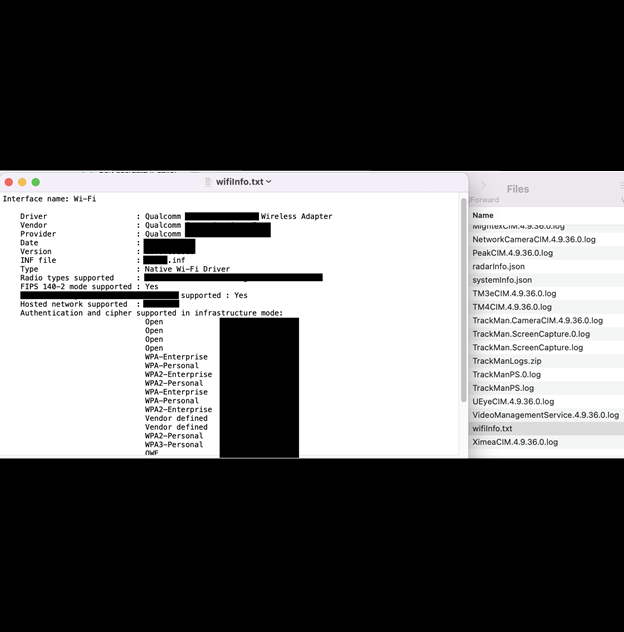
TrackMan is arguably the most well-known sports technology company, specializing in data analytics for performance improvement in sports such as golf and baseball. TrackMan provides subscription software, indoor golf simulators, and physical devices such as launch monitors that measure key parameters like club speed, ball speed, launch angle, spin rate, and more. The tracking systems use Doppler radar and imaging technology to capture detailed data on ball flight and player movement. Among the exposed documents, I saw numerous “session” reports with highly detailed analytics and statistics. TrackMan’s technology is used in broadcasting, offering viewers detailed graphics and statistics that enhance the viewing experience. Their sports analytics technology provides software solutions for performance analysis, coaching, and player development. In a limited sampling of documents, nearly all of them indicated the use of TrackMan Performance Studio.According to their LinkedIn page: Since 2003, TrackMan has been on the forefront of providing reliable performance data solutions and industry-leading innovation to customers all over the world. Our products are used by professional and amateur athletes in a broad spectrum of sports, ranging from the popular segments of golf, baseball, and tennis, to more unique disciplines like the Olympic Game’s (sic) hammer throw and shot put. TrackMan’s proprietary, radar-based technology drives the next generation of performance analysis and statistics. TrackMan is also used by the world’s largest broadcast companies from the Golf Channel to BBC, and CNN World. Any data exposure that contains names and emails could potentially be used to target those individuals for spam, malware distribution, spear phishing attempts or social engineering campaigns. Many of these individuals are professional athletes and as such, could potentially be higher value targets than amateur users. According to their website, the TrackMan system and software itself is priced at $25,495 for non-commercial use at the time of writing, and the software subscription is an additional $1,000 per year for non-commercial use. This is not a small amount of money and, considering that financial gain is usually the primary motivator for cyber criminals, targeting a lucrative sport or hobby is not out of the realm of possibilities. I am not saying or implying that TrackMan users are or were ever at risk of being targeted by cybercriminals, I am only identifying real-world threats to raise awareness of potential risks. Data security for connected devices is crucial because these devices often collect and transmit potentially sensitive logging data or operational information, making them a possible target for cyberattacks. Exposing device information could also have numerous potential risks for the security and integrity of those devices or the network. In this case, the files contained the computer’s Globally Unique Identifier (GUID). The GUID is a 32-character alphanumeric code that is used to identify a specific device and ensure that no two devices have the same identifier. Although the exposure of the GUID is considered less sensitive compared to other types of information (like passwords or personal data), it still poses numerous potential cyber security risks. Cyber criminals can use GUIDs for network reconnaissance to gather detailed information about software versions and configurations, or to identify known vulnerabilities. Once a potential weakness has been identified, criminals could then target specific GUIDs associated with known flaws and potentially exploit weaknesses in the device’s defenses. This includes the possibility of privilege escalation to gain unauthorized access or escalate privileges. Among the most concerning files I saw were those that contained Wi-Fi and device hardware information. Just like the potential risks of exposing GUIDs, the Wi-Fi driver and configuration information can be exploited and create serious potential security risks for users. If a cyber criminal can identify known vulnerabilities specific to the individual wireless adapter, it could allow them to remotely gain unauthorized access to the device or the Wi-Fi network. Knowing the types of authentication and encryption the device uses (such as WPA2-Personal or WPA3-Personal) could potentially allow criminals to launch targeted attacks on the network using brute force or downgrade attacks. Another serious concern would be a successful man-in-the middle attack (MITM) where criminals could compromise the router using unique identifiers from an exposure, allowing them to potentially intercept or alter communications between the connected devices and the network. I am not saying that TrackMan or their users are or were ever at risk of these types of cyber attacks, I am only providing a hypothetical risk scenario. Sports technology companies need to collect and store user data, device information, and statistics. That data needs to be available to users on demand and stored securely to ensure that it does not contain additional information that could expose vulnerabilities or PII. I recommend that any organization storing massive amounts of data in a cloud storage repository take additional steps to safeguard this data. Service providers should implement strong encryption methods, require users to use multi-factor authentication, regularly update software to patch vulnerabilities, and limit access to sensitive or internal data so it’s available only to those who need it. Additionally, it is always a good idea to monitor your cloud storage accounts for unusual activity. This can identify if someone is downloading or transferring internal files. It is extremely important to conduct regular security audits to protect against unauthorized access and identify vulnerabilities. I imply no wrongdoing by TrackMan, and I do not claim that internal data or customer data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by TrackMan or the party who managed the database would be able to identify this information along with any potential suspicious activity related to the breach. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties, and I disclaim any responsibility for actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy.