Inside this Article
What are the advantages and disadvantages of self-hosting a website compared to using a hosting provider?Downtime can be costly for businesses. What measures should website owners take to minimize downtime, and how do hosting providers contribute to this?In the age of mobile-first indexing, how does the choice of web hosting affect a website's mobile performance and search engine ranking?Can you explain the significance of server location in web hosting, and how it impacts website speed and user experience?How do hosting providers address the growing concern of data privacy and compliance with regulations like GDPR in their services?What role do server monitoring and performance optimization play in web hosting, and how can businesses ensure their websites run efficiently?How does the choice of web hosting affect website loading times and what strategies can be employed to optimize website speed?What are the key considerations for businesses when migrating a website from one hosting provider to another, and what challenges should they anticipate?How do you foresee the evolution of web hosting in the context of emerging technologies like blockchain and decentralized applications (DApps)?What are the security implications of using WordPress CMS systems, and how can hosting providers help enhance CMS security?What are the challenges and solutions for hosting and securing e-commerce websites, particularly in the context of online transactions and sensitive customer data?How do website builders with built-in hosting services compare to traditional web hosting, and in what scenarios are they ideal?
What are the advantages and disadvantages of self-hosting a website compared to using a hosting provider?
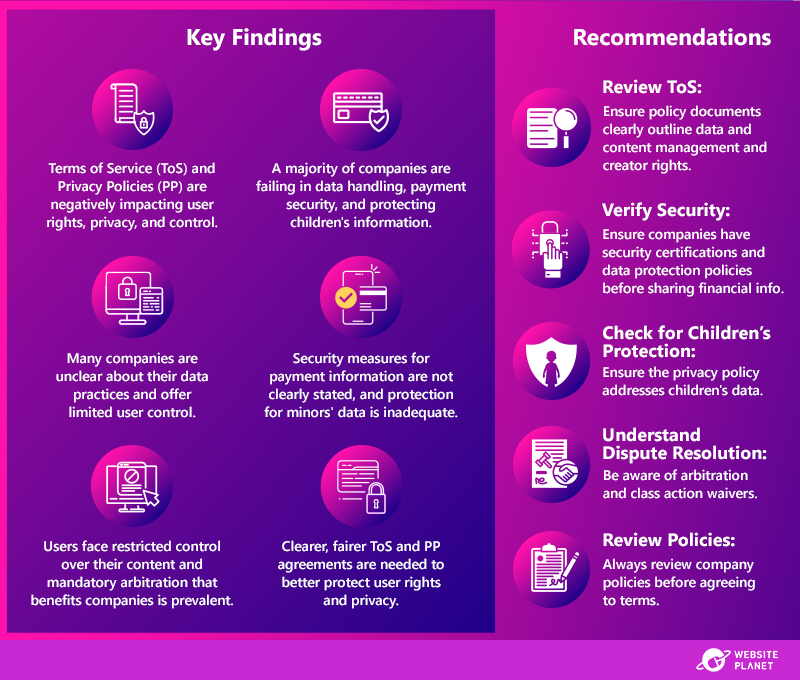
Self-hosting gives ultimate control so everything can be set up exactly as you like, but with all that power comes responsibility – it’s on you to make sure everything is constantly available, updated, secure, and performing to its capability. A hosting provider will have experience in doing this for thousands upon thousands of websites every day, including holidays when you’d rather be enjoying yourself with friends and family. They will understand the intricacies of configuring Nginx to ensure that your website is fast, how to make sure the latest PHP vulnerability doesn’t expose your confidential data to hackers, and how to make sure your site doesn’t become the source of millions of spam emails annoying people around the world. Daniel Foster, Managing Director of 34SP.com / 34SP.comDowntime can be costly for businesses. What measures should website owners take to minimize downtime, and how do hosting providers contribute to this?
Downtime minimization is the result of effective cooperation between site owners and their hosting providers. At DNHOST, we always put the customer first and continue to go the Extra Mile, because every customer deserves it. So, we minimize downtime in order for your site to always remain online and serve your visitors. Update your Site Regularly An updated site is a safe & online site. The more often a site’s CMS or code is updated, the less problems it will face from either cyberattacks or loading problems. Also, at DNHOST we offer Patchman which performs automatic patching of security vulnerabilities. Choose a reliable Hosting Provider State-of-the-art Hardware, trustworthy Datacenter and continuous monitoring of the server’s physical hosting environment (temperature, power supply, etc.) is the triplet that will keep your site online. So don’t hesitate to ask your hosting provider for a detailed report on their infrastructure and security protocols. At DNHOST, we constantly renew our hardware & choose wisely the Datacenters we use around the world to ensure that your site will always remain online. Cyber Protection training of your personnel Even if just one computer connected to your site’s management system is hacked, your security is at risk. So, you should train your personnel based on a cyber security protocol about safe passwords, safe browsing, etc. As an extra measure of safety, at DNHOST we offer a premium spam filter to protect you against phishing attacks and perform continuous audits so that we can inform you on time about users who use insecure passwords or make insecure use of our services. Use of Effective WAF The Web Application Firewall will prevent those who want to gain access to your server and possibly shut down its operation. As an extra security measure, we offer a firewall with custom rules on the server to protect it from malicious hackers who, nevertheless, have managed to gain access. Backup & Disaster Recovery Frequent backups and a disaster recovery infrastructure will bring a crashed site back online in minutes. As an extra security measure, we keep backups of our customers’ sites offline. Ioannis Farazoumis, CEO of DNHOST / dnhost.grIn the age of mobile-first indexing, how does the choice of web hosting affect a website’s mobile performance and search engine ranking?
The choice of hosting has a significant impact on the website’s performance on mobile devices and its position in search engine results. There are a few things to keep in mind when ensuring your good position in Google rankings. Page load speed is one of the most important issues. By placing a site on low-performance hosting, you risk drops in Google’s rankings and, as a result, a lower website visit rate. Choosing poor-quality hosting also exposes us to numerous unavailability of the site due to failures, which is noted by indexing robots as another factor that causes the website to lose its position in Google. The location of the hosting server can also affect loading times for users in different regions. If the hosting server is far away from your target audience, this can increase latency and slow down access to your site for mobile users in that region. Consider hosting your site on a server that is geographically closer to your target audience for better performance. To further speed up your site’s load time, consider a provider that allows simple setup with Cloudflare. This ensures that your site’s content is delivered from the server closest to the user, which is especially important in an era of heavy travel with mobile devices. It’s a good idea to make sure that your hosting provider offers support for SSL, which encrypts data between the user’s device and the server. This not only increases security, but can also positively affect your Google ranking. Search engines score sites that use this type of security better. You can check the website’s performance yourself. There are many ways to do this. One of the most popular and simplest is to perform a test using GTMetrix.com. All you have to do is enter the address of the site you want to analyze, and you will get a detailed report with tips on what to improve. We can get a report tailored directly to mobile devices using the free GoogleSpeed Insights tool. Rafał Kuśmider, Founder & CEO of dhosting.pl / dhosting.plCan you explain the significance of server location in web hosting, and how it impacts website speed and user experience?
With modern infrastructures, the location of the server often no longer plays a role. New generations of processors, hard drives, memories, caches, and supporting software, combined with high-speed Internet connections, make it possible for almost any website to be accessed quickly enough from anywhere in the world. However, there is a significant difference from continent to continent, which can be measured as 1-2-3-4 or even 5 seconds depending on the provider. With worse solutions, a delay in the site’s response can be seen, and the user can simply give up viewing the site if this experience takes a long time. The biggest mistake is when a company operating in Europe rents hosting in the USA or in Japan… the speed is often not obvious, but the difference is there. There are companies that have servers all over the world and serve their website from the closest location to the visitor. Of course, this solution is not financially sustainable for everyone, while there are also companies that do not need this solution at all because they focus their business on a specific territory. That is why we have a range of servers in Europe, the USA and Asia. Customers can combine or rent a server in a specific location they target. Miloš Stanić, CEO of AdriaHost / adriahost.rsHow do hosting providers address the growing concern of data privacy and compliance with regulations like GDPR in their services?
Data privacy and compliance are paramount today more so for across the internet and for hosting companies like ourselves, heavily depended on by our customers to provide the infrastructure necessary for their web and digital needs. Ultahost ensures data privacy and GDPR compliance through rigorous measures. We employ robust encryption protocols to safeguard data both in transit and at rest. Our data centers adhere to strict physical security standards. We’ve implemented granular access controls to restrict data access to authorized personnel only. Additionally, regular audits and compliance checks are conducted to maintain GDPR compliance. We also provide tools and resources for our customers to align with GDPR when using our services, making it a shared responsibility. Transparency is key, so we are open about our data handling practices in our privacy policies and terms of service. Elin Doughouz, CEO of UltaHost / ultahost.comWhat role do server monitoring and performance optimization play in web hosting, and how can businesses ensure their websites run efficiently?
For us at SSD Nodes, both server monitoring and performance optimization are pivotal in the realm of web hosting, working together to ensure websites run efficiently. For businesses similar to ours, seeking a strong online presence, the following components are essential for maintaining high performance and user satisfaction. ➢ Server Monitoring: we make sure to set in place real-time tracking and analysis of various server metrics, including CPU usage, memory consumption, disk space, network traffic, and response times. Its significance lies in:- Issue Detection: At SSD Nodes, real-time monitoring allows us to early detect any potential problems such as performance bottlenecks, security breaches, or hardware failures. This proactive approach helps us mitigate issues before they impact the website’s availability.
- Resource Management: Monitoring provides our engineers insights into resource usage patterns. This data helps hosting providers and businesses make informed decisions about resource allocation, ensuring the website has the necessary computing power to deliver optimal performance, especially during traffic spikes.
- Availability and Reliability: Consistent monitoring ensures our servers at SSD Nodes, are always available and responsive. This is critical for our business, as website downtime can result in lost revenue and damage to brand reputation.
- Load Balancing: It is primordial to distribute incoming traffic across multiple servers, which prevents overload, ensuring consistent performance even during traffic spikes.
- Caching: We rely as well on caching mechanisms to store frequently accessed data, reducing the need for dynamic content generation and significantly speeding up page loading.
- Content Delivery Networks (CDNs): CDNs helps us distribute our sites’ content across global servers, reducing latency and accelerating content delivery to users worldwide.
- Code Optimization: Our SSD Nodes’ developers enforce well-structured and efficient code writing, minimizing server’s resource consumption and accelerating page rendering. This includes optimizing database queries, images, and scripts.
- Database Optimization: Last but not least, we ensure to streamline database queries, indexing, and table structure improving data retrieval speed and reducing page load times.
How does the choice of web hosting affect website loading times and what strategies can be employed to optimize website speed?
The choice of web hosting affects website loading times in several ways. Firstly, the type of web hosting you choose will determine the amount of resources you have available for your website. Shared hosting plans, for example, share the resources of a server with other websites. This type of hosting is the most popular for websites of all types, but if your website becomes popular and has a large number of visits you will need Evaluate VPS, CLOUD, or DEDICATED plans as they offer exclusive resources for your website. Secondly, the web hosting provider you choose can also influence loading times. Web hosting providers that offer high-speed servers and good network infrastructure can help ensure that your website loads quickly. Additionally, there are a number of things you can do to optimize your website’s loading speed, such as:- Choose a suitable web hosting as we already mentioned.
- Optimize images. Images can be an important part of a website, but they can also be a major cause of slow loading. You can optimize images by reducing their size and compromising.
- Optimize the code. Your website code can influence loading speed. You can optimize the code by removing unnecessary code and optimizing existing code.
- Use a content delivery network (CDN). A CDN is a network of servers that store your website files around the world. This can help improve your website’s loading speed for visitors who are far from your servers.
What are the key considerations for businesses when migrating a website from one hosting provider to another, and what challenges should they anticipate?
When considering the migration of a website from one hosting provider to another, businesses must carefully assess several key considerations to ensure a smooth transition. Our blog “Website Migration: Why Everyone Fears It and How We Handle It at vshosting~” sheds light on these considerations and the challenges associated with them. One of the primary concerns during migration is the evaluation of the current hosting partner. Businesses should critically assess the performance and reliability of their existing provider, identifying any recurring issues such as downtime or limitations that may be driving the decision to migrate. Understanding the reasons behind the migration is crucial for effective planning. The text emphasises the challenges inherent in website migration, particularly the downtime and risks associated with data transfer. Acknowledging these challenges is essential for businesses to be adequately prepared for the potential disruptions during the migration process. A significant obstacle is the need for changes in the application or technology. Migration often necessitates adjustments to ensure compatibility with the new hosting solution. This may require the involvement of the development team, posing a challenge, especially for smaller projects that might lack dedicated development resources. Outdated technologies present another hurdle to migration. Running applications on unsupported or obsolete technologies, such as PHP 5.2, not only complicates the migration process but also exposes the website to security risks. There is huge importance in updating applications to current, fully supported versions to mitigate these risks. Compatibility with the new hosting solution is a critical consideration. Businesses need to ensure that their current applications align with the technology of the chosen hosting provider. This is particularly relevant when transitioning to advanced infrastructures like clusters, where adjustments and learning new technologies may be required. Service windows and downtime are inevitable aspects of migration, causing temporary disruptions to website functionality. Planning for these service windows and minimising their impact on the business, especially for large projects, is crucial. The text suggests careful timing and thorough testing of the new solution before migration to prevent complications that could prolong downtime. Choosing an experienced hosting provider is emphasised as a key decision. Providers with a track record in migration can effectively analyse and test the new hosting infrastructure, minimising potential risks. In conclusion, businesses contemplating website migration should consider the performance of their current hosting partner, understand the challenges associated with migration, address necessary changes in application or technology, update outdated technologies, ensure compatibility with the new hosting solution, plan for service windows and downtime, and choose an experienced hosting provider. Thorough planning and consideration of these factors will contribute to a successful and less disruptive migration process. Damir Špoljarič, Co-Founder & CEO of vshosting / vshosting.euHow do you foresee the evolution of web hosting in the context of emerging technologies like blockchain and decentralized applications (DApps)?
Globally, blockchain technology and DApps have not had much of an impact on hosting. However, integrating emerging technologies like edge computing, AI, and IoT with blockchain is poised to change this, potentially leading to more efficient data processing and improved user experiences in web hosting. Decentralized applications use blockchain, meaning all interactions between DApps and hosting occur via blockchain. This reliance on blockchain brings new security opportunities and challenges. The decentralized nature of blockchain offers enhanced data security and privacy but also necessitates the development of new security protocols specifically for decentralized web hosting environments. In the case of blockchains based on proof-of-the-work, they mostly run on mining, leading to the niche development of mining data centers, utilizing either ASICs or powerful servers/GPU servers. This has correspondingly increased the demand for GPU servers, previously used mainly for complex rendering, mathematics, and big data. Now, half of the GPU market comprises clients operating their blockchains, full nodes, etc. However, many still host servers at home and do not use web hosting providers in order to minimize costs, as blockchains for many tasks do not require 100% uptime of nodes. Despite the hype and trends, blockchain has not greatly affected the web hosting industry as a whole. It has mainly increased the demand for individual positions, marking a sideline from regular web hosting. Additionally, many clients make first landings for crypto products, selling the same servers used for classical tasks, indicating a trend of new crypto applications. Many hosting providers have started accepting cryptocurrency. For example, we have developed a cryptoprocessor with open-source code – SHKeeper of non-custodial type for receiving payments in various cryptocurrencies. Globally, the adoption of blockchain in web hosting varies across different industries and regions. This uneven adoption highlights both the potential and challenges of blockchain in web hosting. Moreover, the environmental impact of blockchain, especially proof-of-work models, is a growing concern. Sustainable and energy-efficient solutions are being explored, including the development of greener blockchain technologies and the use of renewable energy sources in hosting infrastructures. In conclusion, the evolution of web hosting, influenced by blockchain technology and decentralized applications, signifies a transformative phase in the industry. While its current impact is nuanced, the potential for profound changes looms large. As web hosting intersects with advanced technologies like AI, IoT, and edge computing and grapples with challenges in security, market dynamics, and environmental sustainability, we are poised to witness a paradigm shift. This shift promises not only technological advancements but also a redefinition of hosting models, user experiences, and industry standards. The journey ahead for web hosting, amidst these evolving technologies, is one of innovation, adaptation, and forward-thinking strategies, shaping the future landscape of the internet and digital services. Vyacheslav Smyrnov, CEO of Virtual Systems / vsys.host – shkeeper.ioWhat are the security implications of using WordPress CMS systems, and how can hosting providers help enhance CMS security?
WordPress has become one of the most targeted CMS systems for attacks due to its popularity. This is due to its open-source nature and the ability for third-party developers to intervene in the system with numerous plugins and themes. In other words, if a plugin developer leaves a security vulnerability, it can create a weakness in the system even if there is no security vulnerability in the WordPress core. This makes it a prime target for malicious individuals who use bots to scan for such plugins and themes on websites. In recent years, the WordPress CMS system has become so versatile that it can easily be transformed into an e-commerce site with just a few plugins, making websites more vulnerable to attacks. During this time, hosting service providers have taken a series of security measures to prevent such incidents. I would like to list some of the measures that can be taken to protect user data:- Isolating Websites: Isolating websites from each other protects the others when one site is infected with malicious software. Verify if your hosting provider uses CloudLinux, an operating system that provides user isolation. CloudLinux ensures this with a special kernel and OS packages.
- Imunify360 Security Software: Imunify360 can quickly prevent emerging security vulnerabilities even if you haven’t updated your website. It identifies and blocks malicious IP addresses and bot entries.
- Intrusion Detection (IDS) and Intrusion Prevention Systems (IPS): IDS and IPS can help prevent potential attacks, password trials, and phishing attacks.
- WP-Toolkit WordPress Tools: These tools regularly scan your website and plugins. They notify you of potential security vulnerabilities via email and can automatically update your site. These tools are often added as third-party software to control panels like cPanel and Plesk and have useful free versions.
- Keeping Software and Operating System Updated: Regularly updating server-side operating systems, packages, and services is crucial. This action fixes known security vulnerabilities. Also, make sure your hosting provider does not display PHP and Web Server banner information to the public, as specific software versions may have security vulnerabilities.
- Using SSL Certificates: Using an SSL certificate prevents eavesdroppers on shared networks from stealing your login information. Hosting providers often offer this service for free. You just need to redirect your site to the HTTPS protocol.
- Two-Factor Authentication (2FA or MFA) for Hosting Control Panels, Customer Panels, or WordPress Admin Panel: Using two-step verification methods can prevent unauthorized access.
- Monitoring for SQL Injection and XSS Vulnerabilities: Tools like Apache Mod Security can monitor and prevent almost 99% of such attacks. It’s important to keep rule sets updated regularly to protect against new security vulnerabilities. Organizations offer both free and paid, professional feeds for this.
- Email Security: Ensuring email security provides a high level of protection against social engineering and data theft attacks. Instead of opening attached files immediately, it’s a good practice to check their trustworthiness. Scanning them on platforms like virustotal.com is a useful practice.
- Preventing Weak Passwords: Preventing the use of simple and common passwords is crucial. It’s one of the most common vulnerabilities. Just as you wouldn’t leave your house key under the doormat, you shouldn’t use a simple password.
- Monitoring WP-Login and XMLRPC Access: It is essential to monitor access to these two critical files on WordPress sites. If a large number of unsuccessful login attempts are made, the IP address is usually blocked for a certain period.
- Keeping Log Records: Keeping log records for at least 365 days can provide clues about the behavior of attackers in case of intrusion attempts. Many website owners put their sites back online without addressing the security vulnerability, only to face the same result. In some cases, the backdoor left by the attacker may even be found within backups.
- Backups: Regularly backing up your data is the only way to recover from a compromised or data loss situation. Hosting companies often take daily or weekly backups and store them for several weeks.
- CloudFlare Proxy System: The CloudFlare proxy system includes specially developed IPS, IDS, and WAF systems. If you are unsure whether your company has taken security measures for WordPress CMS systems, you can provide these measures for free using CloudFlare.
What are the challenges and solutions for hosting and securing e-commerce websites, particularly in the context of online transactions and sensitive customer data?
We have several challenges daily for our customer’s server and website security. It’s an evolving process that takes constant learning and testing. Listed below are the main challenges and how we typically solve them. We work on all of these challenges with new and tested processes we learned over the years which helps streamline most of the process between all servers.- Challenge: Transmitting sensitive data securely.
Solution: Implement SSL/TLS protocols for encryption. - Challenge: Protecting payment information.
Solution: Use PCI DSS-compliant payment gateways, and avoid storing payment data locally. - Challenge: Identifying vulnerabilities.
Solution: Conduct regular security audits and patch vulnerabilities promptly. - Challenge: Ensuring authorized access.
Solution: Implement strong authentication and access controls. - Challenge: Protecting against data loss.
Solution: Perform regular backups and test restoration procedures. - Challenge: Keeping software up to date.
Solution: Regularly update and patch all software components. - Challenge: Detecting security incidents.
Solution: Implement monitoring and intrusion detection systems. - Challenge: Mitigating user-related risks.
Solution: Educate users on security best practices.