Australian Travel Agency Exposed the Personal Data of Thousands of Tourists Online
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to WebsitePlanet about a non-password-protected database that contained 112k records, which included traveler information, passport images, itinerary and ticket documents.
The publicly exposed database contained a total of 112,605 records with a size of 26.8 GB. Upon further research, it appeared that the database belonged to a company named Inspiring Vacations. I immediately sent a responsible disclosure notice, and the database was secured from public access. I received a reply thanking me for my notification and confirming that I didn’t download files from the database without redactions. According to their website, Inspiring Vacations is an Australian-owned travel company based in Melbourne and has a team located in New Delhi, India.
The exposed records contained potentially sensitive information such as high-resolution passport images, travel visa certificates, and itinerary or ticket files. A vast majority of the individuals I saw in the records appeared to be Australian citizens. However, I also saw identification documents from New Zealand, the United Kingdom, and Ireland. It is unclear how many passports were affected. I saw an estimated 1,000 identification documents in a limited sample; however, there were other files in the database that detailed the customers’ passport number and other PII. The file names of the passport documents were structured in a specific manner, to include the name of the individual in plain text.
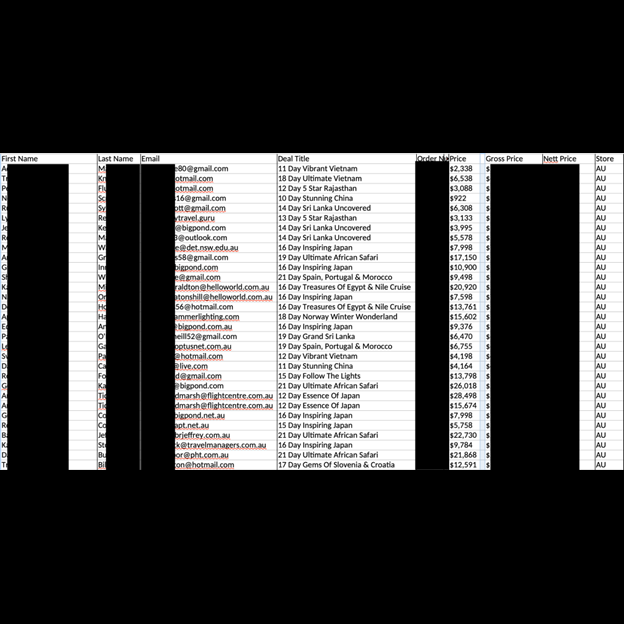
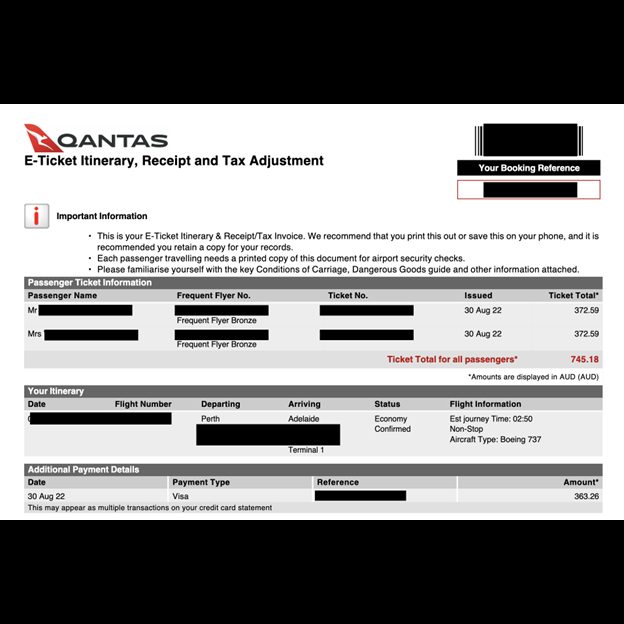
The database also included 48 .xls spreadsheets that detailed information regarding 13,684 customers, such as the travelers’ names, email addresses, trip costs, destinations, and other internal details. There were an estimated 24,000 itinerary and e-ticket .pdf documents, some of which show partial credit card numbers. In addition to customer files, the database included various internal documents, such as 17,000 tax invoices to partners and affiliates that specify gross costs and commissions paid.
Traveling can be stressful enough with cancellations, delays, and dealing with other unforeseen circumstances and costs, which is why many people find it easier and more comfortable to use a travel agency when planning their vacations rather than doing it all themselves. However, in the digital age that we live in, tourists may need to add ‘data security’ to the long list of travel concerns. The travel industry is a lucrative potential target for cyber criminals — not only are vacations expensive (which means travelers are attractive marks), but any travel agency would need their clients’ personal information and identity documents to make reservations on their behalf. Traveling abroad, for instance, requires a passport and sometimes an entry visa. Travelers rarely consider what happens to their highly valuable personal data, how or where their information is stored, and for how long it is retained.