90% of cyber attacks use a fake email to gain access to your business. Retruster allows employees to know if incoming mail is legit, so they can stay protected from malware, phishing and ransomware that can cost the organization hundreds of thousands of dollars. To get to the bottom of this, I sat down for a video call with Retruster CEO Michael Snape, who explained what phishing emails look like and what can be done to stop them coming in.
Please describe your background and the company’s background. What sparked the idea, and how has it evolved so far?
My story is essentially the story of the company. I was working in the finance department of a large commerce company. We received an email from our CEO to say there was a new opportunity and money needs to be transferred. Of course, it turned out that email was fake. When we looked into it, we realized how easy it was to fake an email. We also realized that this is happening all over the world. There’s no reason to rob a bank and put your life at risk when you can just send a fake email with no consequence whatsoever. It’s super easy and that money disappears immediately so why shouldn’t you do it?
It turns out that this problem has only grown as data has become more valuable. As our world has moved more online, this problem has become massive.
Furthermore, what started as just small incidences of financial fraud has grown both in terms of the financial scope and the volume of attacks. Emails are the main way of delivering malware, ransomware, data breaches and data exfiltration, accounting for about 98% of cyber attacks. We realized the majority of security issues that organizations are facing can be solved upstream if you secure the email vector. If you can do that, you’re solving so many issues downstream. Unfortunately, email is something that exposes a large part of the organization, because everyone uses it. If I send a phishing attack to the CEO or the CIO, it’s often just as dangerous as sending a phishing attack to the newest intern that started yesterday.
For example, we recently started working with a bank. The reason they came to us is that one of the branch staff had opened up an email and had given someone their credentials, and now someone outside of the organization has got full access to their entire internal architecture, and they can move laterally within that system. That’s just a disaster that would have been solved if that bank had Retruster in place.
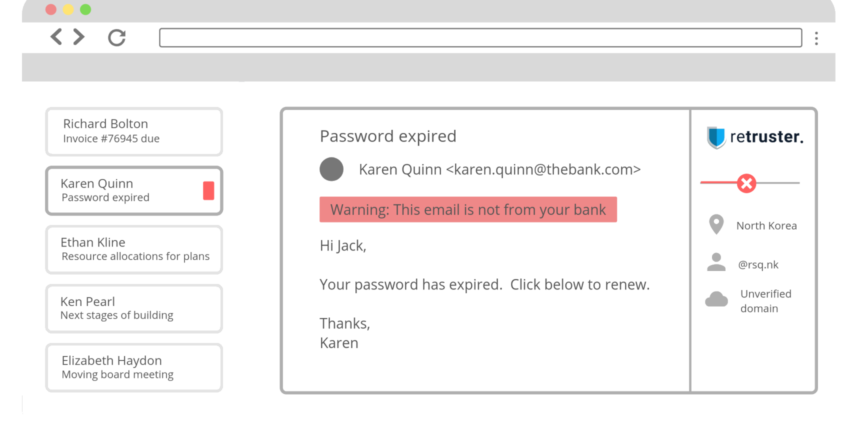
That’s essentially our mission: to secure companies from the number one threat, which is email. The way we decided to do it is very different from the vast majority of current solutions on the market. Most companies use a solution that tries to stop as many emails on the server level as possible before it gets through to the users. That’s only 70% effective, so we are right there next to the user. We will warn them about any email that comes in that looks a little bit suspicious. There’s no question of emails getting through that look fine but are dangerous. A little bit later we’ll talk about why that’s become more of a problem.
What kind of threats are people being exposed to via email?
Firstly, there are different types of malware. Once malware gets deployed into your system, often by clicking on a link in an email, the attacker can essentially do whatever they want. They can take data and sell it on the dark web, or shut you down and demand a ransom in exchange for releasing your data.
All those things have implications both from a financial aspect, and from a data security aspect, not to mention the regulatory issues, from GDPR to the privacy laws in California, and so on.
Can you imagine someone now has all of your passwords and all of your sensitive information? Often, people don’t even know that malware is sitting within one system until days, weeks, and sometimes even years later.
The typical example is you get an email that looks like it’s from Netflix, Amazon, or your bank, and it says, please update your account. You put in your account details and then you’re redirected to the real page, but by then, that person already has your details.
From a business perspective, we see a lot of supply fraud and credential fraud, where a business will get an email saying “our suppliers changed their banking details, please pay into this account”. The next payment goes into that account and obviously, the money disappears.
Almost all cybersecurity threats that organizations face come through the email area, so that’s essentially where that threat lies, even going forward.
What would you say are the most fundamental things to consider when building a business security strategy?
I think software, education, and awareness are the three most important things, and let me break that down.
On the software side, the first thing is taking a multi-layered approach. There isn’t one product out there that is a silver bullet and will solve all your security issues. It’s important to have antivirus in place; It’s important to make sure that all of your software is patched and up to date; And it’s important to have specific anti-phishing and anti-spam software. All of these things are part of a multi-layered approach, which I think is the way forward in terms of cybersecurity.
Of course, all of that has to be allied with education and users should be seen as partners, not as threats. If you can educate your users, that’s very important, but education alone isn’t something that can be relied on. There are quite simplistic tools out there that simulate phishing attacks. Often, employees will think, “oh, I’ve got this, I can now spot phishing attacks”, but that can’t be relied on. Again, that’s part of the multilayer approach that we feel is very important.
The current situation is that things have changed a lot. We’re all working from home and workforces are distributed. That brings other threats into play. Coronavirus is an excellent example where employees are getting fake emails from HR. When people are panicking, they are more likely to make silly decisions that they wouldn’t have made usually. I think being aware of where your employees are, where your business is, and what the general macro environment looks like are all important parts of a holistic security strategy.
How should users go about choosing their email security products?
Firstly, we cannot rely exclusively on the tools that we currently have. Especially in the email security space, a lot of the tools grew out of anti-spam filters. If you look at the big names, many of them started as anti-spam tools, so essentially, they are based on signatures and on classifying certain email types as threats. They are great for traditional threats, but not so great for new threats because those haven’t been classified yet.
So I think it is about being very aware of what new technology is out there, what people are saying about that technology, comparing technologies, looking at reviews and seeing what’s often bought together and what works well together. All those things are really important when it comes to attacks of the future, which are the ones that we need to be scared about.
Which trends or technologies do you find to be particularly intriguing these days?
Anything that’s in the machine learning and AI space is really interesting because that way, we’re moving away from a rules-based approach towards a big data technology-based approach. Obviously it’s going to be a lot better at identifying threats before they even happen. We’ll be able to plug in massive data sets and reach far better results than what humans can do in terms of setting up rules or filters or anything like that. I believe that is the future.