Nearly 150,000 Records Were Exposed Online by On-Site Medical Service Provider
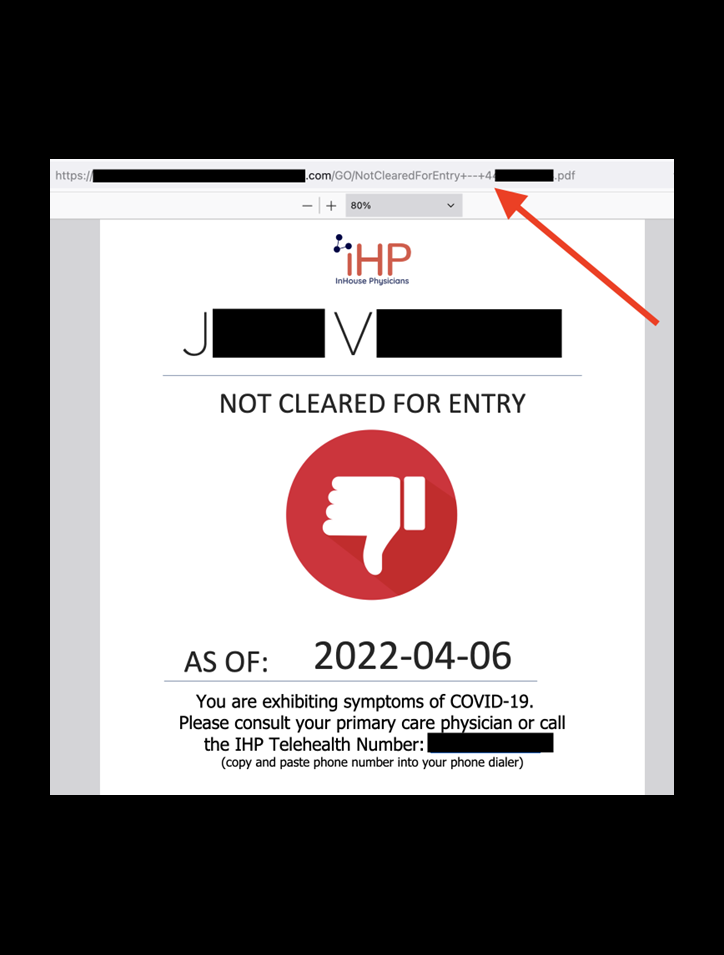
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to Website Planet about a non-password-protected database that contained 148,000 records belonging to InHouse Physicians — a healthcare provider that offers on-site medical services and wellness programs to organizations, including corporate health and wellness solutions, event medical services, and occupational health programs.The database contained documents indicating if the person was cleared to enter an event or tested positive for COVID-19 and denied entry and included names and phone numbers.
The non-password-protected database contained 148,415 PDF documents totalling 12 GB. Each document contained the name of the individual and indicated whether they were cleared or denied entry to conferences, events, or other functions based on the results of medical screenings. The documents indicating denials included instructions of what to do if the individuals were experiencing symptoms of COVID-19. Each document contained the logo and phone number of Illinois-based InHouse Physicians. I immediately sent a responsible disclosure notice, and public access was restricted shortly after. InHouse Physicians acted fast and professionally to secure the documents and thanked me for the notification and bringing it to their attention. Although the documents belonged to InHouse Physicians, it is not known if they managed the database or if it was managed by a third party.
According to their LinkedIn profile: InHouse Physicians is a global provider of innovative onsite healthcare solutions that assist corporations in reducing healthcare claims. Using a value-based approach, our “next generation” worksite clinics reduce healthcare costs while improving health outcomes that matter most to patients.
During the COVID-19 pandemic, healthcare providers and organizations collected vast amounts of personal and medical data, as testing was often mandatory to attend events, work, or travel. The emergency situation and the need to share vast amounts of information across different healthcare systems, government agencies, and patients caught many organizations unprepared for mass data storage, data protection, and privacy. Both public and private health providers had to collect and store test results, vaccination records, contact-tracing information, and personal health details of millions of individuals with little to no planning or guidance. Now that the pandemic is behind us, there is a serious risk of these databases being abandoned or left unsecured and posing potential security and privacy threats. This data exposure of COVID-19 era documents is a prime example of how healthcare organizations should prioritize auditing and reviewing what information they have stored, who has access to such information, and whether the data should be given an expiration date once it is no longer in active use.
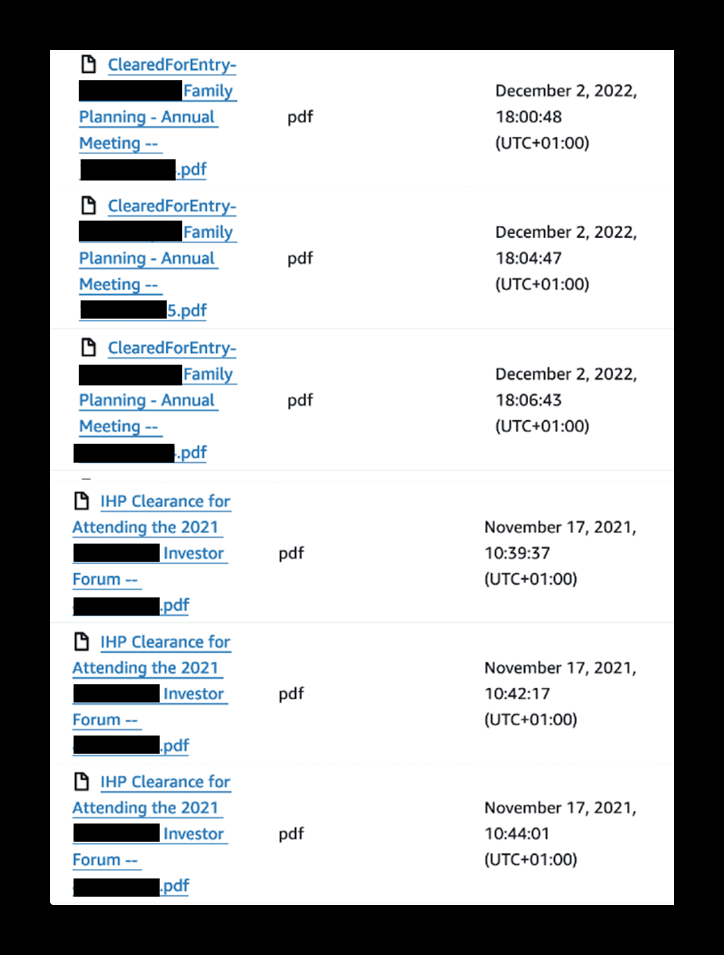
In the publicly exposed PDF files, I saw information indicating statuses of attendees for a wide range of events such as investor forums, family planning services, and other potentially sensitive sectors that could be high-value targets for cyber criminals. For verification purposes, I selected a random sample of documents from the database, and I looked up the names and phone numbers on search engines and open source tools available to the general public. By doing this, I was able to easily obtain further identification details on the individuals from the sample. This means it would be easy for criminals to exploit the exposed information and target individuals with phishing campaigns or social engineering tactics. I am not saying these individuals are at imminent risk of fraud, I am only providing hypothetical scenarios for educational purposes of how these exposed data points could potentially be used by malicious actors.
According to a report by DarkReading, there were an estimated 24+ billion credentials circulating on the dark web in 2022. This is a massive amount of data that criminals can use to build a complete profile of potential victims. Once high value targets are selected, nefarious actors can source information from known public data and then cross-reference that with the ever-growing amount of exposed data that is being sold or dumped on the dark web. In this case, the names of some of the files I saw included the first and last names of individuals as well as their phone numbers.
One potential risk of exposed phone numbers would be SIM cloning, also known as SIM swapping or SIM hijacking. There are numerous documented cases of cyber criminals using the victim’s phone number, supplemented by additional personal information, to impersonate the victim and convince a mobile provider to issue a new SIM card. Once the attacker has successfully swapped the SIM, they gain control over the victim’s phone number and mobile account, allowing the criminal to receive calls, texts, and intercept any two-factor authentication codes sent to the number associated with the account. This also means criminals could potentially reset passwords for accounts linked to that number, such as email, social media, banking accounts, and more.
According to a warning issued by the FBI Internet Crime Complaint Center (IC3), in 2021, victims of SIM swapping reported losses of more than $68 million. That represents an increase of nearly 460% in just one year. It also indicates a growing risk of a very non-technical crime that relies on choosing a target, gathering exposed data, and using social engineering tactics. In November 2022, criminals were able to steal $400 million in cryptocurrency after they SIM-swapped an AT&T customer by using a fake ID and impersonating them at a physical retail store. I am not saying that patients or customers of InHouse Physicians are at risk of a social engineering attack or of being a victim to SIM swapping, I am only highlighting how SIM swapping works and the potential risks involved for educational purposes on the importance of data protection.