Over half (65%) of burglaries happen when you aren’t home, according to the FBI and the US Department of Justice.
Now, how many accounts do you have online that you’re actually never using?
Around 87, according to a research by NordPass on 1509 users.
These are called ‘orphaned accounts’, and they are like a house left empty all day, every day––Hacker heaven. The risk is even higher if you have a website with external providers working on it.
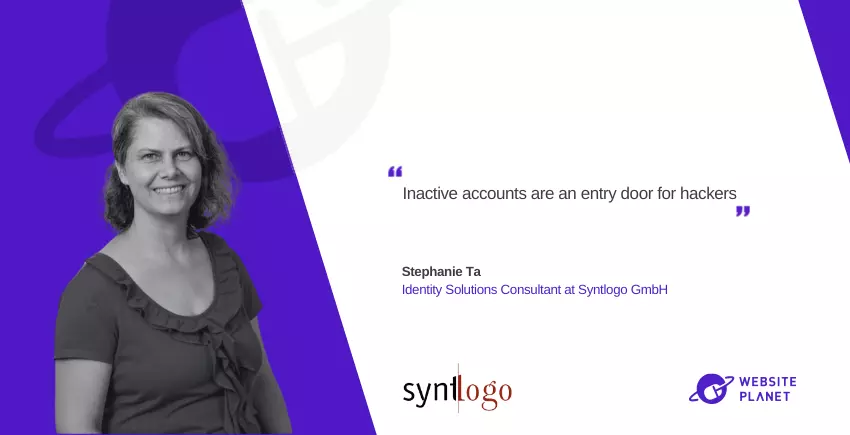
Stephanie Ta, Identity Solutions Consultant of Syntlogo GmbH and 9+ years experience in the field of Identity and Access Management (IAM), has joined Website Planet to explain why orphaned accounts are more dangerous than you probably think, and how website owners and users can proactively protect themselves from its risks.
What are orphaned accounts in IAM, and how do they occur?
An orphaned account is an account left inactive by an employee, vendor or user for a prolonged period of time that still has access to applications and systems. Orphaned accounts arise for a wide variety of reasons.
Duplicate accounts
Users create duplicates, for example, when they open a new account because they have forgotten the password for the old account, or their e-mail address has changed. If it is not a simple process to reset the password as part of a self-service, then there are very many users who simply create a second account.
Changes in the status of employees or external users
Another reason is that the user is no longer part of the team or company as an employee. This is one of the biggest cyber risks, which is why hackers find an easy entry point. Especially, when users take the same password for multiple accounts.
The status of external supplier or partner accounts can change very quickly, and for a variety of reasons:
- The project has ended, but the service account still exists.
- An employee of the external service provider is working for another project or is no longer part of the company.
- Changes in company ownership or structure can lead to inactive accounts if not properly managed
Dormant accounts
Consumers or other users may no longer need access to a protected web application. One-off purchases are a classic example of this. But there are also other reasons, e.g. if the user has chosen an alternative supplier or another service but has not deleted the account with their old provider.
EDITOR’S NOTE
Orphaned accounts can lead to substantial financial losses through data breaches, loss of customer trust, and compliance penalties.
For example, Regal Investment Advisors was fined $1.9 million for neglecting orphan accounts while continuing to charge fees for services that were not provided.
A study by Veritas Technologies on 13,000 consumers around the world also revealed that nearly half (47%) would stop buying from a company if it was failing to monitor and remove unnecessary data.
How can website owners handle dormant accounts?
Prevent double accounts
The monitoring of inactive accounts is a task for the operator or owner of the protected web application. But even before that, one should prevent the creation of double accounts.
Double accounts are an entry door for hackers. Allow users to use their e-mail address only once. Never allow the creation of a second account with the same e-mail address.
Don’t skip the housekeeping
Some users may have additional e-mail addresses, which is why a process named “Housekeeping” should be carried out regularly. And here we are at the management of these accounts. Depending on the business model of the web application, users shall have shorter or longer access to their accounts.
For example, in the e-commerce business, an account is unused if the period between two orders is longer than one or more years. In this case, an Identity & Access Management system detects unused accounts, automatically sends e-mails to these accounts stating that the account will be deleted within one month if there is no activity within the next four weeks.
Ensure the right to be forgotten
This is an important feature to enhance cyber security. Users can administer their accounts independently as part of a self-service. It is important that the user can quickly find the relevant functions and operate them intuitively. For example, they can download or port the account data or use the “right to be forgotten” in accordance with the General Data Protection Regulation.
What are the best tools to help with all of that?
There are efficient tools and functions within Identity and Access Management systems, which can build the central source of identity data when working with multiple protected applications. The control about the status of the accounts is at one central place.
When you are working with one Content Management System, meaning only one application, you may control manually if accounts are inactive or unused for a longer period.
In the case of longer inactivity or users who don’t need access anymore, you shall delete or lock these accounts.
Do you have any specific tips for users?
- Delete your superfluous, unused accounts
- Don’t use the same passwords for different accounts
- Enable MFA or passwordless authentication like Passkeys, whenever possible.
And remember: a user-friendly and comprehensive self-service enables a GDPR-compliant account-life-cycle.
You have the right (and should) to complain with your web app provider if the management of your account is confusing or if important features for account management are missing. Don’t accept GDPR inconsistent processes or missing functions, which disables you from full control of your data.
And what are your tips for providers?
There are some valuable concepts for web applications to prevent a major cyber breach:
- Multi-Factor Authentication (MFA) / Passwordless Authentication
- Anomaly Detection and Adaptive Authentication
- Detection and Deletion of Ghost or Unused Accounts
- Separating Authentication from Authorization
- Splitting authorities to comply with the Zero Trust principle
That’s for prevention, but what to do if I suspect any account has been compromised?
Check the typical pages where you can find out if your account is compromised.
Change your password only in this case, when you find out that your account is leaked. I don’t recommend changing it on a regular basis.
At the same time, it is important that providers immediately block hacked accounts in their systems.
How can our readers connect with you?
LinkedIn: https://www.linkedin.com/in/stephanie-ta-645aa32/
Websites:
- https://www.syntlogo.de/en/
- https://login-master.com/en/