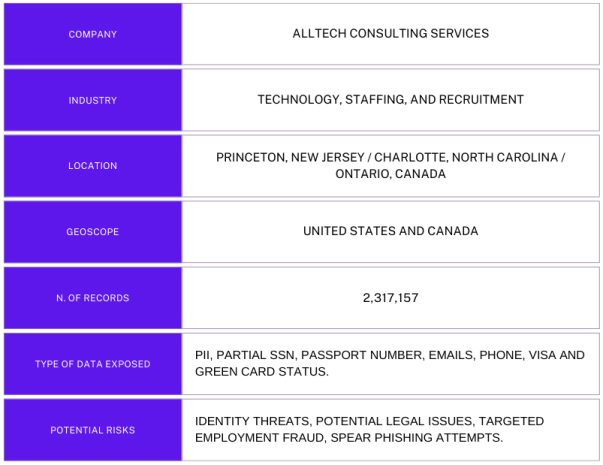
 The non-password-protected database contained a total of 2,317,157 records. The folder labeled as Documents enclosed the PII of an estimated 216k job seekers, including names, phone numbers, email addresses, the last four digits of their SSN, passport numbers, and whether they had a work authorization visa. The records also contained internal notes about their experience, qualifications, and type of job they are looking for.
The non-password-protected database contained a total of 2,317,157 records. The folder labeled as Documents enclosed the PII of an estimated 216k job seekers, including names, phone numbers, email addresses, the last four digits of their SSN, passport numbers, and whether they had a work authorization visa. The records also contained internal notes about their experience, qualifications, and type of job they are looking for.The records appeared to belonged to Alltech Consulting Services, a company based in New Jersey that provides job placement services for the technology and IT sector. According to their website, Alltech works with more than 1,000 companies to connect them with IT and engineering professionals. I immediately sent a responsible disclosure notice of my findings, and public access to the database was restricted the following day. I did not receive a reply to my disclosure notice. Although the records indicated the files belonged to Alltech, it is not known if they managed the unencrypted database or if it was managed by a third party. It is also unknown how long the records were exposed or if anyone else accessed them, as only an internal forensic audit can identify that information. Some of the records contained employer details such as names, company names, email addresses, and phone numbers. The files also contained worker information such as salary expectations, work history, and whether they were willing to relocate. Many of the applicant files indicated if the individual held an H-1B visa. This is a non-immigrant visa that allows U.S. companies to employ foreign workers in specialty occupations that require technical expertise, typically in fields like IT, engineering, and healthcare. This detailed information combined with internal notes could signify additional potential risks if they were to fall in the hands of cyber criminals. It is estimated that there will be nearly 377,500 computer and IT job vacancies each year from 2022 to 2032. Those working in the tech industry earn some of the highest wages of any occupational group. According to some estimates, the average yearly salary for tech employees is above $100,000. For comparison, the median annual salary for all jobs in the United States was $48,060 in 2023. These high-earning professionals could potentially be valuable targets for cyber criminals. When data such as passport numbers and partial SSNs are exposed, they can provide a puzzle piece to create a more complete profile of those individuals. Once criminals have the personal details and information they need (such as employment history, education, and salary data), they could attempt targeted spear phishing campaigns to obtain additional information or financial details. I am not saying that Alltech Consulting’s clients are at risk, I am only stating the real-world risks of employment scams, which have been on the rise. It is estimated that in the U.S. as much as $737M was lost due to fake job offers between 2019 and 2023. According to the Federal Trade Commission (FTC), job and employment scams were up 110% in 2023 compared to 2022, when jobseekers reported losing an estimated $367 million. The statistics show that criminals are successfully stealing millions of dollars through fake job offers, consulting services, and other fraudulent fees. These losses amount to an average of $12,000 per victim — and there’s no sign of how to solve the problem. So far, the only solution is to remain vigilant and look for suspicious warning signs. I recommend that jobseekers be skeptical of any recruiter or agency that requests upfront fees, credit card information, or personal information (such as SSN or passport numbers) as a condition for the application. Do your research on the agency and the company offering the job to make sure that it is legitimate. Remember that if the offer sounds too good to be true, it usually is. In a limited sample from the database, I saw a large number of individuals indicating that they are H-1B visa holders. These workers could be at additional risk due to the strict rules and terms of their status or employment. The H-1B holders are required to obtain job sponsorship, which could potentially make them more vulnerable to employment scams. If criminals are offering fake job opportunities that promise visa sponsorship, the victim could be more likely to provide personal details or pay fees because the job is connected to their ability to stay and work in the U.S. Additionally, criminals could hypothetically use the exposed data of work visa holders to launch targeted immigration-related scams. This could include impersonating government officials, immigration lawyers, or recruiters to extort money with the false promise of resolving immigration issues. These incidents could potentially put H-1B visa holders at risk and create legal problems when renewing their visa or submitting permanent residency applications. I am not saying that individuals using Alltech’s services are at risk of any scam or fraudulent activity, I am only providing information that H-1B visa holders should be aware of for educational purposes.
This exposure of nearly a quarter million individuals highlights the critical importance of data security, particularly when handling sensitive personal employment information that may not be intended to be publicly accessible. In the wrong hands, this data could potentially provide criminals with a working list of high value targets that could be used for fraudulent employment offers or phishing attempts.
While access to the database was eventually restricted, the full extent of the exposure remains unclear without an internal forensic audit. When companies collect and store large amounts of data or potentially sensitive information, it is critical to ensure that proper access controls are implemented. I also recommend organizations conduct regular penetration tests and make sure software, plugins, or other systems are updated.
I imply no wrongdoing by Alltech Consulting Services, their partners, associates, agents, or third-party contractors, nor do I claim that internal data or customer data was ever at risk or could be misused. The hypothetical data-risk scenarios I have presented in this report are exclusively for educational purposes, and it is crucial for all readers to conduct their own independent security assessments to verify the accuracy, completeness, and reliability of data protection measures. As an ethical security researcher, I do not download the data I discover and only take a limited number of screenshots solely for verification purposes. It is not known how long the files were publicly accessible, as only an internal forensic investigation conducted by Alltech Consulting Services or the owner of the database would be able to identify this information along with any potential suspicious activity related to the breach. I do not conduct any activities beyond identifying the security vulnerabilities and notifying the relevant parties, and I disclaim any and all responsibility for actions taken by third parties or others that may be taken as a result of this disclosure. I do not conduct any unauthorized actions, exploit the vulnerabilities, or engage in any activities that would compromise the data further. I publish my findings solely to raise awareness on data security and privacy issues.