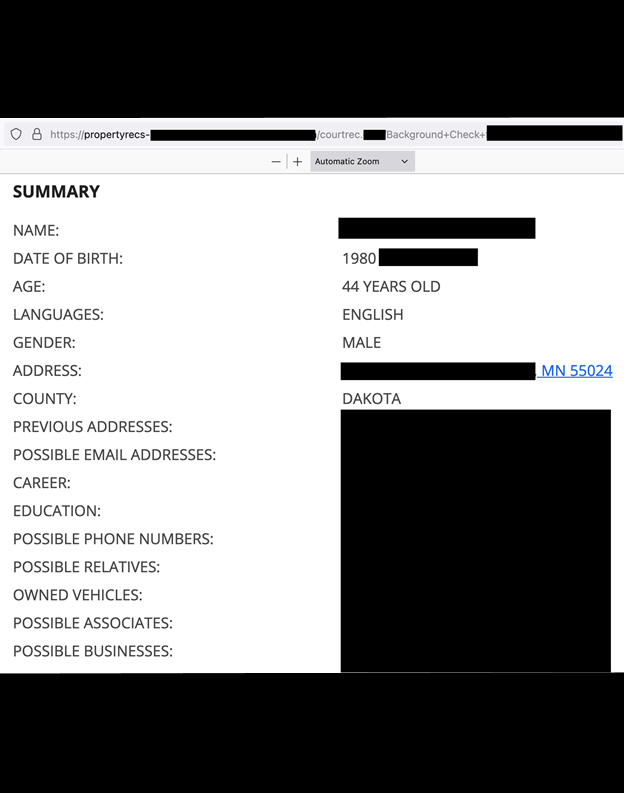
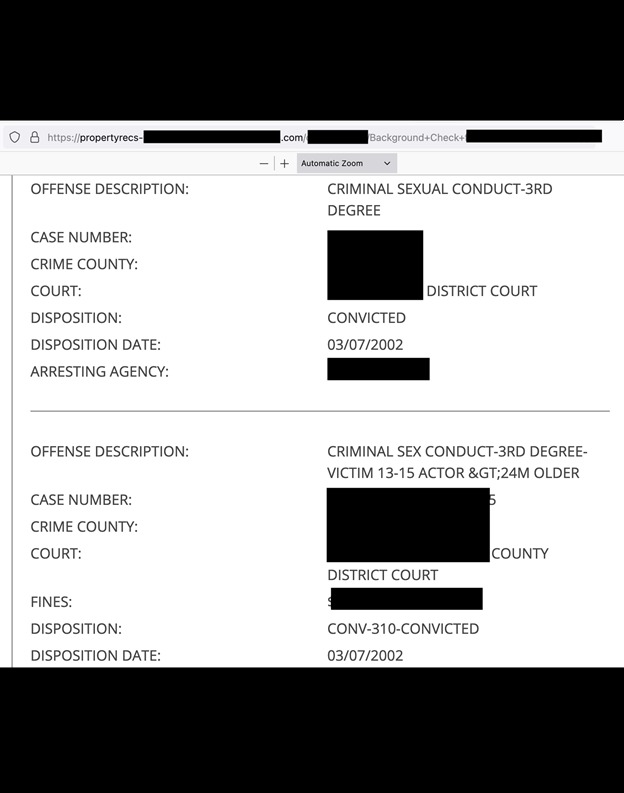
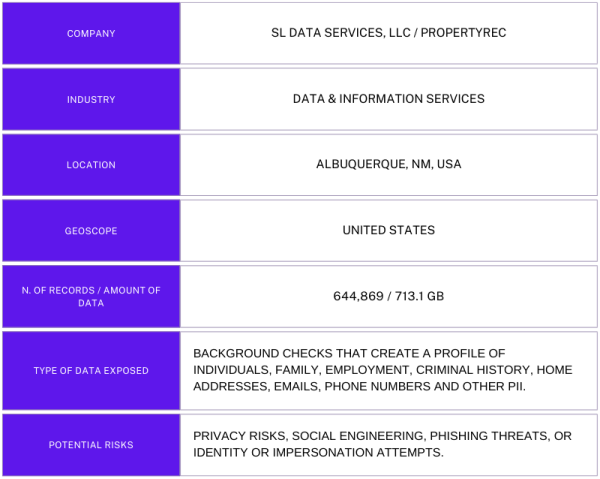
 The publicly exposed database was not password-protected or encrypted. It contained 644,869 PDF files (713.1 GB in total), including court records, vehicle records (license plate and VIN) and property ownership reports. However, around 95% of the limited sample of documents I saw were labeled as “background checks”. These documents contained full names (first, last, and middle), home addresses, phone numbers, email addresses, employment, family members, social media accounts, and criminal record history. In a sample of individuals with unique names, I found individuals with the same name matching the home address listed in the background check documents. This information provides a full profile of these individuals and raises potentially concerning privacy considerations.
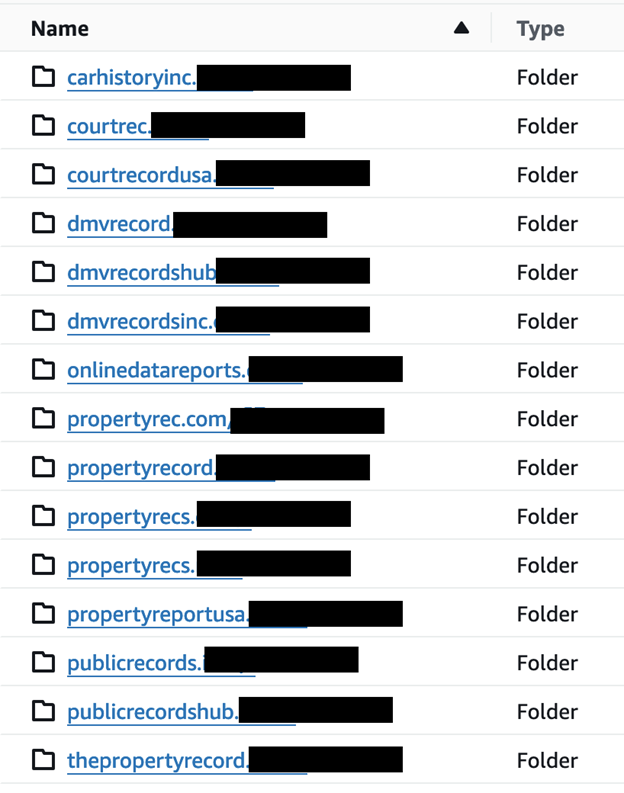
The database belongs to SL Data Services, LLC, though the folders inside it were named with separate website domains. It appears that the company operates a network of an estimated 16 different websites, offering a range of information services. For instance, Propertyrec — a website that advertises property and real estate research data — was mentioned in the database’s name. I immediately sent a responsible disclosure notice, and public access was restricted over one week later. In the time from my discovery until the records were secured, the number of documents in the database grew from 513,876 to 664,934 (+151,058). I did not receive a reply at the time of publication.
It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from SL Data Services / Propertyrec after my disclosure notice or at any time before publication. It is not known if the database was owned and managed by SL Data Services / Propertyrec or a third-party contractor.
According to an article posted in USA Today “PropertyRecs is an online platform where users can access millions of public and private property records in every jurisdiction across the United States.” However, it seems the company offers more than just property records. In a phone call to customer support, I was told they also provide criminal checks, division of motor vehicles (DMV) records, death and birth records. Numerous customer reviews suggests that while the company claims users can get individual documents for as low as $1 per search, instead of a one-time payment, users are unknowingly enrolled in a subscription service, and charged a recurring monthly fee.
These background checks are likely conducted without the knowledge or consent of the individual under review. In the United States, court records and sex offender status are generally considered public records. However, when combined with enough data points, attackers could potentially piece together full profiles of those individuals, their associates, employers, or family members. Hypothetically, the background checks could provide criminals with additional information that could be used to launch targeted phishing attempts or social engineering attacks. The criminals could potentially leverage information about family members, employment, or criminal cases to obtain additional sensitive personal information, financial data, or other privacy threats.
Another potential concern would be impersonation attempts where a criminal uses the identity of an individual whose personal information was exposed in a background check document. I am not stating nor implying that Propertyrec’s customers or any individuals are at risk of impersonation, spear phishing, or social engineering attacks, I am only providing a real world risk scenario of how this type of information could possibly be exploited by criminals.
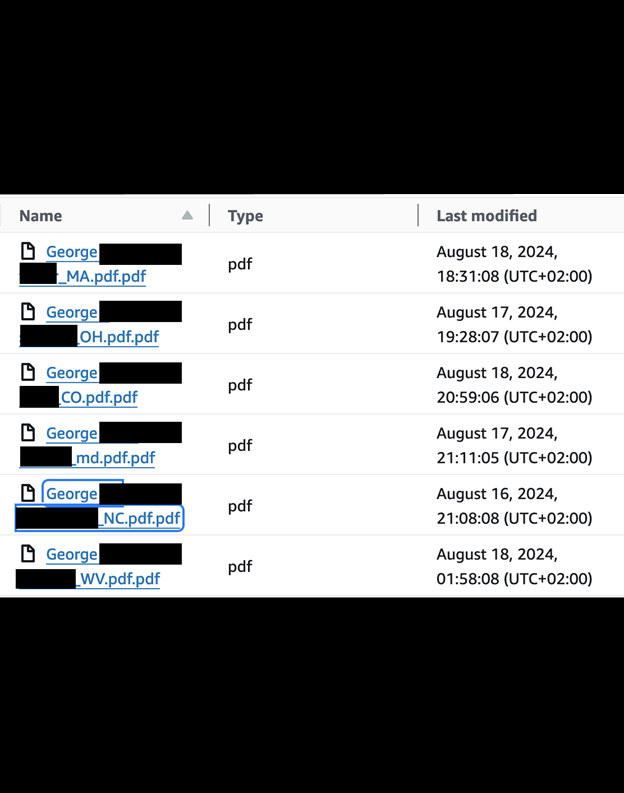
Using PII, such as customer names and locations, in filenames may be a convenient method to organize and make files searchable in an internal document storage system, but it is not recommended from a security standpoint. In the event of a data breach, such filenames pose additional privacy and data security risks even if the files were encrypted (in this case they were not encrypted). Filenames that contain PII could allow unauthorized users to see information simply by viewing the directory or metadata and without opening the file.
I would recommend that organizations use unique identifiers that are random and hashed instead of using customer names or PII as the filenames. These unique identifiers can help ensure that filenames do not contain any personal, sensitive or identifiable information. Companies should also avoid using predictable patterns in file names; for example, in this database, the files were named using the following format: “First_Middle_Last_State.PDF”. Additionally, companies who collect and store potentially sensitive data should monitor access logs. This can help identify any unusual patterns, such as instances of mass viewing or downloading of files from the organization’s cloud storage database or internal network.
This discovery comes only months after the August 2024 National Public Data incident — a data breach of a background check service that compromised the names, addresses, phone numbers, and other confidential details of millions of individuals. In the National Public Data incident, hackers accessed the company’s systems and advertised the stolen data on the darkweb. The cyber criminals offered the dataset containing the PII of US, Canadian, and UK citizens as well as access to National Public Data’s server for $3.5 million USD.
I imply no wrongdoing by SL Data Services, LLC doing business as Propertyrec, their partners, associates, agents, or third-party contractors, nor do I claim that internal data or customer data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures.
As an ethical security researcher, I do not download the data I discover; I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerabilities and notifying the relevant parties. I disclaim any and all responsibility for actions taken by third parties or others that may be taken as a result of this disclosure. I do not conduct any unauthorized actions, exploit the vulnerabilities, or engage in any activities that would compromise the data further. I publish my findings solely to raise awareness on data security and privacy issues.
The publicly exposed database was not password-protected or encrypted. It contained 644,869 PDF files (713.1 GB in total), including court records, vehicle records (license plate and VIN) and property ownership reports. However, around 95% of the limited sample of documents I saw were labeled as “background checks”. These documents contained full names (first, last, and middle), home addresses, phone numbers, email addresses, employment, family members, social media accounts, and criminal record history. In a sample of individuals with unique names, I found individuals with the same name matching the home address listed in the background check documents. This information provides a full profile of these individuals and raises potentially concerning privacy considerations.
The database belongs to SL Data Services, LLC, though the folders inside it were named with separate website domains. It appears that the company operates a network of an estimated 16 different websites, offering a range of information services. For instance, Propertyrec — a website that advertises property and real estate research data — was mentioned in the database’s name. I immediately sent a responsible disclosure notice, and public access was restricted over one week later. In the time from my discovery until the records were secured, the number of documents in the database grew from 513,876 to 664,934 (+151,058). I did not receive a reply at the time of publication.
It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from SL Data Services / Propertyrec after my disclosure notice or at any time before publication. It is not known if the database was owned and managed by SL Data Services / Propertyrec or a third-party contractor.
According to an article posted in USA Today “PropertyRecs is an online platform where users can access millions of public and private property records in every jurisdiction across the United States.” However, it seems the company offers more than just property records. In a phone call to customer support, I was told they also provide criminal checks, division of motor vehicles (DMV) records, death and birth records. Numerous customer reviews suggests that while the company claims users can get individual documents for as low as $1 per search, instead of a one-time payment, users are unknowingly enrolled in a subscription service, and charged a recurring monthly fee.
These background checks are likely conducted without the knowledge or consent of the individual under review. In the United States, court records and sex offender status are generally considered public records. However, when combined with enough data points, attackers could potentially piece together full profiles of those individuals, their associates, employers, or family members. Hypothetically, the background checks could provide criminals with additional information that could be used to launch targeted phishing attempts or social engineering attacks. The criminals could potentially leverage information about family members, employment, or criminal cases to obtain additional sensitive personal information, financial data, or other privacy threats.
Another potential concern would be impersonation attempts where a criminal uses the identity of an individual whose personal information was exposed in a background check document. I am not stating nor implying that Propertyrec’s customers or any individuals are at risk of impersonation, spear phishing, or social engineering attacks, I am only providing a real world risk scenario of how this type of information could possibly be exploited by criminals.
Using PII, such as customer names and locations, in filenames may be a convenient method to organize and make files searchable in an internal document storage system, but it is not recommended from a security standpoint. In the event of a data breach, such filenames pose additional privacy and data security risks even if the files were encrypted (in this case they were not encrypted). Filenames that contain PII could allow unauthorized users to see information simply by viewing the directory or metadata and without opening the file.
I would recommend that organizations use unique identifiers that are random and hashed instead of using customer names or PII as the filenames. These unique identifiers can help ensure that filenames do not contain any personal, sensitive or identifiable information. Companies should also avoid using predictable patterns in file names; for example, in this database, the files were named using the following format: “First_Middle_Last_State.PDF”. Additionally, companies who collect and store potentially sensitive data should monitor access logs. This can help identify any unusual patterns, such as instances of mass viewing or downloading of files from the organization’s cloud storage database or internal network.
This discovery comes only months after the August 2024 National Public Data incident — a data breach of a background check service that compromised the names, addresses, phone numbers, and other confidential details of millions of individuals. In the National Public Data incident, hackers accessed the company’s systems and advertised the stolen data on the darkweb. The cyber criminals offered the dataset containing the PII of US, Canadian, and UK citizens as well as access to National Public Data’s server for $3.5 million USD.
I imply no wrongdoing by SL Data Services, LLC doing business as Propertyrec, their partners, associates, agents, or third-party contractors, nor do I claim that internal data or customer data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures.
As an ethical security researcher, I do not download the data I discover; I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerabilities and notifying the relevant parties. I disclaim any and all responsibility for actions taken by third parties or others that may be taken as a result of this disclosure. I do not conduct any unauthorized actions, exploit the vulnerabilities, or engage in any activities that would compromise the data further. I publish my findings solely to raise awareness on data security and privacy issues.

Over 600,000 Records, Including Background Checks, Vehicle, and Property Records Exposed Online by an Information Service Provider
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to Website Planet about a non-password-protected database that contained more than 600K records belonging to SL Data Services/Propertyrec — an information research provider that offers real estate ownership data and criminal records search information.
![propertyrec-databreach-keyelements]() The publicly exposed database was not password-protected or encrypted. It contained 644,869 PDF files (713.1 GB in total), including court records, vehicle records (license plate and VIN) and property ownership reports. However, around 95% of the limited sample of documents I saw were labeled as “background checks”. These documents contained full names (first, last, and middle), home addresses, phone numbers, email addresses, employment, family members, social media accounts, and criminal record history. In a sample of individuals with unique names, I found individuals with the same name matching the home address listed in the background check documents. This information provides a full profile of these individuals and raises potentially concerning privacy considerations.
The database belongs to SL Data Services, LLC, though the folders inside it were named with separate website domains. It appears that the company operates a network of an estimated 16 different websites, offering a range of information services. For instance, Propertyrec — a website that advertises property and real estate research data — was mentioned in the database’s name. I immediately sent a responsible disclosure notice, and public access was restricted over one week later. In the time from my discovery until the records were secured, the number of documents in the database grew from 513,876 to 664,934 (+151,058). I did not receive a reply at the time of publication.
It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from SL Data Services / Propertyrec after my disclosure notice or at any time before publication. It is not known if the database was owned and managed by SL Data Services / Propertyrec or a third-party contractor.
According to an article posted in USA Today “PropertyRecs is an online platform where users can access millions of public and private property records in every jurisdiction across the United States.” However, it seems the company offers more than just property records. In a phone call to customer support, I was told they also provide criminal checks, division of motor vehicles (DMV) records, death and birth records. Numerous customer reviews suggests that while the company claims users can get individual documents for as low as $1 per search, instead of a one-time payment, users are unknowingly enrolled in a subscription service, and charged a recurring monthly fee.
These background checks are likely conducted without the knowledge or consent of the individual under review. In the United States, court records and sex offender status are generally considered public records. However, when combined with enough data points, attackers could potentially piece together full profiles of those individuals, their associates, employers, or family members. Hypothetically, the background checks could provide criminals with additional information that could be used to launch targeted phishing attempts or social engineering attacks. The criminals could potentially leverage information about family members, employment, or criminal cases to obtain additional sensitive personal information, financial data, or other privacy threats.
Another potential concern would be impersonation attempts where a criminal uses the identity of an individual whose personal information was exposed in a background check document. I am not stating nor implying that Propertyrec’s customers or any individuals are at risk of impersonation, spear phishing, or social engineering attacks, I am only providing a real world risk scenario of how this type of information could possibly be exploited by criminals.
Using PII, such as customer names and locations, in filenames may be a convenient method to organize and make files searchable in an internal document storage system, but it is not recommended from a security standpoint. In the event of a data breach, such filenames pose additional privacy and data security risks even if the files were encrypted (in this case they were not encrypted). Filenames that contain PII could allow unauthorized users to see information simply by viewing the directory or metadata and without opening the file.
I would recommend that organizations use unique identifiers that are random and hashed instead of using customer names or PII as the filenames. These unique identifiers can help ensure that filenames do not contain any personal, sensitive or identifiable information. Companies should also avoid using predictable patterns in file names; for example, in this database, the files were named using the following format: “First_Middle_Last_State.PDF”. Additionally, companies who collect and store potentially sensitive data should monitor access logs. This can help identify any unusual patterns, such as instances of mass viewing or downloading of files from the organization’s cloud storage database or internal network.
This discovery comes only months after the August 2024 National Public Data incident — a data breach of a background check service that compromised the names, addresses, phone numbers, and other confidential details of millions of individuals. In the National Public Data incident, hackers accessed the company’s systems and advertised the stolen data on the darkweb. The cyber criminals offered the dataset containing the PII of US, Canadian, and UK citizens as well as access to National Public Data’s server for $3.5 million USD.
I imply no wrongdoing by SL Data Services, LLC doing business as Propertyrec, their partners, associates, agents, or third-party contractors, nor do I claim that internal data or customer data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures.
As an ethical security researcher, I do not download the data I discover; I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerabilities and notifying the relevant parties. I disclaim any and all responsibility for actions taken by third parties or others that may be taken as a result of this disclosure. I do not conduct any unauthorized actions, exploit the vulnerabilities, or engage in any activities that would compromise the data further. I publish my findings solely to raise awareness on data security and privacy issues.
The publicly exposed database was not password-protected or encrypted. It contained 644,869 PDF files (713.1 GB in total), including court records, vehicle records (license plate and VIN) and property ownership reports. However, around 95% of the limited sample of documents I saw were labeled as “background checks”. These documents contained full names (first, last, and middle), home addresses, phone numbers, email addresses, employment, family members, social media accounts, and criminal record history. In a sample of individuals with unique names, I found individuals with the same name matching the home address listed in the background check documents. This information provides a full profile of these individuals and raises potentially concerning privacy considerations.
The database belongs to SL Data Services, LLC, though the folders inside it were named with separate website domains. It appears that the company operates a network of an estimated 16 different websites, offering a range of information services. For instance, Propertyrec — a website that advertises property and real estate research data — was mentioned in the database’s name. I immediately sent a responsible disclosure notice, and public access was restricted over one week later. In the time from my discovery until the records were secured, the number of documents in the database grew from 513,876 to 664,934 (+151,058). I did not receive a reply at the time of publication.
It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from SL Data Services / Propertyrec after my disclosure notice or at any time before publication. It is not known if the database was owned and managed by SL Data Services / Propertyrec or a third-party contractor.
According to an article posted in USA Today “PropertyRecs is an online platform where users can access millions of public and private property records in every jurisdiction across the United States.” However, it seems the company offers more than just property records. In a phone call to customer support, I was told they also provide criminal checks, division of motor vehicles (DMV) records, death and birth records. Numerous customer reviews suggests that while the company claims users can get individual documents for as low as $1 per search, instead of a one-time payment, users are unknowingly enrolled in a subscription service, and charged a recurring monthly fee.
These background checks are likely conducted without the knowledge or consent of the individual under review. In the United States, court records and sex offender status are generally considered public records. However, when combined with enough data points, attackers could potentially piece together full profiles of those individuals, their associates, employers, or family members. Hypothetically, the background checks could provide criminals with additional information that could be used to launch targeted phishing attempts or social engineering attacks. The criminals could potentially leverage information about family members, employment, or criminal cases to obtain additional sensitive personal information, financial data, or other privacy threats.
Another potential concern would be impersonation attempts where a criminal uses the identity of an individual whose personal information was exposed in a background check document. I am not stating nor implying that Propertyrec’s customers or any individuals are at risk of impersonation, spear phishing, or social engineering attacks, I am only providing a real world risk scenario of how this type of information could possibly be exploited by criminals.
Using PII, such as customer names and locations, in filenames may be a convenient method to organize and make files searchable in an internal document storage system, but it is not recommended from a security standpoint. In the event of a data breach, such filenames pose additional privacy and data security risks even if the files were encrypted (in this case they were not encrypted). Filenames that contain PII could allow unauthorized users to see information simply by viewing the directory or metadata and without opening the file.
I would recommend that organizations use unique identifiers that are random and hashed instead of using customer names or PII as the filenames. These unique identifiers can help ensure that filenames do not contain any personal, sensitive or identifiable information. Companies should also avoid using predictable patterns in file names; for example, in this database, the files were named using the following format: “First_Middle_Last_State.PDF”. Additionally, companies who collect and store potentially sensitive data should monitor access logs. This can help identify any unusual patterns, such as instances of mass viewing or downloading of files from the organization’s cloud storage database or internal network.
This discovery comes only months after the August 2024 National Public Data incident — a data breach of a background check service that compromised the names, addresses, phone numbers, and other confidential details of millions of individuals. In the National Public Data incident, hackers accessed the company’s systems and advertised the stolen data on the darkweb. The cyber criminals offered the dataset containing the PII of US, Canadian, and UK citizens as well as access to National Public Data’s server for $3.5 million USD.
I imply no wrongdoing by SL Data Services, LLC doing business as Propertyrec, their partners, associates, agents, or third-party contractors, nor do I claim that internal data or customer data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures.
As an ethical security researcher, I do not download the data I discover; I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerabilities and notifying the relevant parties. I disclaim any and all responsibility for actions taken by third parties or others that may be taken as a result of this disclosure. I do not conduct any unauthorized actions, exploit the vulnerabilities, or engage in any activities that would compromise the data further. I publish my findings solely to raise awareness on data security and privacy issues.
 The publicly exposed database was not password-protected or encrypted. It contained 644,869 PDF files (713.1 GB in total), including court records, vehicle records (license plate and VIN) and property ownership reports. However, around 95% of the limited sample of documents I saw were labeled as “background checks”. These documents contained full names (first, last, and middle), home addresses, phone numbers, email addresses, employment, family members, social media accounts, and criminal record history. In a sample of individuals with unique names, I found individuals with the same name matching the home address listed in the background check documents. This information provides a full profile of these individuals and raises potentially concerning privacy considerations.
The database belongs to SL Data Services, LLC, though the folders inside it were named with separate website domains. It appears that the company operates a network of an estimated 16 different websites, offering a range of information services. For instance, Propertyrec — a website that advertises property and real estate research data — was mentioned in the database’s name. I immediately sent a responsible disclosure notice, and public access was restricted over one week later. In the time from my discovery until the records were secured, the number of documents in the database grew from 513,876 to 664,934 (+151,058). I did not receive a reply at the time of publication.
It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from SL Data Services / Propertyrec after my disclosure notice or at any time before publication. It is not known if the database was owned and managed by SL Data Services / Propertyrec or a third-party contractor.
According to an article posted in USA Today “PropertyRecs is an online platform where users can access millions of public and private property records in every jurisdiction across the United States.” However, it seems the company offers more than just property records. In a phone call to customer support, I was told they also provide criminal checks, division of motor vehicles (DMV) records, death and birth records. Numerous customer reviews suggests that while the company claims users can get individual documents for as low as $1 per search, instead of a one-time payment, users are unknowingly enrolled in a subscription service, and charged a recurring monthly fee.
These background checks are likely conducted without the knowledge or consent of the individual under review. In the United States, court records and sex offender status are generally considered public records. However, when combined with enough data points, attackers could potentially piece together full profiles of those individuals, their associates, employers, or family members. Hypothetically, the background checks could provide criminals with additional information that could be used to launch targeted phishing attempts or social engineering attacks. The criminals could potentially leverage information about family members, employment, or criminal cases to obtain additional sensitive personal information, financial data, or other privacy threats.
Another potential concern would be impersonation attempts where a criminal uses the identity of an individual whose personal information was exposed in a background check document. I am not stating nor implying that Propertyrec’s customers or any individuals are at risk of impersonation, spear phishing, or social engineering attacks, I am only providing a real world risk scenario of how this type of information could possibly be exploited by criminals.
Using PII, such as customer names and locations, in filenames may be a convenient method to organize and make files searchable in an internal document storage system, but it is not recommended from a security standpoint. In the event of a data breach, such filenames pose additional privacy and data security risks even if the files were encrypted (in this case they were not encrypted). Filenames that contain PII could allow unauthorized users to see information simply by viewing the directory or metadata and without opening the file.
I would recommend that organizations use unique identifiers that are random and hashed instead of using customer names or PII as the filenames. These unique identifiers can help ensure that filenames do not contain any personal, sensitive or identifiable information. Companies should also avoid using predictable patterns in file names; for example, in this database, the files were named using the following format: “First_Middle_Last_State.PDF”. Additionally, companies who collect and store potentially sensitive data should monitor access logs. This can help identify any unusual patterns, such as instances of mass viewing or downloading of files from the organization’s cloud storage database or internal network.
This discovery comes only months after the August 2024 National Public Data incident — a data breach of a background check service that compromised the names, addresses, phone numbers, and other confidential details of millions of individuals. In the National Public Data incident, hackers accessed the company’s systems and advertised the stolen data on the darkweb. The cyber criminals offered the dataset containing the PII of US, Canadian, and UK citizens as well as access to National Public Data’s server for $3.5 million USD.
I imply no wrongdoing by SL Data Services, LLC doing business as Propertyrec, their partners, associates, agents, or third-party contractors, nor do I claim that internal data or customer data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures.
As an ethical security researcher, I do not download the data I discover; I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerabilities and notifying the relevant parties. I disclaim any and all responsibility for actions taken by third parties or others that may be taken as a result of this disclosure. I do not conduct any unauthorized actions, exploit the vulnerabilities, or engage in any activities that would compromise the data further. I publish my findings solely to raise awareness on data security and privacy issues.
The publicly exposed database was not password-protected or encrypted. It contained 644,869 PDF files (713.1 GB in total), including court records, vehicle records (license plate and VIN) and property ownership reports. However, around 95% of the limited sample of documents I saw were labeled as “background checks”. These documents contained full names (first, last, and middle), home addresses, phone numbers, email addresses, employment, family members, social media accounts, and criminal record history. In a sample of individuals with unique names, I found individuals with the same name matching the home address listed in the background check documents. This information provides a full profile of these individuals and raises potentially concerning privacy considerations.
The database belongs to SL Data Services, LLC, though the folders inside it were named with separate website domains. It appears that the company operates a network of an estimated 16 different websites, offering a range of information services. For instance, Propertyrec — a website that advertises property and real estate research data — was mentioned in the database’s name. I immediately sent a responsible disclosure notice, and public access was restricted over one week later. In the time from my discovery until the records were secured, the number of documents in the database grew from 513,876 to 664,934 (+151,058). I did not receive a reply at the time of publication.
It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from SL Data Services / Propertyrec after my disclosure notice or at any time before publication. It is not known if the database was owned and managed by SL Data Services / Propertyrec or a third-party contractor.
According to an article posted in USA Today “PropertyRecs is an online platform where users can access millions of public and private property records in every jurisdiction across the United States.” However, it seems the company offers more than just property records. In a phone call to customer support, I was told they also provide criminal checks, division of motor vehicles (DMV) records, death and birth records. Numerous customer reviews suggests that while the company claims users can get individual documents for as low as $1 per search, instead of a one-time payment, users are unknowingly enrolled in a subscription service, and charged a recurring monthly fee.
These background checks are likely conducted without the knowledge or consent of the individual under review. In the United States, court records and sex offender status are generally considered public records. However, when combined with enough data points, attackers could potentially piece together full profiles of those individuals, their associates, employers, or family members. Hypothetically, the background checks could provide criminals with additional information that could be used to launch targeted phishing attempts or social engineering attacks. The criminals could potentially leverage information about family members, employment, or criminal cases to obtain additional sensitive personal information, financial data, or other privacy threats.
Another potential concern would be impersonation attempts where a criminal uses the identity of an individual whose personal information was exposed in a background check document. I am not stating nor implying that Propertyrec’s customers or any individuals are at risk of impersonation, spear phishing, or social engineering attacks, I am only providing a real world risk scenario of how this type of information could possibly be exploited by criminals.
Using PII, such as customer names and locations, in filenames may be a convenient method to organize and make files searchable in an internal document storage system, but it is not recommended from a security standpoint. In the event of a data breach, such filenames pose additional privacy and data security risks even if the files were encrypted (in this case they were not encrypted). Filenames that contain PII could allow unauthorized users to see information simply by viewing the directory or metadata and without opening the file.
I would recommend that organizations use unique identifiers that are random and hashed instead of using customer names or PII as the filenames. These unique identifiers can help ensure that filenames do not contain any personal, sensitive or identifiable information. Companies should also avoid using predictable patterns in file names; for example, in this database, the files were named using the following format: “First_Middle_Last_State.PDF”. Additionally, companies who collect and store potentially sensitive data should monitor access logs. This can help identify any unusual patterns, such as instances of mass viewing or downloading of files from the organization’s cloud storage database or internal network.
This discovery comes only months after the August 2024 National Public Data incident — a data breach of a background check service that compromised the names, addresses, phone numbers, and other confidential details of millions of individuals. In the National Public Data incident, hackers accessed the company’s systems and advertised the stolen data on the darkweb. The cyber criminals offered the dataset containing the PII of US, Canadian, and UK citizens as well as access to National Public Data’s server for $3.5 million USD.
I imply no wrongdoing by SL Data Services, LLC doing business as Propertyrec, their partners, associates, agents, or third-party contractors, nor do I claim that internal data or customer data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures.
As an ethical security researcher, I do not download the data I discover; I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerabilities and notifying the relevant parties. I disclaim any and all responsibility for actions taken by third parties or others that may be taken as a result of this disclosure. I do not conduct any unauthorized actions, exploit the vulnerabilities, or engage in any activities that would compromise the data further. I publish my findings solely to raise awareness on data security and privacy issues.