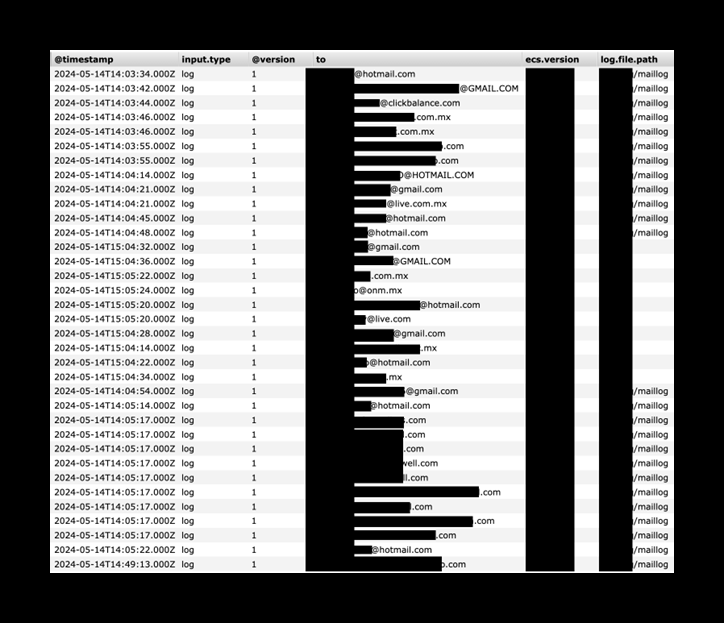
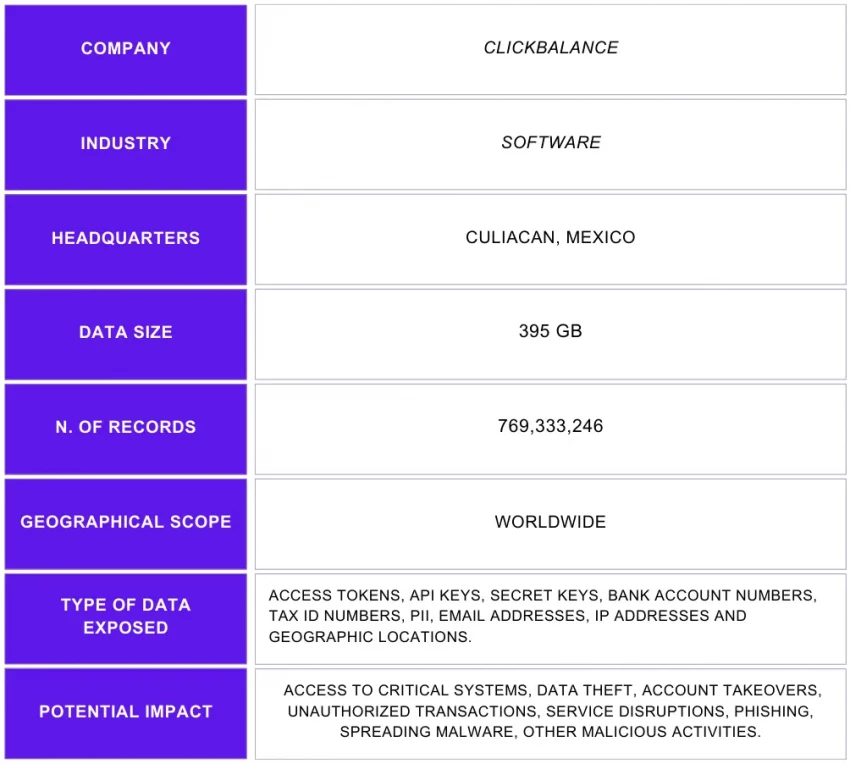
 The publicly exposed database contained potentially sensitive information such as access tokens, API keys, secret keys, bank account numbers, tax identification numbers, and 381,224 email addresses. As a whole, the database contained 769,333,246 records with a total size of 395 GB. Upon further research, I identified that the records belonged to ClickBalance, one of Mexico’s largest Enterprise Resource Planning (ERP) technology providers. Upon discovery of the database, I immediately sent a responsible disclosure notice, and public access was restricted within hours. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from ClickBalance after my disclosure notice or at any time before publication.
ClickBalance offers Enterprise Resource Planning (ERP) software as a suite of cloud-based applications that organizations can access from anywhere and on any device. ERP tools are used to manage and automate various business processes across a range of different departments. These could include finance, human resources, supply chain, manufacturing, sales, among others. The overall purpose of an ERP system is to centralize data and give the user access to real-time information on a wide range of business operations.
Any technology company that manages a wide range of data of internal and external stakeholders including multiple customers, employees, and end users may face considerable data protection challenges. This is due to the large amount of information that they need to store for each customer — and they usually have a high number of customers. For instance, ERP, CRM (Customer Relationship Management), and CDM (Customer Data Management) systems are designed to track, manage, and monitor a wide range of data that can include financial records, personal customer data, employee details, and proprietary business data. This means that a data breach concerning any of these systems can expose potentially sensitive business information, which may bring about long-term operational and strategic risks. Unfortunately, when business or financial data is exposed, it is not known how it may potentially be used by cybercriminals years into the future.
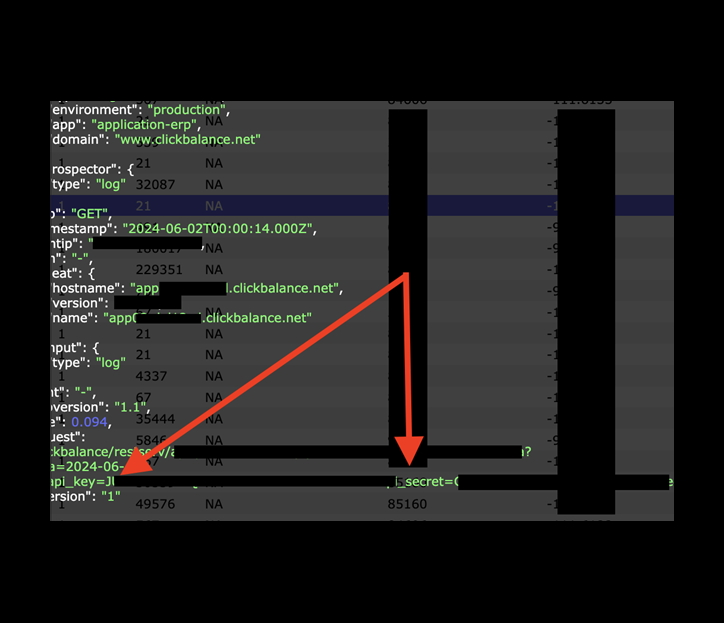
The database contained API keys and secret keys in what appeared to be plain text. These keys can grant access to critical systems and potentially sensitive data. Hypothetically, cyber criminals could exploit exposed credentials to gain unauthorized access to applications, databases, and other services. This could create a serious risk of data theft, account takeovers, unauthorized transactions, or a wide range of service disruptions. Moreover, exposed keys pose numerous potential risks to an organization’s infrastructure and internal data. Protecting keys, tokens, and other administrative credentials with access controls and secure storage practices is highly important. I am not implying that customers or end users are at risk of any unauthorized use of API keys and secret keys. I am only providing a real-world example of how this information could possibly be used by malicious actors.
The exposure of hundreds of thousands of email addresses poses potential risks far beyond spam. According to research published by Deloitte, an auditing and accounting firm, 91% of all cyberattacks begin with a phishing email. This is one of the most common tactics used by criminals, and that is because it has a high success rate and does not require any technical expertise. When criminals have insider or nonpublic information, they can create very convincing deceptive emails to try and steal personal information, financial data, login credentials, and more. In this case, cyber criminals already know that these email addresses are business related and could potentially be used to launch targeted phishing attacks.
There are other risks associated with compromised emails. For instance, they could be used for spreading malware if the organization has lax security measures. Additionally, large collections of email addresses can be sold to other criminals on the dark web, greatly increasing the potential risks. I highly recommend that any organization that has experienced a data incident take protective measures, such as changing their passwords to new ones that meet complex password requirements. It is also a good idea to enable two-factor authentication (2FA) on their accounts. This is also recommended for customers and end users whose information may have been exposed in the breach. It is important to always be cautious of unsolicited emails or suspicious information requests.
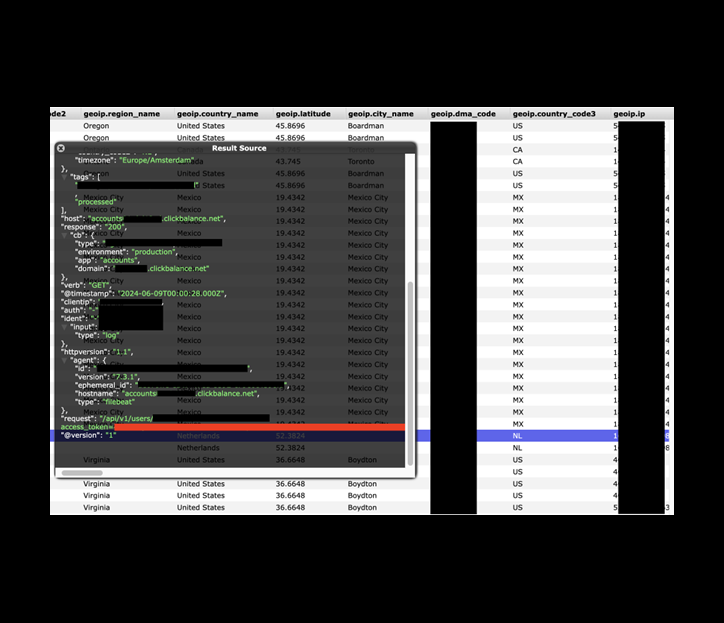
The exposure of IP addresses poses numerous risks due to the nature of the services that ClickBalance provides. Although an IP address alone is a relatively low-risk piece of information that provides limited direct access, cybercriminals may still potentially use the IP address as a starting point to enable other malicious activities. Hypothetically, cybercriminals could attempt to find vulnerabilities associated with the IP addresses. This could easily be done using port-scanning techniques. Once identified, cybercriminals could exploit those weaknesses to gain unauthorized access to the network or system. Additionally, by matching IP addresses to specific users, malicious actors could potentially launch targeted social engineering campaigns, and gather more sensitive information about an individual user, business, or the network.
A data breach of any company that provides ERP or data services can have severe potential long term consequences. Once data has been exposed online, companies should immediately implement incident response protocols and notify affected stakeholders, customers, and partners. I recommend any company which manages customer data to enhance their data security measures, conduct regular security audits, and implement the most up-to-date cybersecurity best practices.
I imply no wrongdoing by ClickBalance, nor do I claim that internal data or customer data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by ClickBalance would be able to identify this information along with any potential suspicious activity related to the breach. I publish my findings to raise awareness on issues of data security and privacy, hoping to contribute to a safer digital space for all.
The publicly exposed database contained potentially sensitive information such as access tokens, API keys, secret keys, bank account numbers, tax identification numbers, and 381,224 email addresses. As a whole, the database contained 769,333,246 records with a total size of 395 GB. Upon further research, I identified that the records belonged to ClickBalance, one of Mexico’s largest Enterprise Resource Planning (ERP) technology providers. Upon discovery of the database, I immediately sent a responsible disclosure notice, and public access was restricted within hours. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from ClickBalance after my disclosure notice or at any time before publication.
ClickBalance offers Enterprise Resource Planning (ERP) software as a suite of cloud-based applications that organizations can access from anywhere and on any device. ERP tools are used to manage and automate various business processes across a range of different departments. These could include finance, human resources, supply chain, manufacturing, sales, among others. The overall purpose of an ERP system is to centralize data and give the user access to real-time information on a wide range of business operations.
Any technology company that manages a wide range of data of internal and external stakeholders including multiple customers, employees, and end users may face considerable data protection challenges. This is due to the large amount of information that they need to store for each customer — and they usually have a high number of customers. For instance, ERP, CRM (Customer Relationship Management), and CDM (Customer Data Management) systems are designed to track, manage, and monitor a wide range of data that can include financial records, personal customer data, employee details, and proprietary business data. This means that a data breach concerning any of these systems can expose potentially sensitive business information, which may bring about long-term operational and strategic risks. Unfortunately, when business or financial data is exposed, it is not known how it may potentially be used by cybercriminals years into the future.
The database contained API keys and secret keys in what appeared to be plain text. These keys can grant access to critical systems and potentially sensitive data. Hypothetically, cyber criminals could exploit exposed credentials to gain unauthorized access to applications, databases, and other services. This could create a serious risk of data theft, account takeovers, unauthorized transactions, or a wide range of service disruptions. Moreover, exposed keys pose numerous potential risks to an organization’s infrastructure and internal data. Protecting keys, tokens, and other administrative credentials with access controls and secure storage practices is highly important. I am not implying that customers or end users are at risk of any unauthorized use of API keys and secret keys. I am only providing a real-world example of how this information could possibly be used by malicious actors.
The exposure of hundreds of thousands of email addresses poses potential risks far beyond spam. According to research published by Deloitte, an auditing and accounting firm, 91% of all cyberattacks begin with a phishing email. This is one of the most common tactics used by criminals, and that is because it has a high success rate and does not require any technical expertise. When criminals have insider or nonpublic information, they can create very convincing deceptive emails to try and steal personal information, financial data, login credentials, and more. In this case, cyber criminals already know that these email addresses are business related and could potentially be used to launch targeted phishing attacks.
There are other risks associated with compromised emails. For instance, they could be used for spreading malware if the organization has lax security measures. Additionally, large collections of email addresses can be sold to other criminals on the dark web, greatly increasing the potential risks. I highly recommend that any organization that has experienced a data incident take protective measures, such as changing their passwords to new ones that meet complex password requirements. It is also a good idea to enable two-factor authentication (2FA) on their accounts. This is also recommended for customers and end users whose information may have been exposed in the breach. It is important to always be cautious of unsolicited emails or suspicious information requests.
The exposure of IP addresses poses numerous risks due to the nature of the services that ClickBalance provides. Although an IP address alone is a relatively low-risk piece of information that provides limited direct access, cybercriminals may still potentially use the IP address as a starting point to enable other malicious activities. Hypothetically, cybercriminals could attempt to find vulnerabilities associated with the IP addresses. This could easily be done using port-scanning techniques. Once identified, cybercriminals could exploit those weaknesses to gain unauthorized access to the network or system. Additionally, by matching IP addresses to specific users, malicious actors could potentially launch targeted social engineering campaigns, and gather more sensitive information about an individual user, business, or the network.
A data breach of any company that provides ERP or data services can have severe potential long term consequences. Once data has been exposed online, companies should immediately implement incident response protocols and notify affected stakeholders, customers, and partners. I recommend any company which manages customer data to enhance their data security measures, conduct regular security audits, and implement the most up-to-date cybersecurity best practices.
I imply no wrongdoing by ClickBalance, nor do I claim that internal data or customer data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by ClickBalance would be able to identify this information along with any potential suspicious activity related to the breach. I publish my findings to raise awareness on issues of data security and privacy, hoping to contribute to a safer digital space for all.

Enterprise Resource Planning (ERP) Software Provider Exposed Millions of Records in Data Breach
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to Website Planet about a non-password-protected database that contained 769 million records belonging to ClickBalance — a software provider that offers multiple cloud-based business services for automating administration, accounting, inventory, payroll processes, and more.
![Clickbalance-data-breach-key-elements]() The publicly exposed database contained potentially sensitive information such as access tokens, API keys, secret keys, bank account numbers, tax identification numbers, and 381,224 email addresses. As a whole, the database contained 769,333,246 records with a total size of 395 GB. Upon further research, I identified that the records belonged to ClickBalance, one of Mexico’s largest Enterprise Resource Planning (ERP) technology providers. Upon discovery of the database, I immediately sent a responsible disclosure notice, and public access was restricted within hours. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from ClickBalance after my disclosure notice or at any time before publication.
ClickBalance offers Enterprise Resource Planning (ERP) software as a suite of cloud-based applications that organizations can access from anywhere and on any device. ERP tools are used to manage and automate various business processes across a range of different departments. These could include finance, human resources, supply chain, manufacturing, sales, among others. The overall purpose of an ERP system is to centralize data and give the user access to real-time information on a wide range of business operations.
Any technology company that manages a wide range of data of internal and external stakeholders including multiple customers, employees, and end users may face considerable data protection challenges. This is due to the large amount of information that they need to store for each customer — and they usually have a high number of customers. For instance, ERP, CRM (Customer Relationship Management), and CDM (Customer Data Management) systems are designed to track, manage, and monitor a wide range of data that can include financial records, personal customer data, employee details, and proprietary business data. This means that a data breach concerning any of these systems can expose potentially sensitive business information, which may bring about long-term operational and strategic risks. Unfortunately, when business or financial data is exposed, it is not known how it may potentially be used by cybercriminals years into the future.
The database contained API keys and secret keys in what appeared to be plain text. These keys can grant access to critical systems and potentially sensitive data. Hypothetically, cyber criminals could exploit exposed credentials to gain unauthorized access to applications, databases, and other services. This could create a serious risk of data theft, account takeovers, unauthorized transactions, or a wide range of service disruptions. Moreover, exposed keys pose numerous potential risks to an organization’s infrastructure and internal data. Protecting keys, tokens, and other administrative credentials with access controls and secure storage practices is highly important. I am not implying that customers or end users are at risk of any unauthorized use of API keys and secret keys. I am only providing a real-world example of how this information could possibly be used by malicious actors.
The exposure of hundreds of thousands of email addresses poses potential risks far beyond spam. According to research published by Deloitte, an auditing and accounting firm, 91% of all cyberattacks begin with a phishing email. This is one of the most common tactics used by criminals, and that is because it has a high success rate and does not require any technical expertise. When criminals have insider or nonpublic information, they can create very convincing deceptive emails to try and steal personal information, financial data, login credentials, and more. In this case, cyber criminals already know that these email addresses are business related and could potentially be used to launch targeted phishing attacks.
There are other risks associated with compromised emails. For instance, they could be used for spreading malware if the organization has lax security measures. Additionally, large collections of email addresses can be sold to other criminals on the dark web, greatly increasing the potential risks. I highly recommend that any organization that has experienced a data incident take protective measures, such as changing their passwords to new ones that meet complex password requirements. It is also a good idea to enable two-factor authentication (2FA) on their accounts. This is also recommended for customers and end users whose information may have been exposed in the breach. It is important to always be cautious of unsolicited emails or suspicious information requests.
The exposure of IP addresses poses numerous risks due to the nature of the services that ClickBalance provides. Although an IP address alone is a relatively low-risk piece of information that provides limited direct access, cybercriminals may still potentially use the IP address as a starting point to enable other malicious activities. Hypothetically, cybercriminals could attempt to find vulnerabilities associated with the IP addresses. This could easily be done using port-scanning techniques. Once identified, cybercriminals could exploit those weaknesses to gain unauthorized access to the network or system. Additionally, by matching IP addresses to specific users, malicious actors could potentially launch targeted social engineering campaigns, and gather more sensitive information about an individual user, business, or the network.
A data breach of any company that provides ERP or data services can have severe potential long term consequences. Once data has been exposed online, companies should immediately implement incident response protocols and notify affected stakeholders, customers, and partners. I recommend any company which manages customer data to enhance their data security measures, conduct regular security audits, and implement the most up-to-date cybersecurity best practices.
I imply no wrongdoing by ClickBalance, nor do I claim that internal data or customer data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by ClickBalance would be able to identify this information along with any potential suspicious activity related to the breach. I publish my findings to raise awareness on issues of data security and privacy, hoping to contribute to a safer digital space for all.
The publicly exposed database contained potentially sensitive information such as access tokens, API keys, secret keys, bank account numbers, tax identification numbers, and 381,224 email addresses. As a whole, the database contained 769,333,246 records with a total size of 395 GB. Upon further research, I identified that the records belonged to ClickBalance, one of Mexico’s largest Enterprise Resource Planning (ERP) technology providers. Upon discovery of the database, I immediately sent a responsible disclosure notice, and public access was restricted within hours. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from ClickBalance after my disclosure notice or at any time before publication.
ClickBalance offers Enterprise Resource Planning (ERP) software as a suite of cloud-based applications that organizations can access from anywhere and on any device. ERP tools are used to manage and automate various business processes across a range of different departments. These could include finance, human resources, supply chain, manufacturing, sales, among others. The overall purpose of an ERP system is to centralize data and give the user access to real-time information on a wide range of business operations.
Any technology company that manages a wide range of data of internal and external stakeholders including multiple customers, employees, and end users may face considerable data protection challenges. This is due to the large amount of information that they need to store for each customer — and they usually have a high number of customers. For instance, ERP, CRM (Customer Relationship Management), and CDM (Customer Data Management) systems are designed to track, manage, and monitor a wide range of data that can include financial records, personal customer data, employee details, and proprietary business data. This means that a data breach concerning any of these systems can expose potentially sensitive business information, which may bring about long-term operational and strategic risks. Unfortunately, when business or financial data is exposed, it is not known how it may potentially be used by cybercriminals years into the future.
The database contained API keys and secret keys in what appeared to be plain text. These keys can grant access to critical systems and potentially sensitive data. Hypothetically, cyber criminals could exploit exposed credentials to gain unauthorized access to applications, databases, and other services. This could create a serious risk of data theft, account takeovers, unauthorized transactions, or a wide range of service disruptions. Moreover, exposed keys pose numerous potential risks to an organization’s infrastructure and internal data. Protecting keys, tokens, and other administrative credentials with access controls and secure storage practices is highly important. I am not implying that customers or end users are at risk of any unauthorized use of API keys and secret keys. I am only providing a real-world example of how this information could possibly be used by malicious actors.
The exposure of hundreds of thousands of email addresses poses potential risks far beyond spam. According to research published by Deloitte, an auditing and accounting firm, 91% of all cyberattacks begin with a phishing email. This is one of the most common tactics used by criminals, and that is because it has a high success rate and does not require any technical expertise. When criminals have insider or nonpublic information, they can create very convincing deceptive emails to try and steal personal information, financial data, login credentials, and more. In this case, cyber criminals already know that these email addresses are business related and could potentially be used to launch targeted phishing attacks.
There are other risks associated with compromised emails. For instance, they could be used for spreading malware if the organization has lax security measures. Additionally, large collections of email addresses can be sold to other criminals on the dark web, greatly increasing the potential risks. I highly recommend that any organization that has experienced a data incident take protective measures, such as changing their passwords to new ones that meet complex password requirements. It is also a good idea to enable two-factor authentication (2FA) on their accounts. This is also recommended for customers and end users whose information may have been exposed in the breach. It is important to always be cautious of unsolicited emails or suspicious information requests.
The exposure of IP addresses poses numerous risks due to the nature of the services that ClickBalance provides. Although an IP address alone is a relatively low-risk piece of information that provides limited direct access, cybercriminals may still potentially use the IP address as a starting point to enable other malicious activities. Hypothetically, cybercriminals could attempt to find vulnerabilities associated with the IP addresses. This could easily be done using port-scanning techniques. Once identified, cybercriminals could exploit those weaknesses to gain unauthorized access to the network or system. Additionally, by matching IP addresses to specific users, malicious actors could potentially launch targeted social engineering campaigns, and gather more sensitive information about an individual user, business, or the network.
A data breach of any company that provides ERP or data services can have severe potential long term consequences. Once data has been exposed online, companies should immediately implement incident response protocols and notify affected stakeholders, customers, and partners. I recommend any company which manages customer data to enhance their data security measures, conduct regular security audits, and implement the most up-to-date cybersecurity best practices.
I imply no wrongdoing by ClickBalance, nor do I claim that internal data or customer data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by ClickBalance would be able to identify this information along with any potential suspicious activity related to the breach. I publish my findings to raise awareness on issues of data security and privacy, hoping to contribute to a safer digital space for all.
 The publicly exposed database contained potentially sensitive information such as access tokens, API keys, secret keys, bank account numbers, tax identification numbers, and 381,224 email addresses. As a whole, the database contained 769,333,246 records with a total size of 395 GB. Upon further research, I identified that the records belonged to ClickBalance, one of Mexico’s largest Enterprise Resource Planning (ERP) technology providers. Upon discovery of the database, I immediately sent a responsible disclosure notice, and public access was restricted within hours. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from ClickBalance after my disclosure notice or at any time before publication.
ClickBalance offers Enterprise Resource Planning (ERP) software as a suite of cloud-based applications that organizations can access from anywhere and on any device. ERP tools are used to manage and automate various business processes across a range of different departments. These could include finance, human resources, supply chain, manufacturing, sales, among others. The overall purpose of an ERP system is to centralize data and give the user access to real-time information on a wide range of business operations.
Any technology company that manages a wide range of data of internal and external stakeholders including multiple customers, employees, and end users may face considerable data protection challenges. This is due to the large amount of information that they need to store for each customer — and they usually have a high number of customers. For instance, ERP, CRM (Customer Relationship Management), and CDM (Customer Data Management) systems are designed to track, manage, and monitor a wide range of data that can include financial records, personal customer data, employee details, and proprietary business data. This means that a data breach concerning any of these systems can expose potentially sensitive business information, which may bring about long-term operational and strategic risks. Unfortunately, when business or financial data is exposed, it is not known how it may potentially be used by cybercriminals years into the future.
The database contained API keys and secret keys in what appeared to be plain text. These keys can grant access to critical systems and potentially sensitive data. Hypothetically, cyber criminals could exploit exposed credentials to gain unauthorized access to applications, databases, and other services. This could create a serious risk of data theft, account takeovers, unauthorized transactions, or a wide range of service disruptions. Moreover, exposed keys pose numerous potential risks to an organization’s infrastructure and internal data. Protecting keys, tokens, and other administrative credentials with access controls and secure storage practices is highly important. I am not implying that customers or end users are at risk of any unauthorized use of API keys and secret keys. I am only providing a real-world example of how this information could possibly be used by malicious actors.
The exposure of hundreds of thousands of email addresses poses potential risks far beyond spam. According to research published by Deloitte, an auditing and accounting firm, 91% of all cyberattacks begin with a phishing email. This is one of the most common tactics used by criminals, and that is because it has a high success rate and does not require any technical expertise. When criminals have insider or nonpublic information, they can create very convincing deceptive emails to try and steal personal information, financial data, login credentials, and more. In this case, cyber criminals already know that these email addresses are business related and could potentially be used to launch targeted phishing attacks.
There are other risks associated with compromised emails. For instance, they could be used for spreading malware if the organization has lax security measures. Additionally, large collections of email addresses can be sold to other criminals on the dark web, greatly increasing the potential risks. I highly recommend that any organization that has experienced a data incident take protective measures, such as changing their passwords to new ones that meet complex password requirements. It is also a good idea to enable two-factor authentication (2FA) on their accounts. This is also recommended for customers and end users whose information may have been exposed in the breach. It is important to always be cautious of unsolicited emails or suspicious information requests.
The exposure of IP addresses poses numerous risks due to the nature of the services that ClickBalance provides. Although an IP address alone is a relatively low-risk piece of information that provides limited direct access, cybercriminals may still potentially use the IP address as a starting point to enable other malicious activities. Hypothetically, cybercriminals could attempt to find vulnerabilities associated with the IP addresses. This could easily be done using port-scanning techniques. Once identified, cybercriminals could exploit those weaknesses to gain unauthorized access to the network or system. Additionally, by matching IP addresses to specific users, malicious actors could potentially launch targeted social engineering campaigns, and gather more sensitive information about an individual user, business, or the network.
A data breach of any company that provides ERP or data services can have severe potential long term consequences. Once data has been exposed online, companies should immediately implement incident response protocols and notify affected stakeholders, customers, and partners. I recommend any company which manages customer data to enhance their data security measures, conduct regular security audits, and implement the most up-to-date cybersecurity best practices.
I imply no wrongdoing by ClickBalance, nor do I claim that internal data or customer data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by ClickBalance would be able to identify this information along with any potential suspicious activity related to the breach. I publish my findings to raise awareness on issues of data security and privacy, hoping to contribute to a safer digital space for all.
The publicly exposed database contained potentially sensitive information such as access tokens, API keys, secret keys, bank account numbers, tax identification numbers, and 381,224 email addresses. As a whole, the database contained 769,333,246 records with a total size of 395 GB. Upon further research, I identified that the records belonged to ClickBalance, one of Mexico’s largest Enterprise Resource Planning (ERP) technology providers. Upon discovery of the database, I immediately sent a responsible disclosure notice, and public access was restricted within hours. It is not known how long the database was exposed or if anyone else gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive a response from ClickBalance after my disclosure notice or at any time before publication.
ClickBalance offers Enterprise Resource Planning (ERP) software as a suite of cloud-based applications that organizations can access from anywhere and on any device. ERP tools are used to manage and automate various business processes across a range of different departments. These could include finance, human resources, supply chain, manufacturing, sales, among others. The overall purpose of an ERP system is to centralize data and give the user access to real-time information on a wide range of business operations.
Any technology company that manages a wide range of data of internal and external stakeholders including multiple customers, employees, and end users may face considerable data protection challenges. This is due to the large amount of information that they need to store for each customer — and they usually have a high number of customers. For instance, ERP, CRM (Customer Relationship Management), and CDM (Customer Data Management) systems are designed to track, manage, and monitor a wide range of data that can include financial records, personal customer data, employee details, and proprietary business data. This means that a data breach concerning any of these systems can expose potentially sensitive business information, which may bring about long-term operational and strategic risks. Unfortunately, when business or financial data is exposed, it is not known how it may potentially be used by cybercriminals years into the future.
The database contained API keys and secret keys in what appeared to be plain text. These keys can grant access to critical systems and potentially sensitive data. Hypothetically, cyber criminals could exploit exposed credentials to gain unauthorized access to applications, databases, and other services. This could create a serious risk of data theft, account takeovers, unauthorized transactions, or a wide range of service disruptions. Moreover, exposed keys pose numerous potential risks to an organization’s infrastructure and internal data. Protecting keys, tokens, and other administrative credentials with access controls and secure storage practices is highly important. I am not implying that customers or end users are at risk of any unauthorized use of API keys and secret keys. I am only providing a real-world example of how this information could possibly be used by malicious actors.
The exposure of hundreds of thousands of email addresses poses potential risks far beyond spam. According to research published by Deloitte, an auditing and accounting firm, 91% of all cyberattacks begin with a phishing email. This is one of the most common tactics used by criminals, and that is because it has a high success rate and does not require any technical expertise. When criminals have insider or nonpublic information, they can create very convincing deceptive emails to try and steal personal information, financial data, login credentials, and more. In this case, cyber criminals already know that these email addresses are business related and could potentially be used to launch targeted phishing attacks.
There are other risks associated with compromised emails. For instance, they could be used for spreading malware if the organization has lax security measures. Additionally, large collections of email addresses can be sold to other criminals on the dark web, greatly increasing the potential risks. I highly recommend that any organization that has experienced a data incident take protective measures, such as changing their passwords to new ones that meet complex password requirements. It is also a good idea to enable two-factor authentication (2FA) on their accounts. This is also recommended for customers and end users whose information may have been exposed in the breach. It is important to always be cautious of unsolicited emails or suspicious information requests.
The exposure of IP addresses poses numerous risks due to the nature of the services that ClickBalance provides. Although an IP address alone is a relatively low-risk piece of information that provides limited direct access, cybercriminals may still potentially use the IP address as a starting point to enable other malicious activities. Hypothetically, cybercriminals could attempt to find vulnerabilities associated with the IP addresses. This could easily be done using port-scanning techniques. Once identified, cybercriminals could exploit those weaknesses to gain unauthorized access to the network or system. Additionally, by matching IP addresses to specific users, malicious actors could potentially launch targeted social engineering campaigns, and gather more sensitive information about an individual user, business, or the network.
A data breach of any company that provides ERP or data services can have severe potential long term consequences. Once data has been exposed online, companies should immediately implement incident response protocols and notify affected stakeholders, customers, and partners. I recommend any company which manages customer data to enhance their data security measures, conduct regular security audits, and implement the most up-to-date cybersecurity best practices.
I imply no wrongdoing by ClickBalance, nor do I claim that internal data or customer data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the database was publicly accessible, as only an internal forensic investigation conducted by ClickBalance would be able to identify this information along with any potential suspicious activity related to the breach. I publish my findings to raise awareness on issues of data security and privacy, hoping to contribute to a safer digital space for all.