Company name and location: Civicom Inc., located in the USA
Size (in GB and amount of records): 100,000+ files, over 8TB
Data Storage Format: AWS S3 bucket
Countries Affected: USA
The Website Planet security team uncovered a data breach affecting the B2B conferencing service Civicom Inc.
The US firm, which specializes in online video conferencing, left its Amazon S3 bucket open and accessible, without proper user authentication procedures in place. As a result, Civicom’s bucket exposed over 100,000 video and audio files belonging to its customers.
These files extensively document meetings between employees of the client businesses using Civicom’s platform. Civicom’s breach could damage a number of businesses with sensitive company data included in the bucket’s content.
Customer Data Exposed
In total, Civicom Inc.’s misconfigured AWS S3 bucket exposed 100,000+ files, equating to over 8TB of data. The data belongs to businesses that are clients of Civicom.
We identified four separate datasets which were categorized based on the file extensions present on Civicom’s bucket. These datasets exposed the content of client meetings:
- Videos of meetings
- Clipped Highlights
- Audio recordings
- Audio Transcripts
Thousands of hours of video and audio recordings, along with hundreds of written transcripts, expose the private conversations of Civicom’s clients.
Among these conversations, many businesses have likely discussed:
- sensitive company data (including possible market research calls);
- trade secrets; and
- intellectual properties.
It’s worth mentioning that numerous client businesses have staff members with information exposed on the bucket.
Exposed PII of Civicom clients’ employees includes:
- full names; and
- images of employees’ faces and bodies.
The bucket was live and being updated at the time of discovery, and has been live since February 2018. Amazon is not responsible for the management of Civicom’s bucket and this data breach is not Amazon’s fault.
Videos of meetings were recorded and uploaded to Civicom’s bucket. Many videos of meetings were between one and two hours long, though, some videos were shorter or longer than this time frame. A number of videos were also recorded with a 360° camera.
Clipped highlights are another form of video exposed on the server. These videos show the most important snippets of information discussed in meetings. You can see screenshots of each video type below.

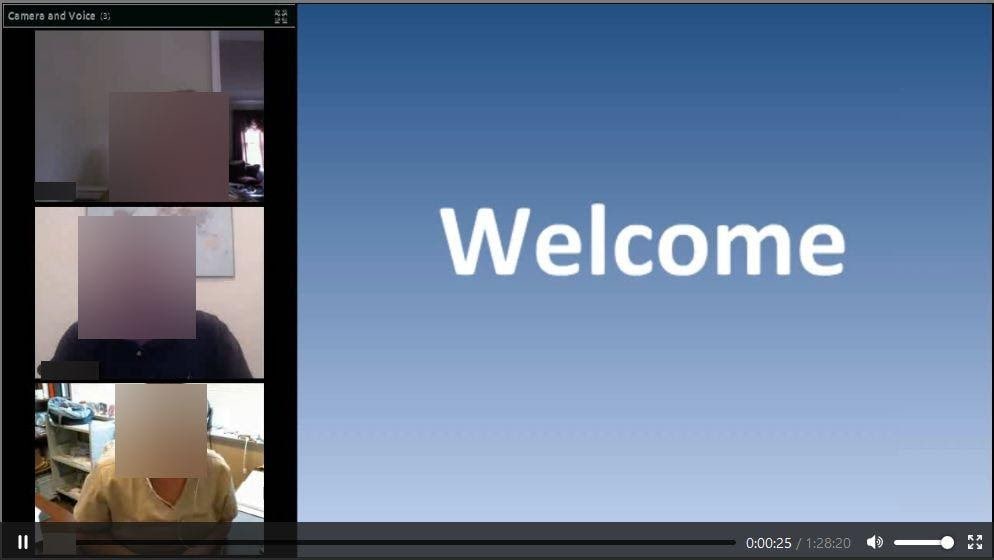
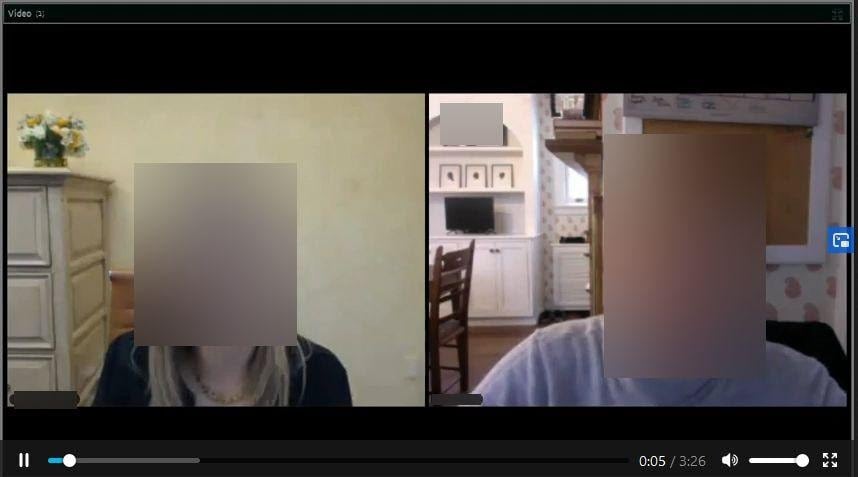
There are audio recordings of meetings stored on the bucket too. Audio recordings are the biggest collection of files on the bucket, though, we cannot confirm whether these files document the same meetings as those in video format.
Most of the audio transcripts stored on Civicom’s S3 bucket were created by Amazon Transcribe, an AWS service that automatically converts audio to text. Some transcriptions were also created using TrancriptionWing, a Civicom service. Transcriptions of meetings are few in number and were recently added to the bucket—every transcription was uploaded within two months of the date we discovered Civicom’s bucket.
While we can see evidence of supplementary technologies that Civicom’s clients used, such as AWS Transcribe, these technologies are in no way responsible for Civicom’s data exposure.
We can’t share screenshots of audio recordings for obvious reasons. However, you can see evidence of transcriptions in the following images.
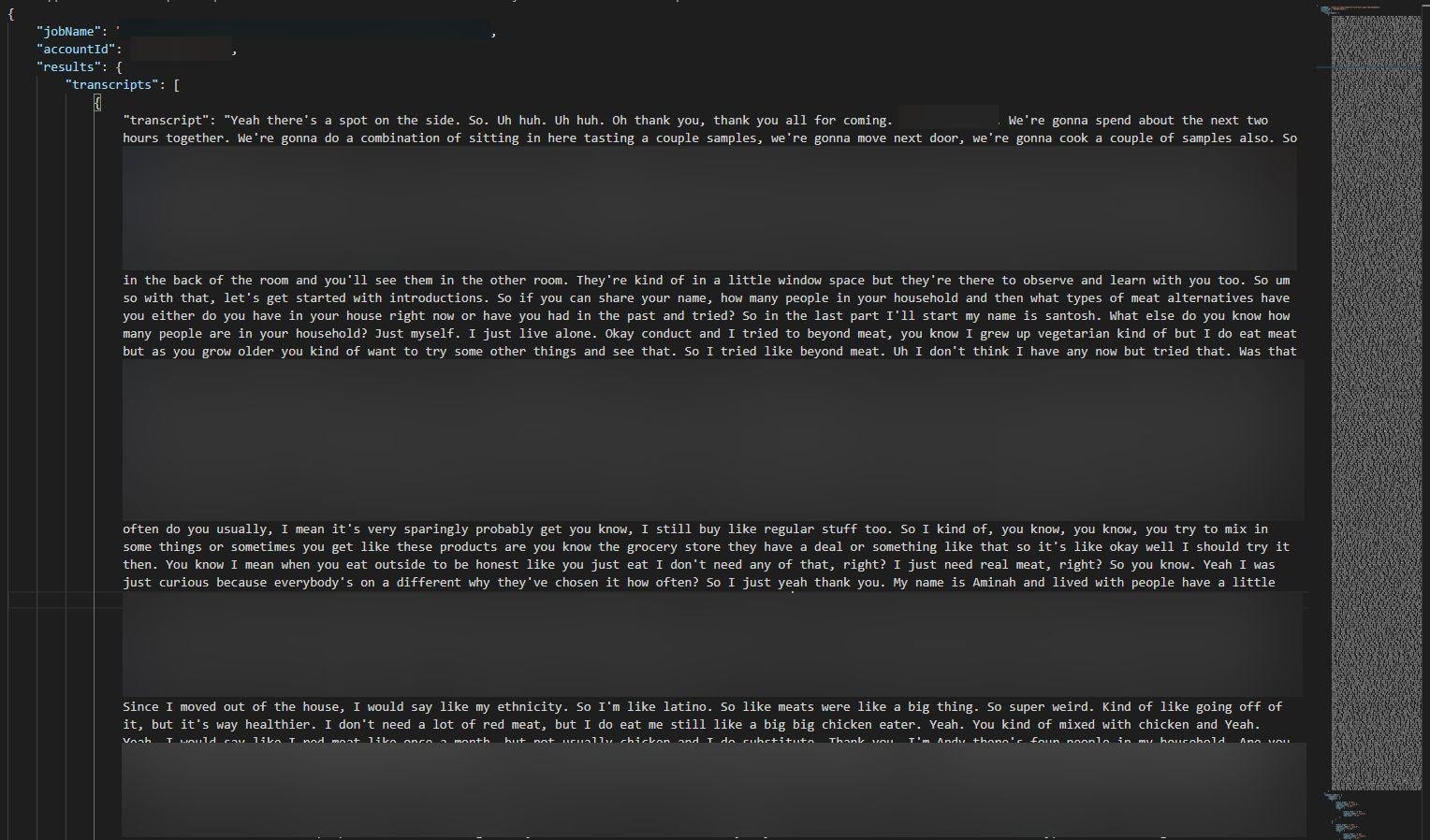

It’s difficult to estimate the exact number of businesses affected without examining tens of thousands of hours of content stored on the server. We did not analyze every file on the bucket for ethical reasons. As such, there may be numerous businesses with sensitive company data, business secrets, and intellectual properties discussed on the bucket.
Exposed businesses could face damaging consequences, while Civicom may come under legal scrutiny as a result of this data breach.
Who Was Affected
Civicom Inc. is a B2B company and, thus, businesses are affected by this data exposure rather than consumers. Some employees of client businesses using Civicom’s platform have been named and pictured among the server’s content as well, which could, again, come back to affect exposed businesses.
Users of Civicom’s “Glide Central” software are the primarily affected clients. We know this because the content of the server fits with the Audio and Video management software’s features, such as the Clip Key Points feature.
Civicom has clients in practically every industry imaginable, too, although much of the content we investigated mentioned health and legal topics. Other meetings involve various different business topics.
We suspect some US citizens may have been exposed on the server due to the presence of focus groups, surveys, and other meetings where businesses have contact with the general public. However, we cannot confirm this assumption.
Who is responsible for the breach?
Civicom Inc., founded in 2000, is an “other telecommunications” technology company that specializes in B2B video conferencing. Though Civicom provides a range of services, with its conferencing, collaboration, and webinar platforms supplemented by marketing research and administrative assistance services, and even a mobile travel app.
Popular services include Civicom Conferencing, Civicom Large Event Calls, Civicom Marketing Research Services, and TranscriptionWing.
Civicom has acquired several other companies over the last two decades. In 2012, Civicom merged with ConferTel, a webinar technology provider. The merger entered Civicom into the full-service, professionally managed webinar market.
Civicom Inc. employs over 200 people across 8 locations. The company is headquartered in New York City with additional offices throughout the United States, including Larchmont, NY; Newton, MA; Denver, CO; and San Diego, CA. Civicom has other locations across the world, including an office in London, England, and a Pacific branch with offices in Manilla and Cebu, in the Philippines.
Some of Civicom’s sister companies and services are also headquartered in Greenwich, Connecticut, USA.
Impact on End Users (if B2B)
We cannot and do not know whether malicious actors have gained access to the content of Civicom’s open AWS S3 bucket. However, bad actors may have found Civicom’s bucket.
In this case, there is a potential treasure trove of sensitive company data, industry secrets, and intellectual properties available to criminals and rival businesses. The content of the server suggests business espionage and sabotage is the number one risk factor for exposed Civicom clients.
Business Espionage & Sabotage
The content of the bucket may pose real problems for businesses. Rival businesses could acquire the content of the bucket from hackers or malicious actors. Rival businesses may be interested in learning more about exposed businesses to gain a competitive advantage.
Rival businesses could find out sensitive company data by watching leaked videos, listening to audio recordings, and reading transcripts of meetings. Highlight videos could give snoopers instant access to the most valuable snippets of company information and insight.
Many employees of client businesses have had their names and images exposed as well. A rival business could use these details, along with information representatives have learned about a competitor, to phish for more sensitive company data over the phone or via email. For example, someone from a rival business could ring an exposed business while posing as an employee, referencing the names of colleagues to build trust, and initiating a conversation about topics discussed in a meeting to unearth more sensitive information or industry secrets.
Based on the specifics of the information available, there are numerous ways rival businesses could use the bucket’s content to sabotage exposed users or gain an advantage. For example, rival businesses could undercut exposed businesses who discuss their deals with customers, or they could steal secrets found on the bucket and implement changes within their own business accordingly.
Impact on Civicom
Civicom Inc. could be subject to legal implications, while the company may face wider impacts as a result of this data breach
Data Privacy Violations
Civicom has exposed the sensitive information of countless businesses, along with the names and images of numerous employees from customer businesses. As an enterprise located in the USA which is primarily serving American clients, Civicom could come under the scrutiny of the Federal Trade Commission (FTC).
The FTC protects the sensitive and nonpublic data of US citizens and businesses. The FTC Act governs unfair or deceptive business acts or practices affecting commerce. Under Section 5 of the FTC Act, the maximum sanction for any transgression is a $100 million fine, along with imprisonment for guilty parties in serious cases.
Loss of Business
Civicom could experience a short-term loss of business following its data exposure. Some clients may choose to leave Civicom for an alternative service over concerns about their company’s data. Prospective customers might ultimately choose another provider for this reason too.
Competition Espionage
Other conferencing and telecom providers could access the content of Civicom’s bucket to find out about Civicom’s clients. Rival businesses could contact exposed clients with offers in an attempt to steal business away from Civicom.
Status of the Data Breach
We discovered the AWS S3 bucket on October 28th, 2021. On October 30th, 2021, we sent a message to Civicom regarding the company’s data exposure. We followed up on our initial message to Civicom on November 1st, 2021, while also sending messages to some new Civicom contacts. At that moment, we realized our emails were bouncing back and our email address appeared to be blocked. On November 15th, 2021, we emailed AWS regarding Civicom’s open bucket and received an auto-reply.
The bucket was finally secured on January 26th, 2022. A few days later we received an email from Civicom confirming they took care of the misconfiguration.
Reply from Civicom’s founder, Dave West:
“Since data security gets an enormous amount of time and attention in our company – see below – this horrified us. The issue was fixed immediately when we learned of it and fortunately an analysis of logs and data usage suggests that, besides the watchdog investigative reporter at Website Planet who thankfully took pains to avoid disclosing file details, there was no evidence that the S3 bucket was breached by bad actors while the vulnerability existed. And the issue was limited to only one of Civicom’s many services.
Our excellent team has made two additional security framework updates since last week to protect our clients’ data even further. For over ten years, every person in this company has spoken quarterly oaths of confidentiality and we have voluntarily engaged with external auditors to holistically ensure effective policies are being followed. We also have quarterly programmed-learning and annual security training for all employees. The recent penetration test of this service did not include the associated S3 bucket, but it will, going forward.”
Protecting Your Data
The primary threat faced by Civicom and its clients is business espionage and sabotage. While malicious parties could have collected sensitive company information stored on Civicom’s bucket, affected parties can mitigate the risk of losing information through targeted phishing attempts.
Organizations should educate staff about business espionage, phishing, and the importance of keeping sensitive data private unless speaking to a trusted source. Affected companies could establish systems that allow colleagues to authenticate themselves over the phone or via email. This way, employees would know for certain they are speaking to a trusted colleague and not a malicious actor.
Civicom (and companies in general) should check the security controls on any other cloud storage solutions it owns or that are within its control. Organizations should check the security of their databases at regular intervals.
How and Why We Report on Data Breaches
We want to help our readers stay safe when using any website or online product.
Unfortunately, most data breaches are never discovered or reported by the companies responsible. So, we decided to do the work and find the vulnerabilities putting people at risk.
We follow the principles of ethical hacking and stay within the law. We only investigate open, unprotected databases that we find randomly, and we never target specific companies.
By reporting these leaks, we hope to make the internet safer for everyone.
What is Website Planet?
Website Planet holds the top spot as the go-to resource for web designers, digital marketers, developers, and businesses with an online presence. Here, we provide tools and resources catering to individuals at all skill levels, from beginners to experts — and we uphold a steadfast commitment to honesty as our foremost principle.
We have an experienced team of ethical security research experts who uncover and disclose serious data leaks as part of a free service for the online community at large. This has included a breach in a medical AI platform, as well as a breach in a French real estate agency exposing sensitive data.
You can read about how we tested five popular web hosts to see how easily hackable they are here.