Inside this Article
What the Exposed Database Contained:
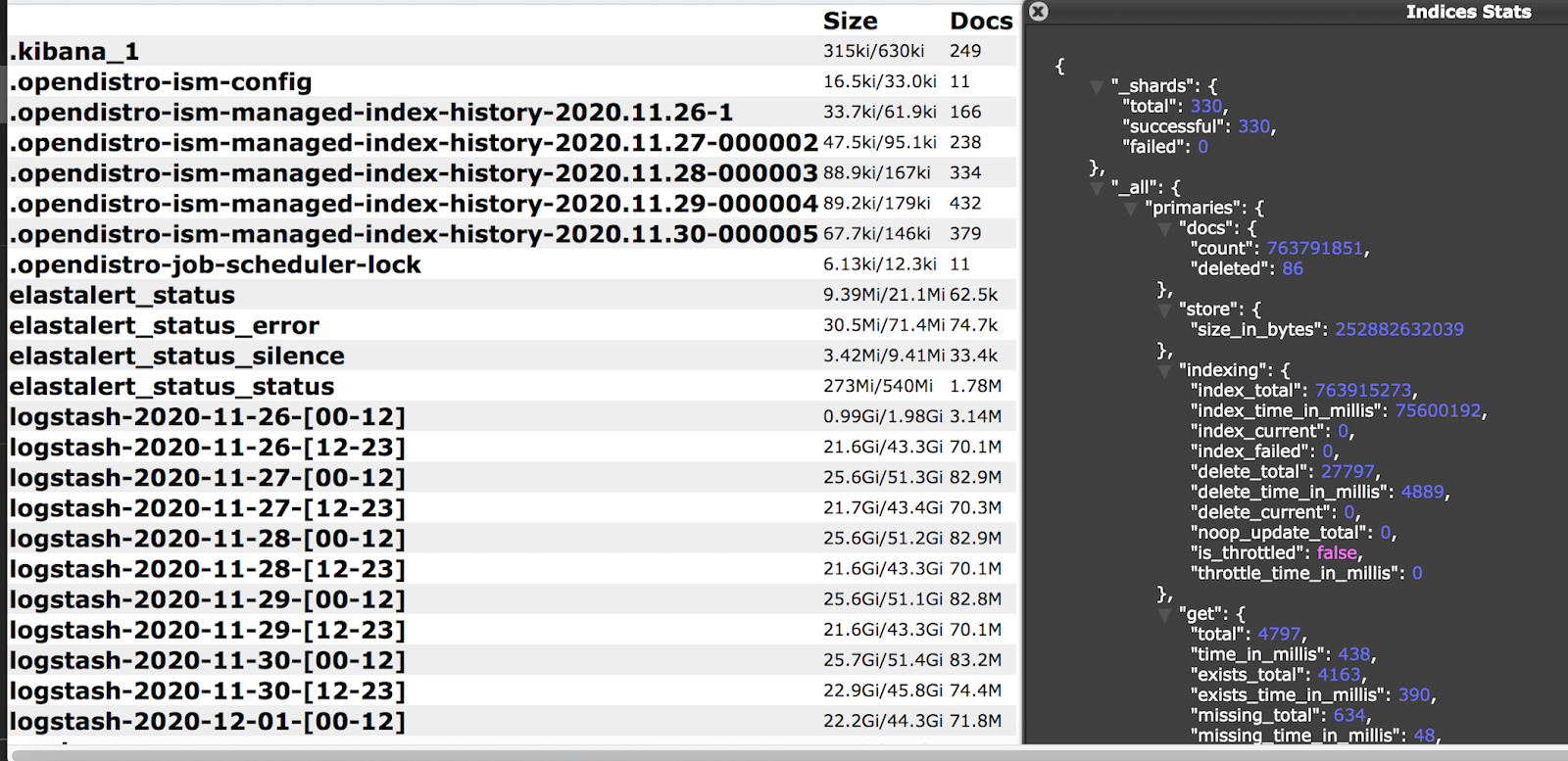
- The total size of the database was 477.95 GB and contained 1,507,301,521 (1.5 Billion) records.
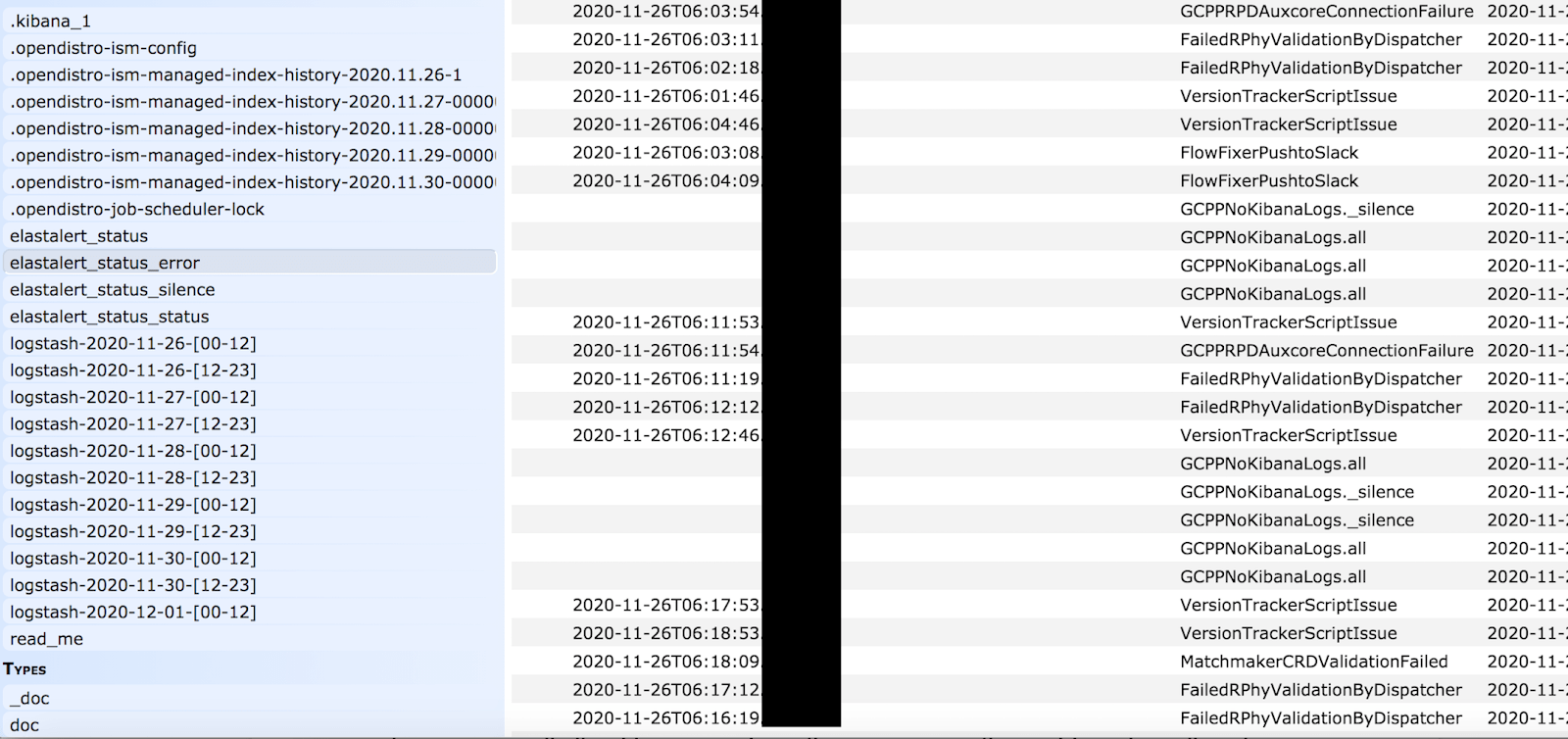
- There were a large number of remote and internal IP addresses, node names and other details that could provide a blueprint for internal functionality, logging, and overall structure of the network. Even if it is a non-production environment it potentially mirrors the primary data structure and could hypothetically expose how the monitoring works or provide clues to where customer or production data is stored.
- In addition to the technical logs above mentioned, the server exposed email addresses and hashed passwords of Comcast’s Development team. As well as error logs, alerts, and job scheduling records that revealed cluster names, device names and many internal rules and tasks that were marked “Privileged =True”.
- Finally, were found IP addresses, Ports, Pathways, and storage information that cyber criminals could potentially exploit to access deeper into the network. Error logs also identified middleware that could also be used as a secondary path for malware or other vulnerabilities.

Accidental Data Sharing
Following my disclosure to Comcast, I have been somehow included in an internal email thread where someone accidentally attached “access logs and cluster samples”. This email put 14 attachments in my inbox that were intended for internal communications regarding the incident. I immediately knew this was an unintentional and honest mistake. As a legitimate Security Researcher I highly value ethics and integrity when it comes to data protection. I did not open the attached compressed files and I did not see what they contained. Shortly after that, I received another email telling me they had made a mistake by sending me those documents and I confirmed that I would not access those records.Comcast Validated the Discovery and Closed Access Fast
As soon as we were confident that the data belonged to Comcast we immediately sent a disclosure notice and reported our findings. In less than an hour the database was closed to public access and I received a reply from their Security Defect Reporting team. I must admit this was among the fastest response times I have ever had. Comcast acted fast and professionally to restrict the data set that was accessible to anyone with an internet connection. The following day I received confirmation that this data did indeed belong to Comcast and that a limited number of employees were affected (development team). In a reply a member of the Comcast Product Security Incident Response Team (PSIRT) told me that this data was used for internal development and testing. The email attachments were an accidental data exposure that also highlights how important it is to make sure internal team members do not “reply to all”. To the best of my knowledge there was no customer data to cross reference or validate and I have no reason to doubt that this was not a development environment despite the massive number of records. In my experience I have had countless organizations tell me that the records I found were dummy data despite evidence that they were not. In this case I saw records marked as “Development” and “Privileged”. I am not implying that this was production data or any wrongdoing by Comcast and only highlighting my discovery to raise awareness that even development records can expose potentially sensitive information about the internal network systems, configuration settings, and much more. In today’s world all data is valuable and must be securely protected.Comcast is the Biggest Player in the Game
Comcast provides residential and commercial services in 40 states, and is the largest cable TV company and largest home Internet service provider in the USA. Critics have long blamed Comcast for high prices and lack of competition in the industries they operate in and although the Federal Trade Commission says there is competition many consumers feel differently. I have personally lived in areas where there were no other cable or broadband providers to choose from. According to Electronic Frontier Foundation an estimated 68 million American households do not have access to broadband or just one internet service provider. Americans pay more for data than anywhere else in the world. The cost of broadband in the US is nearly double what consumers pay in the UK, Europe, Korea, or Asia. Comcast has swallowed up the competition along the way to provide customers with broadband internet, phone, cable television, broadcast television stations, filmed entertainment, theme parks and much more. Some of the well known brands under the Comcast umbrella include Xfinity, NBC Universal, Sky broadcast and telecommunications, DreamWorks Animation, and XUMO streaming services.Emerging Threats and Past Incidents
As recent as 2018 Comcast Xfinity had a data incident that exposed the home addresses and social security numbers of more than 26.5 million users. In 2015 Comcast paid a settlement of $33 Million for leaking thousands of unlisted phone numbers. In 2014 Comcast suffered an insider attack when an employee gave 2 unauthorized individuals access to a remote-administration tool. They stole an estimated 24.5 million individuals’ personally identifiable information (PII). In this incident anyone with an internet connection was able to see behind the scenes of how Comcast logs errors, job tasks, permissions, middleware they use to connect their infrastructure and much more. The real threat would be social engineering of the development team to obtain credentials or other confidential information about Comcast’s network. Exposing what middleware is being used could also provide a secondary path for malware. Middleware is the software glue that helps applications work together but it usually requires the never ending job of security patching and updates. Every day, the ever-changing landscape of technology, along with updates and security gaps, poses growing risks to any company or organization. Moreover, one must not underestimate the potential for external attacks or insider threats. A company of Comcast’s size faces a significant responsibility in safeguarding their digital assets, given the array of services and technologies they provide.Originally published on February 1th, 2021