Originally published on November 17th, 2020
Company name and location: TronicsXchange, Inc based in California, US.
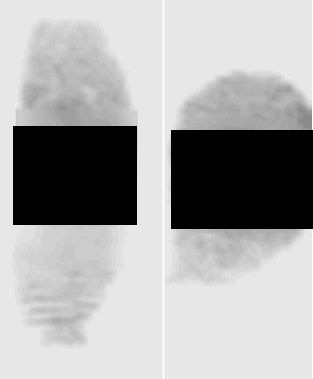
Leak size: Over 2.6 million files (including 80,000 identification photos and approximately 10,000 fingerprint samples).
Number of people exposed: 80,000+
Data Storage Format: AWS S3 Bucket
Countries Affected: United States
A US-based used electronics seller with retail operations has exposed its customers’ data due to a lack of security measures. The company was previously operating under the name of GreenElectronicsExchange (GEEx) and later renamed TronicsXchange.
In the course of conducting a random scan for server vulnerabilities, the Website Planet research team discovered that TronicsXchange’s AWS S3 Bucket was left unprotected. Further investigation led our team to determine that the company had suffered a devastating breach that exposed 2.6 million files – potentially the company’s entire customer database – although, this has yet to be confirmed.
Leaked Customer Data
Most of the exposed information was contained in .png, .jpg and .gif image files and included Personally Identifiable Information (PII) data such as:
- Driver’s licenses
- IDs
- Fingerprints
- Selfies
- Photos of electronics obtained from mobile devices
- Receipts
- Shipping labels including full address information
More specifically, as a result of government-issued driving licenses being stored in image format, TronicsXchange allowed multiple instances of PII to be exposed including:
- Full name
- Date of birth
- Photograph of license holder
- Home address
- Date of issue
- Date of expiration
- Gender
- Hair Colour
- Eye Colour
- Height and weight
- Place of issue
- Driver’s license class
- ID and Driver’s License Numbers



Who was affected?
The bucket exposed mostly Californian residents that visited TronicsXchange stores in different shopping centers (malls) in California and bought or sold electronic equipment between 2012-2015.
In 2015, the company ceased all operations including its online and retail presence.
Who Was Leaking the Data?
TronicsXchange is an American company with retail operations, buying and selling used electronics including mobile phones, tablets, laptops and cameras. Customers could attend TronicsXchange retail stores to sell their used electronics equipment in exchange for immediate cash payments, as well as, buy used devices and repair devices.
According to the company, its existing network of kiosks in shopping malls saw “millions of shoppers every year” with the company adding that malls served as the most “convenient” location to run its electronics exchange business.
Customer Impact
It is currently unknown how extensive the leak was, including how many unauthorized parties were able to access the leaked data (if any). If the data was obtained by malicious hackers, there is severe risk of identity fraud and various other scams being perpetrated against the individuals exposed by the leak.
TronicsXchange’s misconfigured bucket contained an extensive set of personal information including personal identifiable information that can be harnessed by nefarious hackers to cause severe financial, social and reputational damage to those affected by the leak.
Furthermore, given the fact that government-issue documents were exposed, nefarious users could potentially conduct identity fraud across different platforms and institutions. Users’ true likenesses, copies of official documentation and contact details could be harnessed to conduct identity theft.
Credit Card Fraud and Identity Theft
Identity theft is a form of fraud whereby a nefarious user steals personal information such as someone’s legal name, date of birth and physical address – in order to assume that identity in legal form and conduct financial scams for profit.
User details are typically used to open a bank account, sign up for credit cards, or apply for official documents.
The clear and present danger for individuals is that becoming the victim of credit card fraud or identity theft is extremely damaging, both financially and reputationally. Moreover, victims of identity fraud experience negative repercussions for a considerable time after their experience because credit history remediation is time-consuming, while financial intermediaries cannot guarantee the full restoration of lost funds.
Status of the Data Breach
Our team discovered the vulnerability on 12 October 2020 and disclosed all its findings to Amazon AWS on 14 October 2020. Our team attempted contacting TronicsXchange, but were unsuccessful considering the company’s listed email address was invalid and its website was offline. Upon conducting a follow-up check on 20 October 2020, the bucket was found to be adequately secured.
Protecting Your Data
In this particular case, there was little TronicsXchange customers could have done to protect themselves. The most important thing they could have done is wipe their devices of all information before selling their phones to TronicsXchange. Stronger precautions could include insisting on redacting portions of the document, especially the address and other unique numbers or digits.
Fingerprints are typically never requested by retail outlets, or even large commercial stores. Therefore, if asked to provide fingerprints when conducting a routine sale at a retail store, customers should be wary and consider searching for alternative proprietors. It was the company’s policy to obtain customer information including ID checks, but such data must be kept in adequately secure conditions including encryption and password protection.
For added peace of mind, customers may choose to obtain professional ID and credit history protection/remediation services offered by the likes of Equifax, Experian and TransUnion.
How and Why We Report on Data Breaches
Website Planet is an entity that seeks to help its readers stay safe when using any website or online service. However, given that most data breaches are never discovered or reported by the affected companies, conveying current risk information can be problematic. As a result, we seek to identify existing online vulnerabilities that are putting people at risk, to better prepare them for the risks they face online.
As an organization, we follow the principles of ethical hacking and we always work within the remit of the law. We only investigate unsecured and unprotected databases that were discovered at random. We never target specific companies and we always report all our findings to the appropriate authorities, including the affected companies themselves.
By reporting these leaks, we help to make the internet safer for everyone.
What is Website Planet?
Web designers, digital marketers, developers, and businesses with an online presence rely on Website Planet as their primary resource. Our platform offers valuable tools and resources catering to both beginners and experts. We also provide updates on the latest advancements in cybersecurity while maintaining a strong commitment to honesty and transparency – our utmost priorities.
We have an experienced team of ethical security research experts who uncover and disclose serious data leaks as part of a free service for the online community. This has included a vulnerability in Donald Trump’s 2020 campaign app and in a Hotel reservation platform exposing sensitive data.
Read about how we tested five popular web hosts to see how easily hackable they are, here.