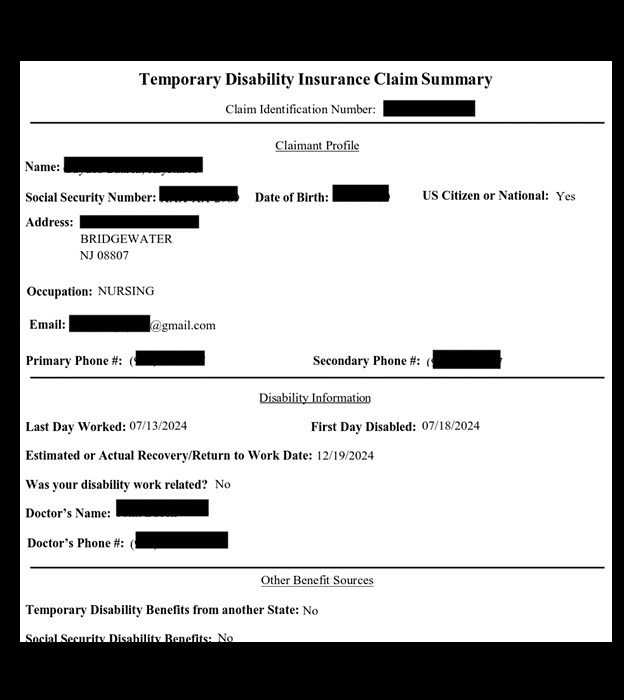
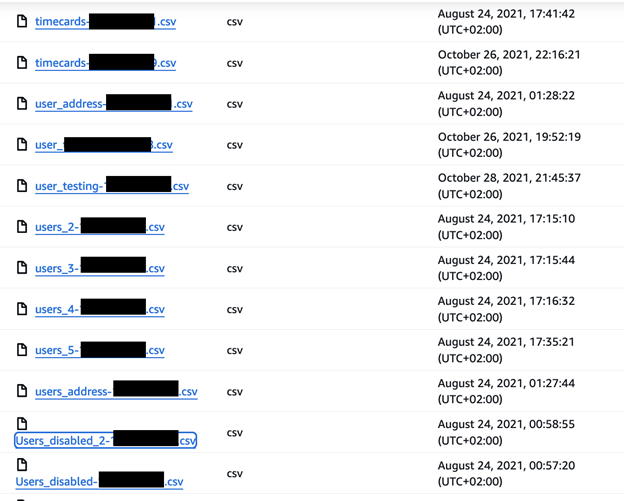
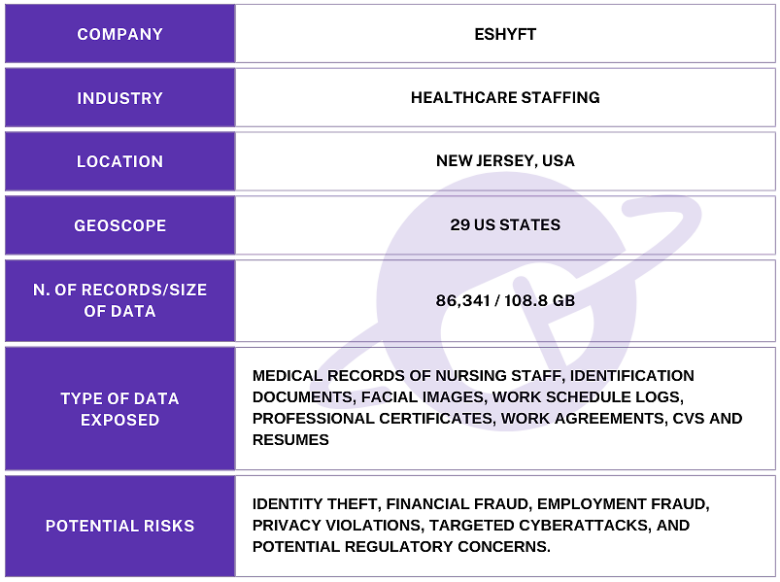
 The publicly exposed database was not password-protected or encrypted. It contained 86,341 records totaling 108.8 GB in size. The majority of the documents were contained inside of a folder labeled “App”. In a limited sampling of the exposed documents, I saw records that included profile or facial images of users, .csv files with monthly work schedule logs, professional certificates, work assignment agreements, CVs and resumes that contained additional PII. One single spreadsheet document contained 800,000+ entries that detailed the nurse’s internal IDs, facility name, time and date of shifts, hours worked, and more.
I also saw what appeared to be medical documents uploaded to the app. These files were potentially uploaded as proof for why individual nurses missed shifts or took sick leave. These medical documents included medical reports containing information of diagnosis, prescriptions, or treatments that could potentially fall under the ambit of HIPAA regulations.
The name of the database as well as the documents inside it indicated that the records belonged to ESHYFT. I immediately sent a responsible disclosure notice to the company, and the database was restricted from public access over a month later. I received a response thanking me for the notification stating: “Thank you! we’re actively looking into this and working on a solution”. It is not known if the database was owned and managed by ESHYFT directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
ESHYFT provides a mobile platform that connects healthcare facilities with qualified nursing professionals. It is available on both Apple’s App Store and the Google Play Store. Apple no longer provides user statistics, but the ESHYFT app has been downloaded more than 50,000 times from the Google Play Store.
The application claims to offer nurses the flexibility to select shifts that fit their schedules while providing healthcare facilities with access to vetted W-2 nursing staff to meet their needs. The platform is available in following U.S. states: AL, AZ, AR, CA, CT, DE, FL, GA, IL, IN, IA, KS, KY, MD, MI, MN, MO, NE, NJ, OH, PA, RI, SC, TN, VT, VA, WA, WI, and WV.
A report by the Health Resources & Services Administration (NCHWA) projects a 10% nationwide shortage of registered nurses by 2027. With the growing need for healthcare workers, platforms like ESHYFT serve an important role in filling those staffing deficiencies. This means that workers who perform offline jobs (like nursing) are now integrated with online technology, and healthtech companies need to implement robust privacy safeguards to bridge the gap securely.
As more hospitals and healthcare workers depend on technology for data storage, care management, and employment, the need for increased cybersecurity measures across the entire industry is inescapable. Hospitals are considered critical infrastructure and have been routinely targeted by cybercriminals. In recent years, numerous networks have been hit with devastating ransomware attacks. In my opinion, the data and PII of the doctors, nurses, and staff are equally as important as the healthcare facilities themselves.
Any exposure of Personally Identifiable Information (PII), salary details, and work history of nursing professionals could result in significant potential risks and vulnerabilities — both for the affected individuals and the healthcare facilities that employ them. Scans of identification documents (such as driver’s licenses or Social Security cards) when combined with addresses and other contact details could hypothetically provide a gateway for cybercriminals to commit identity theft or financial fraud in the victims’ names.
Another potential risk of exposed personal and professional details would be highly targeted phishing campaigns that could use real information to deceive victims with employment scams or drive them into revealing additional personal or financial data. I am not suggesting or implying that ESHYFT’s data or that of their users is at risk of any type of scam or fraudulent activity, or compromised in any manner. I am only providing a general observation of potential cybersecurity risks as it relates to the exposure of personally identifiable information. This commentary is intended solely to highlight the broader landscape of privacy and cybersecurity considerations.
My recommendations for healthtech companies and medical software providers would be to take proactive cybersecurity measures to protect their data and prevent unauthorized access. This would include mandatory encryption protocols of sensitive data and regular security audits of internal infrastructure to identify potential vulnerabilities. It is always a good idea to limit the storage of sensitive data and anonymize records where possible. This includes assigning data an expiration date once it is no longer in use.
In this particular case, it appears that user files were uploaded to a single folder and not segregated based on their sensitivity. As an example, a user’s profile image could have a low sensitivity rating while proof of a medical exam could have a high sensitivity rating. In theory, these two documents should not be stored in the same folder. When sensitive data is segregated and encrypted, it adds an additional layer of protection in the event of an accidental exposure or malicious attack.
Moreover, multi-factor authentication (MFA) should be a requirement for any application where the user has access to potentially sensitive information or documents. By requiring MFA, even if user credentials (like username and password) are exposed, it is more difficult for someone to simply login and gain full access to the application or user dashboard.
Lastly, for healthtech companies of any size, it is a good idea to have a data breach response plan in place and a dedicated communication channel for reporting potential security incidents. Far too often I observe that companies have only customer support or sales contacts listed, forgoing the contact information of key stakeholders who need to act in case of a data breach. When sensitive data is publicly exposed, every second counts, and any delay in mitigation and recovery could be potentially catastrophic.
It is also important to give timely responsible disclosure notices to anybody who could be directly affected by the breach. After any data incident, users should be notified and educated on how to recognize phishing attempts in relation to the specific application or service that was potentially compromised. Protecting users from the real risks of social engineering and phishing attempts makes common sense and benefits both the service provider and the user or customer.
I imply no wrongdoing by Shiftster LLC dba ESHYFT, any contractors or affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 86,341 records totaling 108.8 GB in size. The majority of the documents were contained inside of a folder labeled “App”. In a limited sampling of the exposed documents, I saw records that included profile or facial images of users, .csv files with monthly work schedule logs, professional certificates, work assignment agreements, CVs and resumes that contained additional PII. One single spreadsheet document contained 800,000+ entries that detailed the nurse’s internal IDs, facility name, time and date of shifts, hours worked, and more.
I also saw what appeared to be medical documents uploaded to the app. These files were potentially uploaded as proof for why individual nurses missed shifts or took sick leave. These medical documents included medical reports containing information of diagnosis, prescriptions, or treatments that could potentially fall under the ambit of HIPAA regulations.
The name of the database as well as the documents inside it indicated that the records belonged to ESHYFT. I immediately sent a responsible disclosure notice to the company, and the database was restricted from public access over a month later. I received a response thanking me for the notification stating: “Thank you! we’re actively looking into this and working on a solution”. It is not known if the database was owned and managed by ESHYFT directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
ESHYFT provides a mobile platform that connects healthcare facilities with qualified nursing professionals. It is available on both Apple’s App Store and the Google Play Store. Apple no longer provides user statistics, but the ESHYFT app has been downloaded more than 50,000 times from the Google Play Store.
The application claims to offer nurses the flexibility to select shifts that fit their schedules while providing healthcare facilities with access to vetted W-2 nursing staff to meet their needs. The platform is available in following U.S. states: AL, AZ, AR, CA, CT, DE, FL, GA, IL, IN, IA, KS, KY, MD, MI, MN, MO, NE, NJ, OH, PA, RI, SC, TN, VT, VA, WA, WI, and WV.
A report by the Health Resources & Services Administration (NCHWA) projects a 10% nationwide shortage of registered nurses by 2027. With the growing need for healthcare workers, platforms like ESHYFT serve an important role in filling those staffing deficiencies. This means that workers who perform offline jobs (like nursing) are now integrated with online technology, and healthtech companies need to implement robust privacy safeguards to bridge the gap securely.
As more hospitals and healthcare workers depend on technology for data storage, care management, and employment, the need for increased cybersecurity measures across the entire industry is inescapable. Hospitals are considered critical infrastructure and have been routinely targeted by cybercriminals. In recent years, numerous networks have been hit with devastating ransomware attacks. In my opinion, the data and PII of the doctors, nurses, and staff are equally as important as the healthcare facilities themselves.
Any exposure of Personally Identifiable Information (PII), salary details, and work history of nursing professionals could result in significant potential risks and vulnerabilities — both for the affected individuals and the healthcare facilities that employ them. Scans of identification documents (such as driver’s licenses or Social Security cards) when combined with addresses and other contact details could hypothetically provide a gateway for cybercriminals to commit identity theft or financial fraud in the victims’ names.
Another potential risk of exposed personal and professional details would be highly targeted phishing campaigns that could use real information to deceive victims with employment scams or drive them into revealing additional personal or financial data. I am not suggesting or implying that ESHYFT’s data or that of their users is at risk of any type of scam or fraudulent activity, or compromised in any manner. I am only providing a general observation of potential cybersecurity risks as it relates to the exposure of personally identifiable information. This commentary is intended solely to highlight the broader landscape of privacy and cybersecurity considerations.
My recommendations for healthtech companies and medical software providers would be to take proactive cybersecurity measures to protect their data and prevent unauthorized access. This would include mandatory encryption protocols of sensitive data and regular security audits of internal infrastructure to identify potential vulnerabilities. It is always a good idea to limit the storage of sensitive data and anonymize records where possible. This includes assigning data an expiration date once it is no longer in use.
In this particular case, it appears that user files were uploaded to a single folder and not segregated based on their sensitivity. As an example, a user’s profile image could have a low sensitivity rating while proof of a medical exam could have a high sensitivity rating. In theory, these two documents should not be stored in the same folder. When sensitive data is segregated and encrypted, it adds an additional layer of protection in the event of an accidental exposure or malicious attack.
Moreover, multi-factor authentication (MFA) should be a requirement for any application where the user has access to potentially sensitive information or documents. By requiring MFA, even if user credentials (like username and password) are exposed, it is more difficult for someone to simply login and gain full access to the application or user dashboard.
Lastly, for healthtech companies of any size, it is a good idea to have a data breach response plan in place and a dedicated communication channel for reporting potential security incidents. Far too often I observe that companies have only customer support or sales contacts listed, forgoing the contact information of key stakeholders who need to act in case of a data breach. When sensitive data is publicly exposed, every second counts, and any delay in mitigation and recovery could be potentially catastrophic.
It is also important to give timely responsible disclosure notices to anybody who could be directly affected by the breach. After any data incident, users should be notified and educated on how to recognize phishing attempts in relation to the specific application or service that was potentially compromised. Protecting users from the real risks of social engineering and phishing attempts makes common sense and benefits both the service provider and the user or customer.
I imply no wrongdoing by Shiftster LLC dba ESHYFT, any contractors or affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.

Thousands of Records, Including PII, Exposed Online in Healthcare Marketplace Connecting Facilities and Nurses Data Leak
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to Website Planet about a non-password-protected database that contained over 86,000 records belonging to ESHYFT — a New-Jersey-based HealthTech company that operates in 29 states. It offers a mobile app platform that connects healthcare facilities with healthcare workers, including Certified Nursing Assistants (CNAs), Licensed Practical Nurses (LPNs), and Registered Nurses (RNs).
![WSP-ESHYFT-healthtech-data-breach-key-elements]() The publicly exposed database was not password-protected or encrypted. It contained 86,341 records totaling 108.8 GB in size. The majority of the documents were contained inside of a folder labeled “App”. In a limited sampling of the exposed documents, I saw records that included profile or facial images of users, .csv files with monthly work schedule logs, professional certificates, work assignment agreements, CVs and resumes that contained additional PII. One single spreadsheet document contained 800,000+ entries that detailed the nurse’s internal IDs, facility name, time and date of shifts, hours worked, and more.
I also saw what appeared to be medical documents uploaded to the app. These files were potentially uploaded as proof for why individual nurses missed shifts or took sick leave. These medical documents included medical reports containing information of diagnosis, prescriptions, or treatments that could potentially fall under the ambit of HIPAA regulations.
The name of the database as well as the documents inside it indicated that the records belonged to ESHYFT. I immediately sent a responsible disclosure notice to the company, and the database was restricted from public access over a month later. I received a response thanking me for the notification stating: “Thank you! we’re actively looking into this and working on a solution”. It is not known if the database was owned and managed by ESHYFT directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
ESHYFT provides a mobile platform that connects healthcare facilities with qualified nursing professionals. It is available on both Apple’s App Store and the Google Play Store. Apple no longer provides user statistics, but the ESHYFT app has been downloaded more than 50,000 times from the Google Play Store.
The application claims to offer nurses the flexibility to select shifts that fit their schedules while providing healthcare facilities with access to vetted W-2 nursing staff to meet their needs. The platform is available in following U.S. states: AL, AZ, AR, CA, CT, DE, FL, GA, IL, IN, IA, KS, KY, MD, MI, MN, MO, NE, NJ, OH, PA, RI, SC, TN, VT, VA, WA, WI, and WV.
A report by the Health Resources & Services Administration (NCHWA) projects a 10% nationwide shortage of registered nurses by 2027. With the growing need for healthcare workers, platforms like ESHYFT serve an important role in filling those staffing deficiencies. This means that workers who perform offline jobs (like nursing) are now integrated with online technology, and healthtech companies need to implement robust privacy safeguards to bridge the gap securely.
As more hospitals and healthcare workers depend on technology for data storage, care management, and employment, the need for increased cybersecurity measures across the entire industry is inescapable. Hospitals are considered critical infrastructure and have been routinely targeted by cybercriminals. In recent years, numerous networks have been hit with devastating ransomware attacks. In my opinion, the data and PII of the doctors, nurses, and staff are equally as important as the healthcare facilities themselves.
Any exposure of Personally Identifiable Information (PII), salary details, and work history of nursing professionals could result in significant potential risks and vulnerabilities — both for the affected individuals and the healthcare facilities that employ them. Scans of identification documents (such as driver’s licenses or Social Security cards) when combined with addresses and other contact details could hypothetically provide a gateway for cybercriminals to commit identity theft or financial fraud in the victims’ names.
Another potential risk of exposed personal and professional details would be highly targeted phishing campaigns that could use real information to deceive victims with employment scams or drive them into revealing additional personal or financial data. I am not suggesting or implying that ESHYFT’s data or that of their users is at risk of any type of scam or fraudulent activity, or compromised in any manner. I am only providing a general observation of potential cybersecurity risks as it relates to the exposure of personally identifiable information. This commentary is intended solely to highlight the broader landscape of privacy and cybersecurity considerations.
My recommendations for healthtech companies and medical software providers would be to take proactive cybersecurity measures to protect their data and prevent unauthorized access. This would include mandatory encryption protocols of sensitive data and regular security audits of internal infrastructure to identify potential vulnerabilities. It is always a good idea to limit the storage of sensitive data and anonymize records where possible. This includes assigning data an expiration date once it is no longer in use.
In this particular case, it appears that user files were uploaded to a single folder and not segregated based on their sensitivity. As an example, a user’s profile image could have a low sensitivity rating while proof of a medical exam could have a high sensitivity rating. In theory, these two documents should not be stored in the same folder. When sensitive data is segregated and encrypted, it adds an additional layer of protection in the event of an accidental exposure or malicious attack.
Moreover, multi-factor authentication (MFA) should be a requirement for any application where the user has access to potentially sensitive information or documents. By requiring MFA, even if user credentials (like username and password) are exposed, it is more difficult for someone to simply login and gain full access to the application or user dashboard.
Lastly, for healthtech companies of any size, it is a good idea to have a data breach response plan in place and a dedicated communication channel for reporting potential security incidents. Far too often I observe that companies have only customer support or sales contacts listed, forgoing the contact information of key stakeholders who need to act in case of a data breach. When sensitive data is publicly exposed, every second counts, and any delay in mitigation and recovery could be potentially catastrophic.
It is also important to give timely responsible disclosure notices to anybody who could be directly affected by the breach. After any data incident, users should be notified and educated on how to recognize phishing attempts in relation to the specific application or service that was potentially compromised. Protecting users from the real risks of social engineering and phishing attempts makes common sense and benefits both the service provider and the user or customer.
I imply no wrongdoing by Shiftster LLC dba ESHYFT, any contractors or affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 86,341 records totaling 108.8 GB in size. The majority of the documents were contained inside of a folder labeled “App”. In a limited sampling of the exposed documents, I saw records that included profile or facial images of users, .csv files with monthly work schedule logs, professional certificates, work assignment agreements, CVs and resumes that contained additional PII. One single spreadsheet document contained 800,000+ entries that detailed the nurse’s internal IDs, facility name, time and date of shifts, hours worked, and more.
I also saw what appeared to be medical documents uploaded to the app. These files were potentially uploaded as proof for why individual nurses missed shifts or took sick leave. These medical documents included medical reports containing information of diagnosis, prescriptions, or treatments that could potentially fall under the ambit of HIPAA regulations.
The name of the database as well as the documents inside it indicated that the records belonged to ESHYFT. I immediately sent a responsible disclosure notice to the company, and the database was restricted from public access over a month later. I received a response thanking me for the notification stating: “Thank you! we’re actively looking into this and working on a solution”. It is not known if the database was owned and managed by ESHYFT directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
ESHYFT provides a mobile platform that connects healthcare facilities with qualified nursing professionals. It is available on both Apple’s App Store and the Google Play Store. Apple no longer provides user statistics, but the ESHYFT app has been downloaded more than 50,000 times from the Google Play Store.
The application claims to offer nurses the flexibility to select shifts that fit their schedules while providing healthcare facilities with access to vetted W-2 nursing staff to meet their needs. The platform is available in following U.S. states: AL, AZ, AR, CA, CT, DE, FL, GA, IL, IN, IA, KS, KY, MD, MI, MN, MO, NE, NJ, OH, PA, RI, SC, TN, VT, VA, WA, WI, and WV.
A report by the Health Resources & Services Administration (NCHWA) projects a 10% nationwide shortage of registered nurses by 2027. With the growing need for healthcare workers, platforms like ESHYFT serve an important role in filling those staffing deficiencies. This means that workers who perform offline jobs (like nursing) are now integrated with online technology, and healthtech companies need to implement robust privacy safeguards to bridge the gap securely.
As more hospitals and healthcare workers depend on technology for data storage, care management, and employment, the need for increased cybersecurity measures across the entire industry is inescapable. Hospitals are considered critical infrastructure and have been routinely targeted by cybercriminals. In recent years, numerous networks have been hit with devastating ransomware attacks. In my opinion, the data and PII of the doctors, nurses, and staff are equally as important as the healthcare facilities themselves.
Any exposure of Personally Identifiable Information (PII), salary details, and work history of nursing professionals could result in significant potential risks and vulnerabilities — both for the affected individuals and the healthcare facilities that employ them. Scans of identification documents (such as driver’s licenses or Social Security cards) when combined with addresses and other contact details could hypothetically provide a gateway for cybercriminals to commit identity theft or financial fraud in the victims’ names.
Another potential risk of exposed personal and professional details would be highly targeted phishing campaigns that could use real information to deceive victims with employment scams or drive them into revealing additional personal or financial data. I am not suggesting or implying that ESHYFT’s data or that of their users is at risk of any type of scam or fraudulent activity, or compromised in any manner. I am only providing a general observation of potential cybersecurity risks as it relates to the exposure of personally identifiable information. This commentary is intended solely to highlight the broader landscape of privacy and cybersecurity considerations.
My recommendations for healthtech companies and medical software providers would be to take proactive cybersecurity measures to protect their data and prevent unauthorized access. This would include mandatory encryption protocols of sensitive data and regular security audits of internal infrastructure to identify potential vulnerabilities. It is always a good idea to limit the storage of sensitive data and anonymize records where possible. This includes assigning data an expiration date once it is no longer in use.
In this particular case, it appears that user files were uploaded to a single folder and not segregated based on their sensitivity. As an example, a user’s profile image could have a low sensitivity rating while proof of a medical exam could have a high sensitivity rating. In theory, these two documents should not be stored in the same folder. When sensitive data is segregated and encrypted, it adds an additional layer of protection in the event of an accidental exposure or malicious attack.
Moreover, multi-factor authentication (MFA) should be a requirement for any application where the user has access to potentially sensitive information or documents. By requiring MFA, even if user credentials (like username and password) are exposed, it is more difficult for someone to simply login and gain full access to the application or user dashboard.
Lastly, for healthtech companies of any size, it is a good idea to have a data breach response plan in place and a dedicated communication channel for reporting potential security incidents. Far too often I observe that companies have only customer support or sales contacts listed, forgoing the contact information of key stakeholders who need to act in case of a data breach. When sensitive data is publicly exposed, every second counts, and any delay in mitigation and recovery could be potentially catastrophic.
It is also important to give timely responsible disclosure notices to anybody who could be directly affected by the breach. After any data incident, users should be notified and educated on how to recognize phishing attempts in relation to the specific application or service that was potentially compromised. Protecting users from the real risks of social engineering and phishing attempts makes common sense and benefits both the service provider and the user or customer.
I imply no wrongdoing by Shiftster LLC dba ESHYFT, any contractors or affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.
 The publicly exposed database was not password-protected or encrypted. It contained 86,341 records totaling 108.8 GB in size. The majority of the documents were contained inside of a folder labeled “App”. In a limited sampling of the exposed documents, I saw records that included profile or facial images of users, .csv files with monthly work schedule logs, professional certificates, work assignment agreements, CVs and resumes that contained additional PII. One single spreadsheet document contained 800,000+ entries that detailed the nurse’s internal IDs, facility name, time and date of shifts, hours worked, and more.
I also saw what appeared to be medical documents uploaded to the app. These files were potentially uploaded as proof for why individual nurses missed shifts or took sick leave. These medical documents included medical reports containing information of diagnosis, prescriptions, or treatments that could potentially fall under the ambit of HIPAA regulations.
The name of the database as well as the documents inside it indicated that the records belonged to ESHYFT. I immediately sent a responsible disclosure notice to the company, and the database was restricted from public access over a month later. I received a response thanking me for the notification stating: “Thank you! we’re actively looking into this and working on a solution”. It is not known if the database was owned and managed by ESHYFT directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
ESHYFT provides a mobile platform that connects healthcare facilities with qualified nursing professionals. It is available on both Apple’s App Store and the Google Play Store. Apple no longer provides user statistics, but the ESHYFT app has been downloaded more than 50,000 times from the Google Play Store.
The application claims to offer nurses the flexibility to select shifts that fit their schedules while providing healthcare facilities with access to vetted W-2 nursing staff to meet their needs. The platform is available in following U.S. states: AL, AZ, AR, CA, CT, DE, FL, GA, IL, IN, IA, KS, KY, MD, MI, MN, MO, NE, NJ, OH, PA, RI, SC, TN, VT, VA, WA, WI, and WV.
A report by the Health Resources & Services Administration (NCHWA) projects a 10% nationwide shortage of registered nurses by 2027. With the growing need for healthcare workers, platforms like ESHYFT serve an important role in filling those staffing deficiencies. This means that workers who perform offline jobs (like nursing) are now integrated with online technology, and healthtech companies need to implement robust privacy safeguards to bridge the gap securely.
As more hospitals and healthcare workers depend on technology for data storage, care management, and employment, the need for increased cybersecurity measures across the entire industry is inescapable. Hospitals are considered critical infrastructure and have been routinely targeted by cybercriminals. In recent years, numerous networks have been hit with devastating ransomware attacks. In my opinion, the data and PII of the doctors, nurses, and staff are equally as important as the healthcare facilities themselves.
Any exposure of Personally Identifiable Information (PII), salary details, and work history of nursing professionals could result in significant potential risks and vulnerabilities — both for the affected individuals and the healthcare facilities that employ them. Scans of identification documents (such as driver’s licenses or Social Security cards) when combined with addresses and other contact details could hypothetically provide a gateway for cybercriminals to commit identity theft or financial fraud in the victims’ names.
Another potential risk of exposed personal and professional details would be highly targeted phishing campaigns that could use real information to deceive victims with employment scams or drive them into revealing additional personal or financial data. I am not suggesting or implying that ESHYFT’s data or that of their users is at risk of any type of scam or fraudulent activity, or compromised in any manner. I am only providing a general observation of potential cybersecurity risks as it relates to the exposure of personally identifiable information. This commentary is intended solely to highlight the broader landscape of privacy and cybersecurity considerations.
My recommendations for healthtech companies and medical software providers would be to take proactive cybersecurity measures to protect their data and prevent unauthorized access. This would include mandatory encryption protocols of sensitive data and regular security audits of internal infrastructure to identify potential vulnerabilities. It is always a good idea to limit the storage of sensitive data and anonymize records where possible. This includes assigning data an expiration date once it is no longer in use.
In this particular case, it appears that user files were uploaded to a single folder and not segregated based on their sensitivity. As an example, a user’s profile image could have a low sensitivity rating while proof of a medical exam could have a high sensitivity rating. In theory, these two documents should not be stored in the same folder. When sensitive data is segregated and encrypted, it adds an additional layer of protection in the event of an accidental exposure or malicious attack.
Moreover, multi-factor authentication (MFA) should be a requirement for any application where the user has access to potentially sensitive information or documents. By requiring MFA, even if user credentials (like username and password) are exposed, it is more difficult for someone to simply login and gain full access to the application or user dashboard.
Lastly, for healthtech companies of any size, it is a good idea to have a data breach response plan in place and a dedicated communication channel for reporting potential security incidents. Far too often I observe that companies have only customer support or sales contacts listed, forgoing the contact information of key stakeholders who need to act in case of a data breach. When sensitive data is publicly exposed, every second counts, and any delay in mitigation and recovery could be potentially catastrophic.
It is also important to give timely responsible disclosure notices to anybody who could be directly affected by the breach. After any data incident, users should be notified and educated on how to recognize phishing attempts in relation to the specific application or service that was potentially compromised. Protecting users from the real risks of social engineering and phishing attempts makes common sense and benefits both the service provider and the user or customer.
I imply no wrongdoing by Shiftster LLC dba ESHYFT, any contractors or affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 86,341 records totaling 108.8 GB in size. The majority of the documents were contained inside of a folder labeled “App”. In a limited sampling of the exposed documents, I saw records that included profile or facial images of users, .csv files with monthly work schedule logs, professional certificates, work assignment agreements, CVs and resumes that contained additional PII. One single spreadsheet document contained 800,000+ entries that detailed the nurse’s internal IDs, facility name, time and date of shifts, hours worked, and more.
I also saw what appeared to be medical documents uploaded to the app. These files were potentially uploaded as proof for why individual nurses missed shifts or took sick leave. These medical documents included medical reports containing information of diagnosis, prescriptions, or treatments that could potentially fall under the ambit of HIPAA regulations.
The name of the database as well as the documents inside it indicated that the records belonged to ESHYFT. I immediately sent a responsible disclosure notice to the company, and the database was restricted from public access over a month later. I received a response thanking me for the notification stating: “Thank you! we’re actively looking into this and working on a solution”. It is not known if the database was owned and managed by ESHYFT directly or via a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
ESHYFT provides a mobile platform that connects healthcare facilities with qualified nursing professionals. It is available on both Apple’s App Store and the Google Play Store. Apple no longer provides user statistics, but the ESHYFT app has been downloaded more than 50,000 times from the Google Play Store.
The application claims to offer nurses the flexibility to select shifts that fit their schedules while providing healthcare facilities with access to vetted W-2 nursing staff to meet their needs. The platform is available in following U.S. states: AL, AZ, AR, CA, CT, DE, FL, GA, IL, IN, IA, KS, KY, MD, MI, MN, MO, NE, NJ, OH, PA, RI, SC, TN, VT, VA, WA, WI, and WV.
A report by the Health Resources & Services Administration (NCHWA) projects a 10% nationwide shortage of registered nurses by 2027. With the growing need for healthcare workers, platforms like ESHYFT serve an important role in filling those staffing deficiencies. This means that workers who perform offline jobs (like nursing) are now integrated with online technology, and healthtech companies need to implement robust privacy safeguards to bridge the gap securely.
As more hospitals and healthcare workers depend on technology for data storage, care management, and employment, the need for increased cybersecurity measures across the entire industry is inescapable. Hospitals are considered critical infrastructure and have been routinely targeted by cybercriminals. In recent years, numerous networks have been hit with devastating ransomware attacks. In my opinion, the data and PII of the doctors, nurses, and staff are equally as important as the healthcare facilities themselves.
Any exposure of Personally Identifiable Information (PII), salary details, and work history of nursing professionals could result in significant potential risks and vulnerabilities — both for the affected individuals and the healthcare facilities that employ them. Scans of identification documents (such as driver’s licenses or Social Security cards) when combined with addresses and other contact details could hypothetically provide a gateway for cybercriminals to commit identity theft or financial fraud in the victims’ names.
Another potential risk of exposed personal and professional details would be highly targeted phishing campaigns that could use real information to deceive victims with employment scams or drive them into revealing additional personal or financial data. I am not suggesting or implying that ESHYFT’s data or that of their users is at risk of any type of scam or fraudulent activity, or compromised in any manner. I am only providing a general observation of potential cybersecurity risks as it relates to the exposure of personally identifiable information. This commentary is intended solely to highlight the broader landscape of privacy and cybersecurity considerations.
My recommendations for healthtech companies and medical software providers would be to take proactive cybersecurity measures to protect their data and prevent unauthorized access. This would include mandatory encryption protocols of sensitive data and regular security audits of internal infrastructure to identify potential vulnerabilities. It is always a good idea to limit the storage of sensitive data and anonymize records where possible. This includes assigning data an expiration date once it is no longer in use.
In this particular case, it appears that user files were uploaded to a single folder and not segregated based on their sensitivity. As an example, a user’s profile image could have a low sensitivity rating while proof of a medical exam could have a high sensitivity rating. In theory, these two documents should not be stored in the same folder. When sensitive data is segregated and encrypted, it adds an additional layer of protection in the event of an accidental exposure or malicious attack.
Moreover, multi-factor authentication (MFA) should be a requirement for any application where the user has access to potentially sensitive information or documents. By requiring MFA, even if user credentials (like username and password) are exposed, it is more difficult for someone to simply login and gain full access to the application or user dashboard.
Lastly, for healthtech companies of any size, it is a good idea to have a data breach response plan in place and a dedicated communication channel for reporting potential security incidents. Far too often I observe that companies have only customer support or sales contacts listed, forgoing the contact information of key stakeholders who need to act in case of a data breach. When sensitive data is publicly exposed, every second counts, and any delay in mitigation and recovery could be potentially catastrophic.
It is also important to give timely responsible disclosure notices to anybody who could be directly affected by the breach. After any data incident, users should be notified and educated on how to recognize phishing attempts in relation to the specific application or service that was potentially compromised. Protecting users from the real risks of social engineering and phishing attempts makes common sense and benefits both the service provider and the user or customer.
I imply no wrongdoing by Shiftster LLC dba ESHYFT, any contractors or affiliates. I do not claim that internal data or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes and do not reflect any actual compromise of data integrity. It should not be construed as a reflection of any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download the data I discover. I only take a limited number of screenshots solely for verification purposes. I do not conduct any activities beyond identifying the security vulnerability and notifying the relevant parties. I disclaim any responsibility for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness on issues of data security and privacy. My aim is to encourage organizations to proactively safeguard sensitive information against unauthorized access.