The Exposure Provides a Look Behind the Scenes of the Controversial Business of Autodialing.
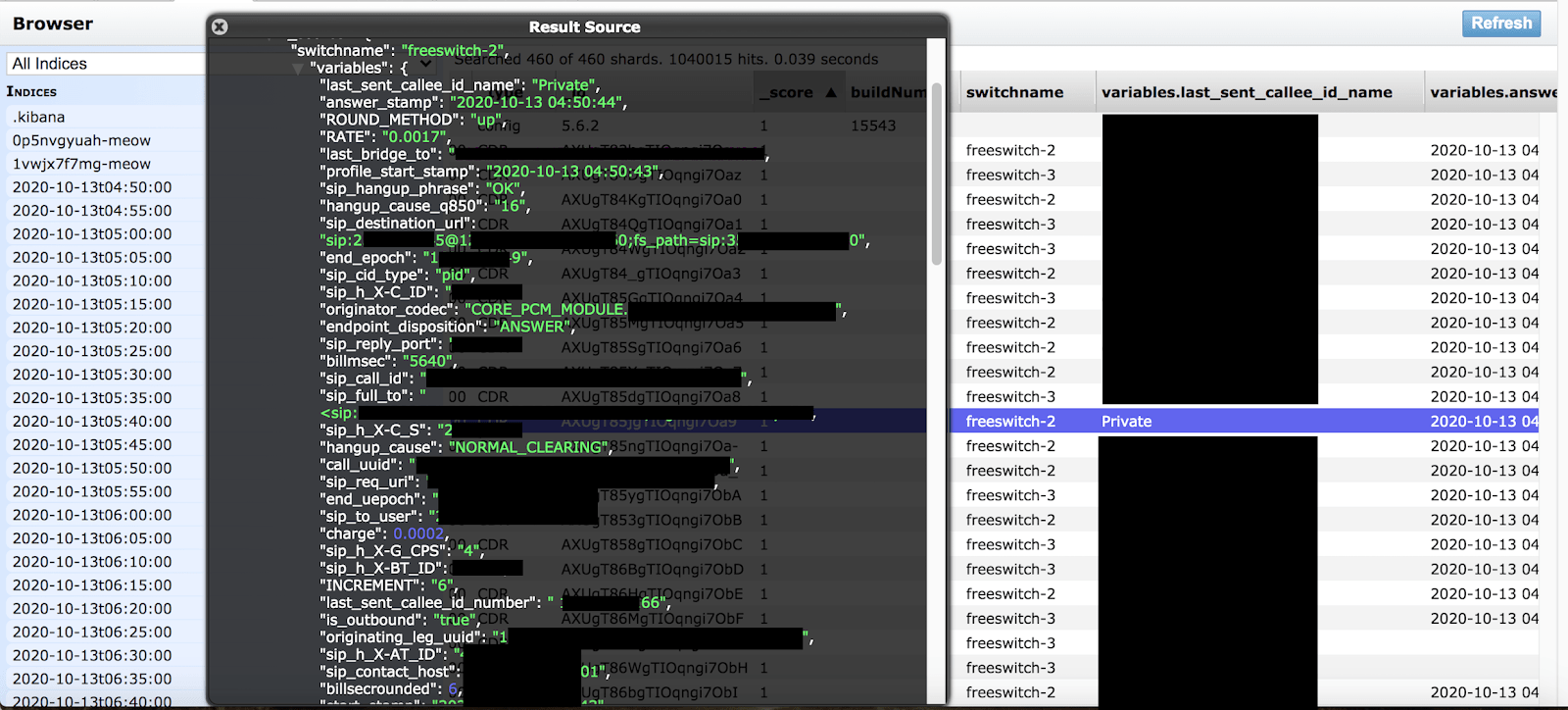
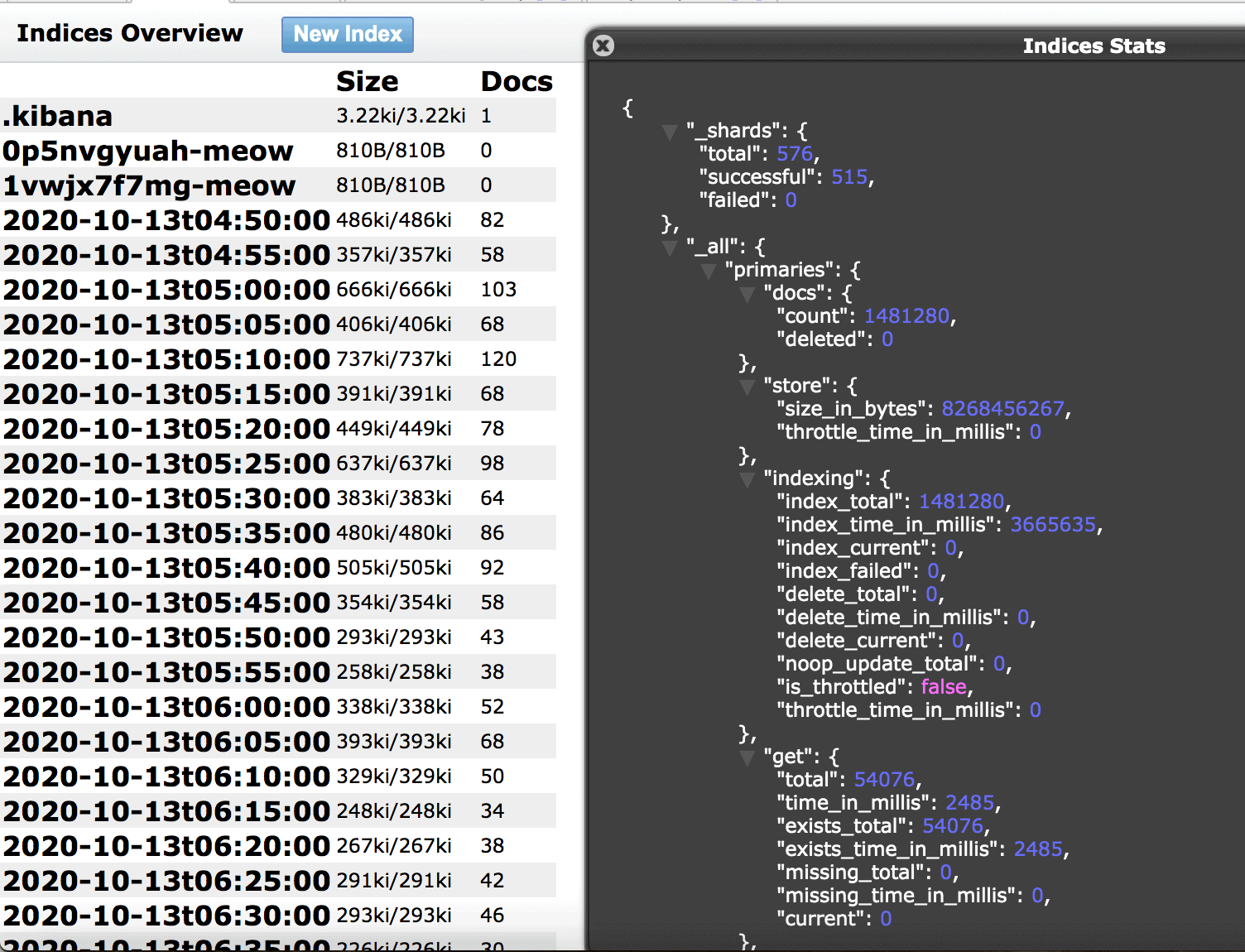
- 1,481,280 calls made in 24 hours that included logs, exposing outgoing call data, and incoming phone numbers
- Details about how the calls are made and caller ID numbers
- The database updated every 5 min with real time call logs and internal settings such as IPs and VOIP configuration settings
- Calls were made to US based receivers in multiple states on behalf of a wide range of companies including debt collectors, medical insurance, investments, and more.
On October 14th 2020 the WebsitePlanet research team in cooperation with Security Researcher Jeremiah Fowler discovered a non-password protected database that contained a large number of phone call records and VOIP related data. The dataset was exposed for a little more than 24hours and was growing in real time with thousands of calls being made per hour. In the time from when I found the database to when it was secured it logged 1.48 million robocalls in a just over a day. Nearly all calls were outgoing, but the system also logged when someone called back a number that appeared on their caller ID. The database and records belonged to a company called 200 Networks, LLC based in Reno, Nevada. We immediately sent a responsible disclosure notice of our findings and 200 Networks restricted public access shortly after.
Robocalls, a disliked practice
There are few things in life that make people as angry as robocalls. According to a recent report Americans received an estimated 58 billion calls in 2019 up 22% from the 47.8 billion in 2018. The Federal Communications Commission (FCC) says that 60% percent of all the complaints they received in 2018 was due to robocalls.
The worst part about many of these calls is that they can come from anywhere in the world using something called a voice over internet protocol (VOIP). The callers often use a method called “spoofing” to make the caller ID number appear to be a local number. When a person gets a call and they see a local number they often answer it thinking it is someone they know or an important call only to answer and discover it is a debt collector or sales call.
If you have ever received a robocall you already know that usually when you call the number back it is either disconnected or in use by a person who has no idea their number was used by an autodialer. The fact that these calls can be so anonymous is what makes robocalls so mysterious and disliked at the same time. Most of the time it is virtually impossible to trace a spoofed phone call and figure out where the calls originate from.
Of course, law enforcement and phone providers have some tools at their disposal to try and figure out where these calls come from, but it is a game of cat and mouse with the ever-changing technology and calling methods. The autodial technology makes it very cheap and easy to launch a massive robocall campaign and oftentimes these companies will hide the caller’s identity in the process. This is what makes my latest discovery so interesting.
Our findings
While trying to identify the owner of the dataset I saw multiple references to Inteliquent connected to multiple IP addresses used for calling. There were a number of consumer complaints posted online about Inteliquent and spam calls. My next logical step was to reach out to Inteliquent about my discovery. They were very helpful and pointed me in the right direction of how to identify the owner of the dataset. It should be noted that Inteliquent is not a telemarketer and does not provide or use telemarketing services. Inteliquent provides wholesale telecommunications services, including telephone numbers, to other telecommunications carriers, service providers, and resellers who use those services to provide their own wholesale or retail telecommunications services. I assume 200 Networks, actual owner of the server, was using their technology and it is possible that these complaints came from individuals who falsely identified the true source of the calls.
This discovery was a close look inside the industry and shows exactly how the calls are made, managed, and logged. This data leak publicly exposed the inner workings of the process including Trunk and SIP configurations, numbers, caller ID records, and much more. These calls were logged as inbound or outbound and there were detailed records of if the person answered the phone or hung up, how long they were on the phone, and if they were forwarded on using a tier system. Session Initiation Protocol (SIP) protocol is what enables VOIP calling. The bigger problem is that SIP is not secure and can be easily hacked because it is a text-based protocol similar to HTML and in the process can expose information about the caller’s device and other details about how the call is made.
One extremely interesting finding was that when I discovered the dataset the first thing that I did was search my own number and there were zero results. An hour later after calling multiple numbers and blocking my own number using the *67 feature, my phone number appeared. In North America phone providers allow the *67 service code that blocks your phone number display and provides you with the privacy of hiding your phone number for the call that is being made. However, I saw that my calls and real phone number were logged and recorded. This is a wakeup call for anyone who thinks that the *67 Caller ID Blocking protects your privacy by not displaying your phone number when you call back suspicious numbers.
What the database contained:
- This database was non-password protected, open and visible in any browser (publicly accessible) and anyone with bad intentions could edit, download, or even delete data without administrative credentials. (As a security researcher I never bypass or circumvent password protected assets).
- 1,481,280 total records accessible that continued to grow until access was restricted. Updating the logs every 5 min.
- Exposed records that contained internal information, SIP, Caller ID, call pathways IPs and Ports.
- Caller ID (spoofed or masked) numbers in the form of the IP address and then phone number and “Destination Numbers” of the recipients. It should be noted that the outbound caller ID numbers all went back to what I am assuming was 200 Networks’ customers or a voicemail system
- I was able to validate a large sampling of phone numbers back to debt collection services, Health Benefit Advisors (insurance sales), and multiple other mystery services that only told me to leave my personal info for an agent to callback.
- The database was at risk for ransomware and there was evidence of an automated Meow bot attack.
- Middleware and build information that could allow for a secondary path for malware. (Middleware is software that connects the operating system and the applications together; it is often called “software glue”. If there are vulnerabilities or exploits in the middleware it can be a backdoor into the network).
- Technical records such as IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to potentially access deeper into the network.
The potential risks of a data exposure like this include the possibility to do something called “phreaking”. This is a very old term that describes hacking a traditional phone service to make free long-distance calls. Modern day phreaking would involve gaining full access to the VOIP service provider’s network without them ever knowing. Cyber criminals could not only get ‘free’ access to the calling network, they also try to intercept information from the calls such as billing or payment information, sensitive business data, medical or other personal information, voicemails, and the list goes on.
We want to clarify that 200 Networks has not experienced or fallen victim to Phreaking. Instead, we are exclusively highlighting the potential security challenges that modern phone technologies may encounter both today and in the future. Typically, VOIP calls employ a distinctive IP address, and it’s noteworthy that SIP information is seldom encrypted, rendering this a genuinely significant security concern.
The law can’t keep up with the speed of technology
It is unclear if any of these numbers they were calling were on the Do Not Call Registry. The FCC allows citizens to check whether your number is on the Do Not Call Registry but you must call from the number you want to verify, so I was unable to validate if these numbers were in violation. Robocalls and spoofing have become such a problem that In 2009 the US Congress passed the Truth in Caller ID Act, FCC rules prohibit anyone from transmitting misleading or inaccurate caller ID information with the intent to defraud, cause harm or wrongly obtain anything of value with penalties of up to $10,000 for each violation. An anti-robocall bill passed Congress overwhelmingly and was signed by the President on December 31, 2019.
As annoying as robocalls are, it is not illegal to make a massive amount of calls as long as they comply with the law. I am not implying any wrongdoing by 200 Networks or their customers and only highlighting my discovery while raising awareness of how the industry is using technology to make millions of calls each day. 200 Networks allows their users to make robocalls or autodialed calls using a range of features including customized voice recordings, menu selection, and routing options that would forward to an answering machine or to a live agent.
It should be noted that the outbound numbers I called back were an IP call that appeared to be masked or spoofed using a real number as an “alias”. Meaning that if you called the number back you would reach an agent or a voicemail belonging to what I assume would have been a customer of 200 Networks. These numbers were also assigned by geolocation or prefix as the numbers that were being called. For example, if a Texas number was called the outbound caller ID would be from a Texas area code. In a 2020 FTC filing 200 Networks LLC applied for “Authorizing of Numbering Resources”. I can only assume that this allowed them to use legally assigned phone numbers to be in compliance with the law and have a full range of area codes.
According to their website “200 Networks is a leading provider of cloud-based voice and messaging technology for enterprises, contact centers, BPOs, and collection agencies worldwide. 200 Networks serves various Fortune 500 companies and enterprises in multiple industries including newspaper, collection, education, healthcare, automotive, political, customer service, and marketing”.
200 Networks acted fast and professionally to secure the database immediately after my responsible disclosure notification. I received an email reply thanking me for the details of my investigation and the notification. The database was openly accessible to anyone with an internet connection and it is unclear who else may have had access to the records from the time of my discovery until when the data was secured. This is yet another reminder that companies big and small who collect and log data to ensure they encrypt those records and take the proper cyber security safeguards.
Originally published on March 25th, 2021