American Marriage Ministries (AMM) exposed PII and sensitive data belonging to marriage officiants and married couples.
| Company name and location | American Marriage Ministries (AMM), based in the US |
| Size of the breach | Almost 630 GB of data, over 715,000 files |
| Data storage format | AWS S3 bucket |
| Countries affected | The United States |
| Exposed data |
|
| Date range of files | March 31st, 2018, to April 2022 |
| How many people could be affected? | Around 185,000 officiants and roughly 15,000 married couples (and their wedding guests).
Our estimation is based on the number of unique officiants’ documents and pictures. |
The Website Planet research team discovered a data exposure affecting American Marriage Ministries (AMM), a non-profit constitutional church.
American Marriage Ministries provides ministers with free ordination, advocacy, and training to become fully-fledged marriage officiants. According to AMM’s website, the organization has ordained over 900,000 ministers throughout the United States since it was founded in 2009.
American Marriage Ministries’ Amazon bucket was left unsecured, without any password protection or encryption controls in place. The organization’s bucket has therefore exposed the PII and sensitive data of ministers, married couples, and various wedding guests.
We know the bucket belongs to AMM because the organization’s logos appear on numerous files. Amazon is not responsible for the misconfiguration of AMM’s open bucket.
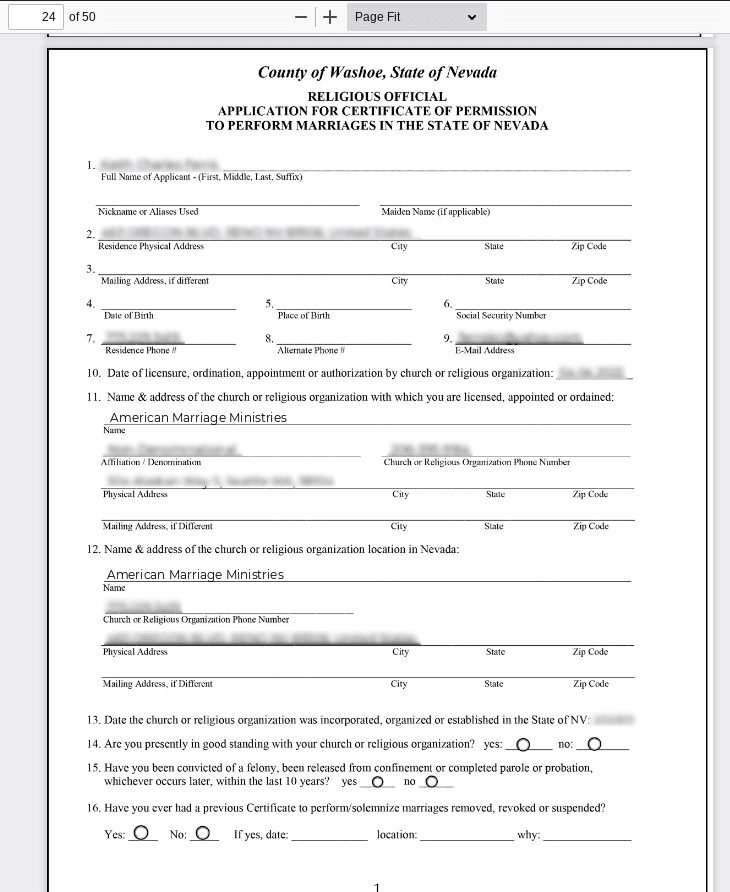
Exposed files include ministers’ program application forms, over 500,000 ordination certificates and minister identification documents, and marriage licenses that contain details about newly-wedded couples.
The bucket also contained more than 140,000 pictures of ministers, couples, and guests at wedding ceremonies.
While we cannot and do not know whether hackers found the data, AMM’s open bucket may violate people’s privacy and could facilitate phishing attacks in the wrong hands.
You can see examples of ministers’ information and a married couple’s data in the screenshots below.

Exposure Timeline
| When did we find AMM’s data? | April 26th, 2022 |
| Who did we contact to close the breach? | AMM and US Cert |
| When did we responsibly disclose the breach? | After initial contact, we responsibly disclosed the breach to AMM on April 29th, 2022. |
| What did they say? | In follow-up messages, a representative from AMM told us that they were trying to fix the issue |
| When was the breach secured? | May 11th, 2022 |
Response from AMM’s Executive Director:
“AMM appreciates WebsitePlanet’s bringing this matter to our attention, and moved quickly to investigate their report. The bucket in question was intended to be public, however a specific folder within the bucket which contained minister addresses and emails was sealed off after correspondence with WebsitePlanet. The other documents and images were intentionally public, and most are uploaded by our ministers to their public profiles. Our website contains a social feature that allows ministers to upload photos and other details about weddings that they officiate including couples names, venues, and other relevant details. AMM doesn’t actively moderate all of the photos uploaded to our site, and we allow our ministers to upload images for general viewing at their discretion.
How and Why We Report on Data Breaches
We want to help our readers stay safe when using any website or online product.
Unfortunately, most data breaches are never discovered or reported by the companies responsible. So, we decided to do the work and find the vulnerabilities putting people at risk.
We follow the principles of ethical hacking and stay within the law. We only investigate open, unprotected databases that we find randomly, and we never target specific companies.
By reporting these leaks, we hope to make the internet safer for everyone.
What is Website Planet?
Website Planet holds the top position as the primary resource for web designers, digital marketers, developers, and businesses with an online presence. We provide tools and resources catering to everyone, from beginners to experts, all while maintaining a steadfast commitment to honesty.
We have an experienced team of ethical security research experts who uncover and disclose serious data leaks as part of a free service for the online community at large. This has included a breach affecting a famous US news network, as well as an incident that exposed website traffic for millions of internet users.
You can read about how we tested five popular web hosts to see how easily hackable they are here.